This article will present a short and concise way of configuring Lateral Movement Detection feature
Background
What is Lateral movement ? and why it is relevant? and how it works? and how an Administrator can configure Versa Appliance to detect Lateral Movements attacks.
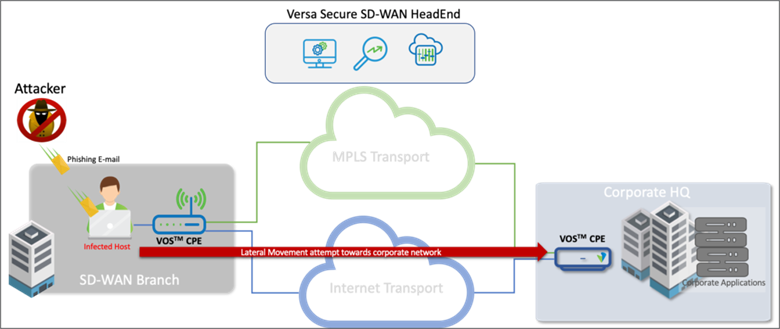
Lateral Movement tries to detect what’s called the post-exploitation technique. Attackers may not have immediate access to high profile targets like domain controller or database behind private network. Hence in most scenarios, attackers would seek to gain a foothold on a relatively easy target on the network such as a user machine and then from there they try to propagate and all these techniques that they use to propagate within the network are called “Lateral Movement techniques”
Spear-phishing is very common on the internet these days and it has been the de-facto methodology of the attackers for the past 10yrs. The attackers would launch a spear-phishing attack to find the entry point for the network.
For example, let’s say the attacker is after abc.com. So first step for the attacker is to find out the quickest way to implant the malicious payload on an easy target; best to send a clickbait email. The attacker would now look for email addresses that exist on abc.com. Once the list of email addresses is obtained the attacker would prepare an email crafted that would entice users to open up a document or click on the link inside that email. Most of the cases the attacker would find its victim from the list who would fall for the trick and clicks the bait. That’s when the attacker establishes the foothold. Once an attacker has a foothold or access to an internal machine, the attacker can study the network and domain to identify domain accounts and computers. Attackers could use credentials harvesting tools like mimikatz.
So detecting the lateral movement is more like accepting the fact that infiltration can happen anytime. Detecting lateral movement ensures any malicious code that got into the network is detected, contained, and not allowed propagate further.
Few Facts
- With the help of basic hacking mechanisms like Footprinting/Recon/Spear-phishing attackers have already got the way to access victim machine who happens to be residing in one of the remote spoke sites.
- The attacker would have sent a Spear-Phishing email or email with some virus affected document attached which victim has unintentionally clicked it and got affected.
- Post that phase the attacker gained access to a Victim machine and that’s when the attacker will try to execute further attacks against organization resources; this is where lateral movement detection will play its part and protect those resources access from Attacker.
☞ It is assumed that an Administrator following this article is aware of basic Firewall policies/rules configurations using Versa Director and latest security pack is installed on the VOS.
Configuration Steps
Step 1: Firewall rule creation
Create a firewall rule for Lateral Movement detection. The configuration can be done either through templates or on a specific device. The screenshot below shows firewall rule creation on a specific CPE.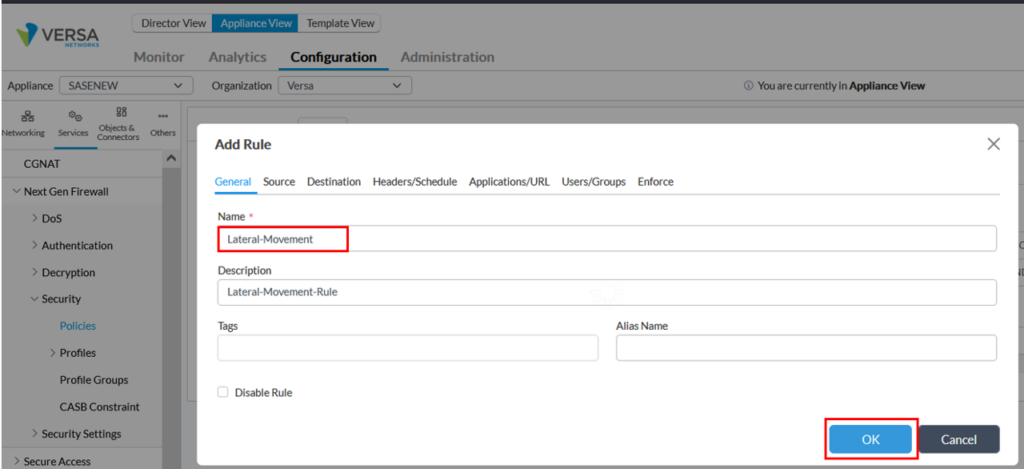
Step 2: Identify Source and Destination zones as per the topology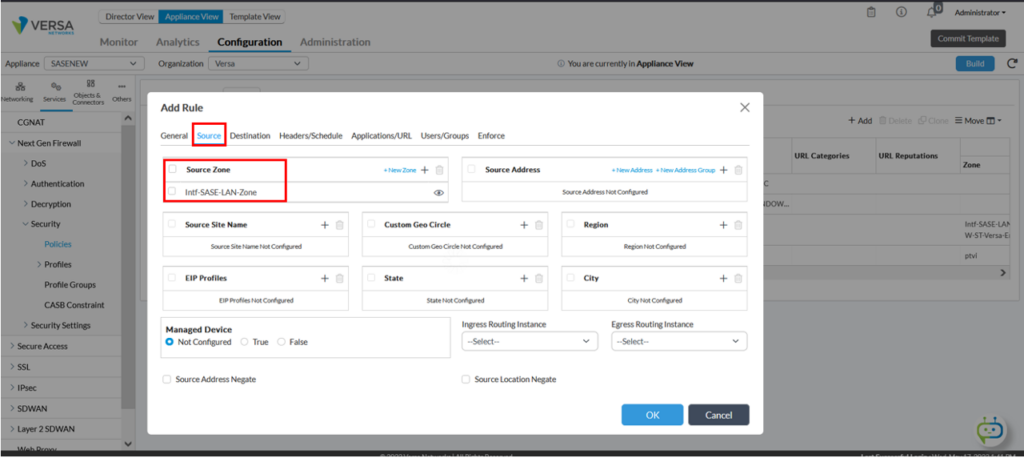
Step 3 : Applying Lateral Movement Detection profile
Select “Apply Security Profile” under the Enforce tab and then enable “Vulnerability” checkbox. From the dropdown menu select Versa pre-defined “Lateral Movement Detection”. 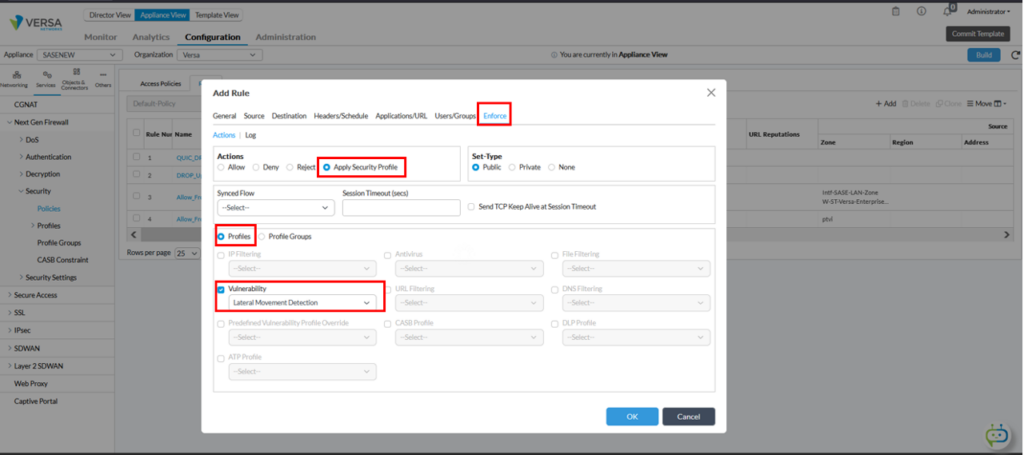
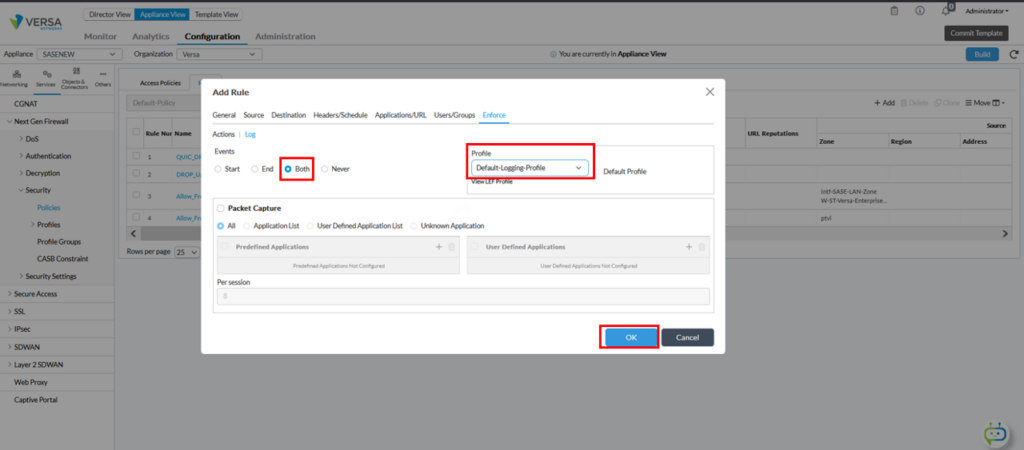
In order to log events in Analytics select “Default-Logging-Profile” in Log Tab next to Actions.
Verification
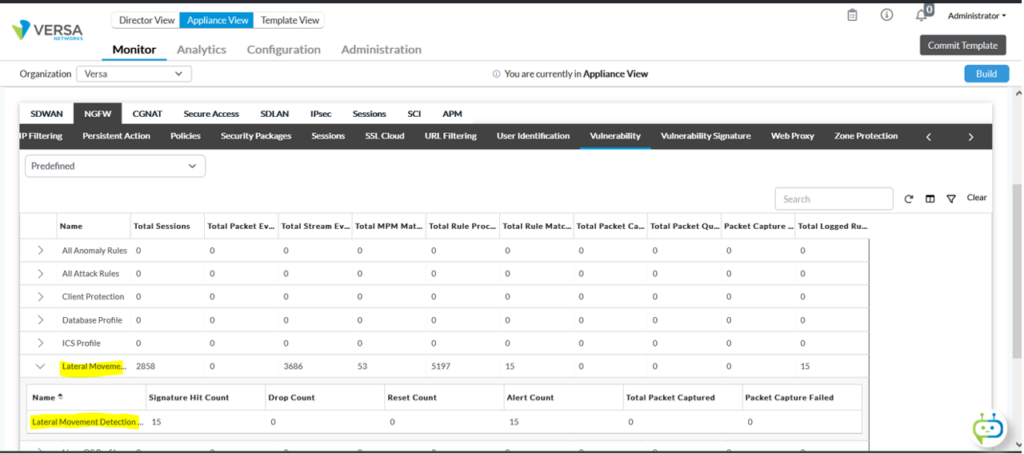
Versa Analytics provides provides incidents logs with details for any forensics and analysis
Analytics -> Logs ->Threat Detection -> IDP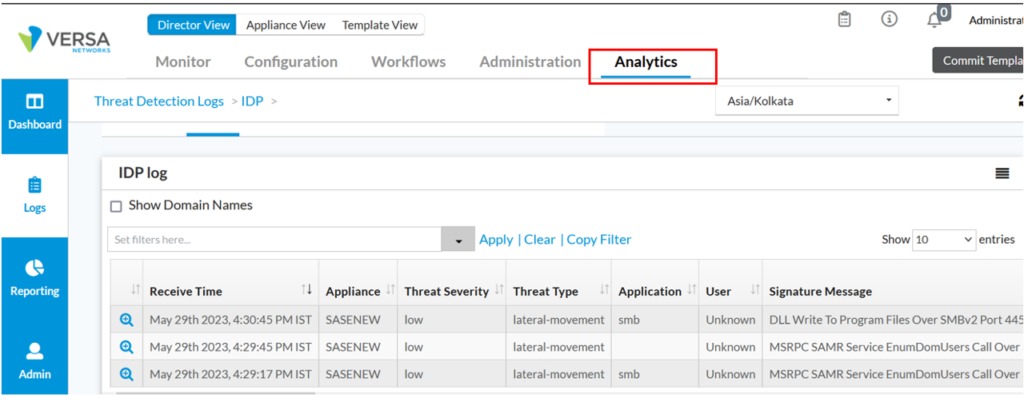
Expand the logs for more details.
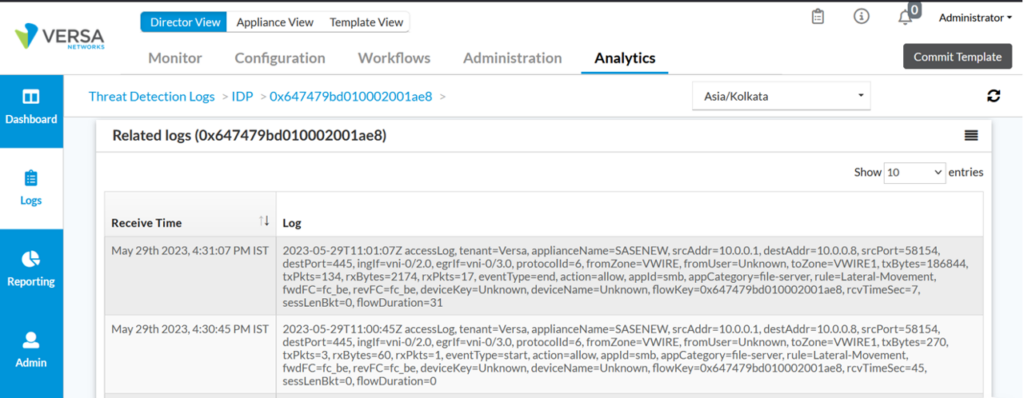
In Device-Monitor-> NGFW -> Vulnerability