by Tayo Ogunseyinde and Maksym Dmitriiev
Introduction
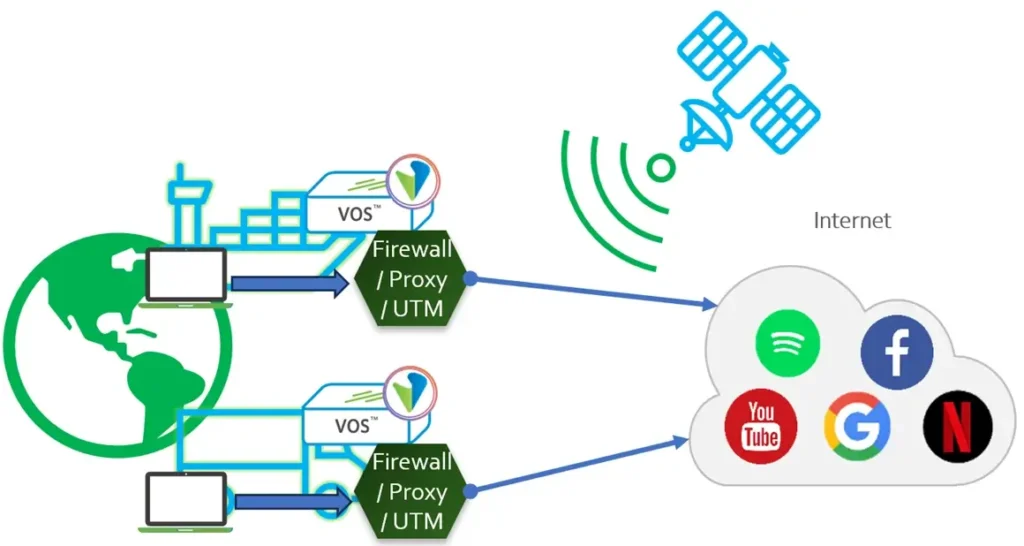 Figure 1 Solution Overview
Below are general guidelines of implemented security rules. It does not represent customer specific applications, network segments and zones. Further augmentation of customer specific rules should be considered to ensure tailored protection taking into account the unique aspects of the environment and data patterns.
Figure 1 Solution Overview
Below are general guidelines of implemented security rules. It does not represent customer specific applications, network segments and zones. Further augmentation of customer specific rules should be considered to ensure tailored protection taking into account the unique aspects of the environment and data patterns.
Introduction
This article presents a production case study of Cisco Umbrella Cloud based security replacement with Versa VOS (Versa Operation System) on-prem security options for a major customer in the maritime sector. It will detail customer motivation, Versa benefits, technical recommendations and conclude with practical highlights of additional achievements that became available with VOS security stack.Motivation & Benefits
The customer requirement is driven by the following reasons.- Bandwidth savings – Low bandwidth in the satellite environment is always a consideration. Therefore, the customer was looking for opportunities to limit that amount of upload bandwidth consumed while sending sanctioned traffic to the Cisco Umbrella cloud security system only to be dropped. The Versa on-prem security can enforce the security at the edge, thus avoiding unnecessary bandwidth consumption. The customer also takes advantage of other bandwidth saving features of the Versa SDWAN edge such as DNS caching.
- Improved user experience (Optimized Latency) – Instant policy enforcement at the edge reduces response time to the user when access is denied. In a satellite environment where RTT could be up to ~ 1000ms this is a significant improvement to the user experience.
- Cost Savings via consolidation – The Versa VOS is a single piece of software that provides Routing, SDWAN and Security functions at the edge. As the Cisco Umbrella service came up for a renewal customer took the opportunity to consolidate by enabling the security service on their existing Versa VOS edge appliances. The customer also benefits from additional simplification of the edge network by removing layers network and security components.
- Improve Security between LAN Segments – Prevent lateral movement within the network, limiting the spread of potential threats or unauthorized access from one zone to another. This is important in mitigating potential data breaches.
- Consolidated Analytics – The Versa solution can provide single pane of glass view of both their Network and Security analytics. This correlated view improves operational efficiency (particularly during troubleshooting) while allowing the customer to generate meaningful insight into how the network is used.
Implementation
Using the Versa robust Next Generation firewall module, the customer has successfully implemented a powerful combination of security policies to strengthen their network perimeter, protect sensitive data, mitigate emerging threats, and ensure compliance with defined architecture standards. This implementation also includes features such as captive portal, deep traffic inspection with SSL decryption, and micro segmentation, which collectively provide greater control over policy enforcement and offer enhanced visibility into data flows. With these advanced capabilities, the customer can confidently safeguard their network and maintain a secure environment. Figure 1 Solution Overview
Below are general guidelines of implemented security rules. It does not represent customer specific applications, network segments and zones. Further augmentation of customer specific rules should be considered to ensure tailored protection taking into account the unique aspects of the environment and data patterns.
Figure 1 Solution Overview
Below are general guidelines of implemented security rules. It does not represent customer specific applications, network segments and zones. Further augmentation of customer specific rules should be considered to ensure tailored protection taking into account the unique aspects of the environment and data patterns.
- Block QUIC – QUIC was developed to improve performance of connection-oriented protocol such as TCP, it presents challenges when it comes to inspecting traffic for potential threats. Organization that needs a granular control of user and application traffic over the network to enforce its security inspection techniques should consider blocking QUIC. However, with Versa solution, you have flexibility to selectively allow QUIC for specific network segments where its benefits outweigh the associated constrains. One example is a guest network where organization does not need to enforce deep security analysis.
- DNS proxy enabled along with NGFW rule to allow only authorized DNS destinations. This will enforce DNS requests control and minimize data leakage or security policy bypass using DNS tunnelling techniques.
- DNS packet inspection with IP and URL filtering. Connection will be prevented for common malicious or destinations with bad reputation early at DNS level.
- URL & IP filtering. Customer-defined restrictions based on well-known categories and reputations as well as created custom list of destinations.
- Prevent unauthorized VPN connections from internal network. Using Versa Analytics data, the administrator can identify unauthorized connections. The analysis of applications, URLs, destination IPs and port numbers allowed administrator to build additional custom policies which blocked unsanctioned from bypassing defined security policies. It significantly improved control and security enforcement of standard categories blockage such as Malware, Parked Domains, Dead Sites, Proxy etc, where the traffic can be evasive.
- Security policy refinement. Leveraging Versa Analytics data and user experience security lifecycle policies were regularly reviewed and refined, incorporating both allow and block exceptions, to enhance business security shield and reduce the occurrence of false positives.
- Captive portal implementation to inform user of unauthorized access blocked or potential threat.
- Deep malware inspections might be considered leveraging Versa Antivirus and IPS modules.
Service Migration to Versa Security
To ensure minimal impact to availability and user experience during the service migration from Cisco Umbrella to Versa security, it is crucial to follow a well-defined plan consisting of three phases: planning, execution, and validation. The planning phase involves thorough analysis and preparation. This includes understanding the current configuration of Cisco Umbrella and mapping it to the desired configuration in Versa Os Security. The outcome results in reflecting existing security posture within Versa VOS configuration format. Next step within the planning phase was security posture strengthening. It has been achieved by rectifying existing and adding more policies based on the previous experience. During the execution phase, the migration process takes place. This involves deploying and configuring the Versa security solution, including the necessary policies, rules, and access controls. It is imperative to ensure a seamless transition by conducting a pilot deployment in a controlled environment to identify and resolve any issues before implementing the solution across the entire network. Versa Analytics and end user feedback were taken into account in order to fine tune security policies according to customer traffic patterns and daily employee activities. This phase also includes migrating data and configurations from Cisco Umbrella to Versa security, ensuring a smooth transfer of settings and policies. Once the migration is complete, the validation phase begins. This phase focuses on verifying the functionality and performance of the newly implemented Versa security solution. Robust testing procedures were be conducted to ensure that all security measures are working as intended and that there are no disruptions to availability or user experience. This is a continuous process of security lifecycle to monitor and dynamically respond to security events within the production environment.Conclusions
Using Versa on-prem NGFW customer could incorporate all Cisco Umbrella security features directly on WAN Edge. It has proved to be highly beneficial for the customer, as it has addressed some limitations that the customer reported with the previous solution such as:- Ability to block unauthorized VPN applications that end user could use to bypass defined security standards.
- Ability to block custom ports and other unauthorized connections based on L3/L4 information.
- Ability to block connections based on application recognition module as well as whitelist approved applications.





