IPS/IDS profile configuration and verifications
This article will show how to enable and verify IPS/IDS operations while using Versa Recommended profile on VOS™ CPEs. Before explaining the configuration its important to understand some commonly used terminologies and their details. Table below details some common terminologies
Some commonly used IPS/IDS terminologies
| Term | Description |
| True Positives | A legitimate attack which triggers to produce an alarm. Example: You have a brute force alert, and it triggers. You investigate the alert and find out that somebody was indeed trying to break into one of your systems via brute force methods. |
| True Negative | An event when no attack has taken place and no detection is made. No attack occurred and your rule didn’t fire. |
| False Positive | IDS classified BENIGN packet as malicious. An event signaling to produce an alarm when no attack has taken place. Example: You investigate another of these brute force alerts, and find out that it was just some users who mistypes their password a bunch of times, not a real attack. |
| False Negative | IDS classified MALICIOUS packet as benign. When no alarm is raised when an attack has taken place. Example: There actually was someone trying to break into your system, but they did so below the threshold of your brute force attack logic. For example, you set your rule to look for 10 failed logins in a minute, and the attacker did only 9. The attack occurred, but your rule failed to detect it. |
| CVE | CVE stands for Common Vulnerability Enumeration, which is a dictionary of publicly known information security vulnerabilities and exposures. |
| CVSSl | CVSS stands for “Common Vulnerability Scoring System”, which provides a score to indicate the severity of the CVE vulnerabilities. |
| Confidence | Versa recommends using a “Higher” value against the Confidence parameter. Every signature can potentially catch “True positive” (malicious traffic) and trigger “False positive” (benign traffic incorrectly get identified as malicious traffic). Every signature has a “confidence” field. The higher the value, the more confident we are that this signature will only catch “True positive” and not trigger “False positive” |
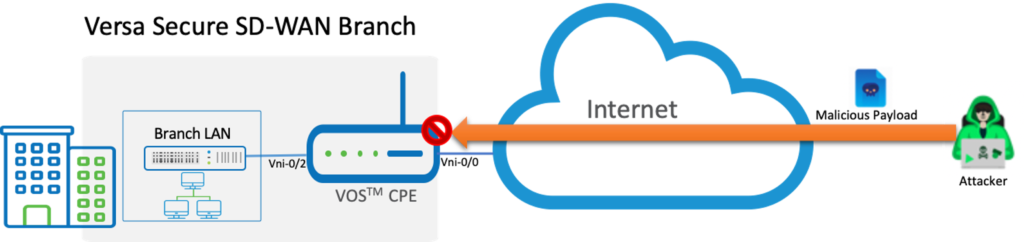
Network Topology
Enabling Versa Recommended IPS/IDS Profile
Step 1 : Go to Configuration --> Services --> Next Gen Firewall --> Security --> Policies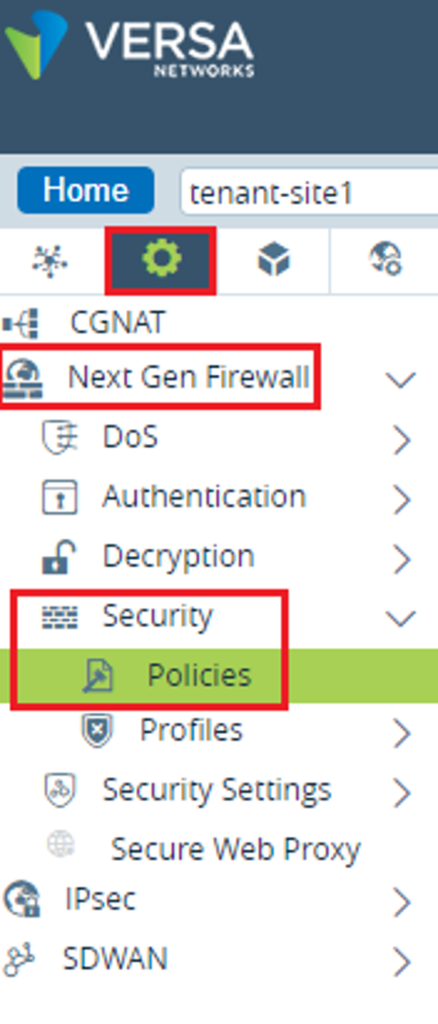
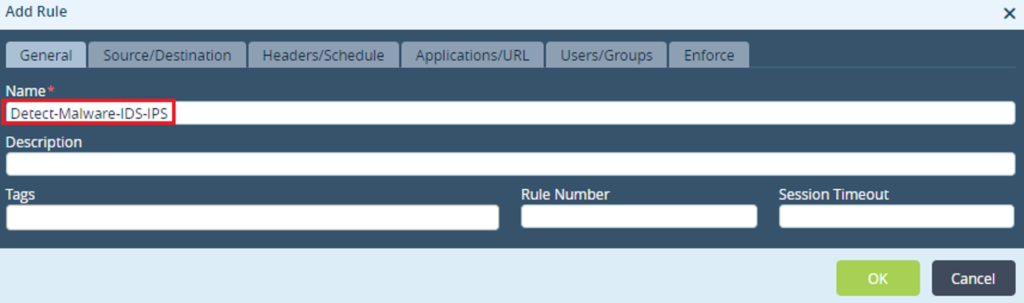
Step 2: Provide a name for the rule
Step 3: Specify Source/Destination zone per topology requirement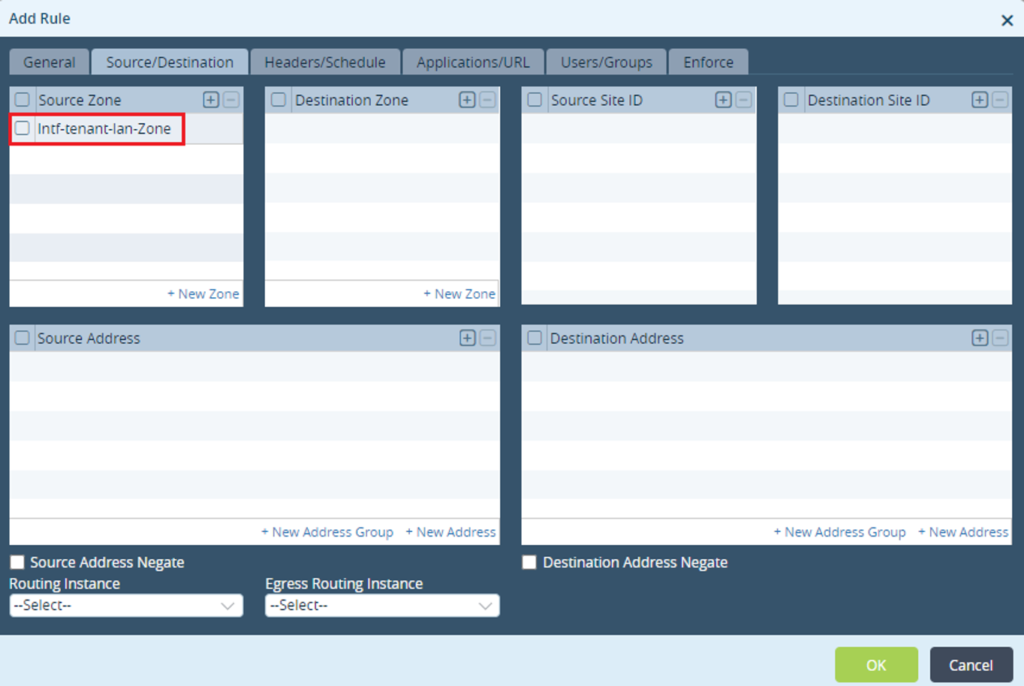
Step 4: -While in enforce tab, select "Apply Security Profile" checkbox-Against Vulnerability dropdown choose "Versa Recommended Profile"- Click "OK"
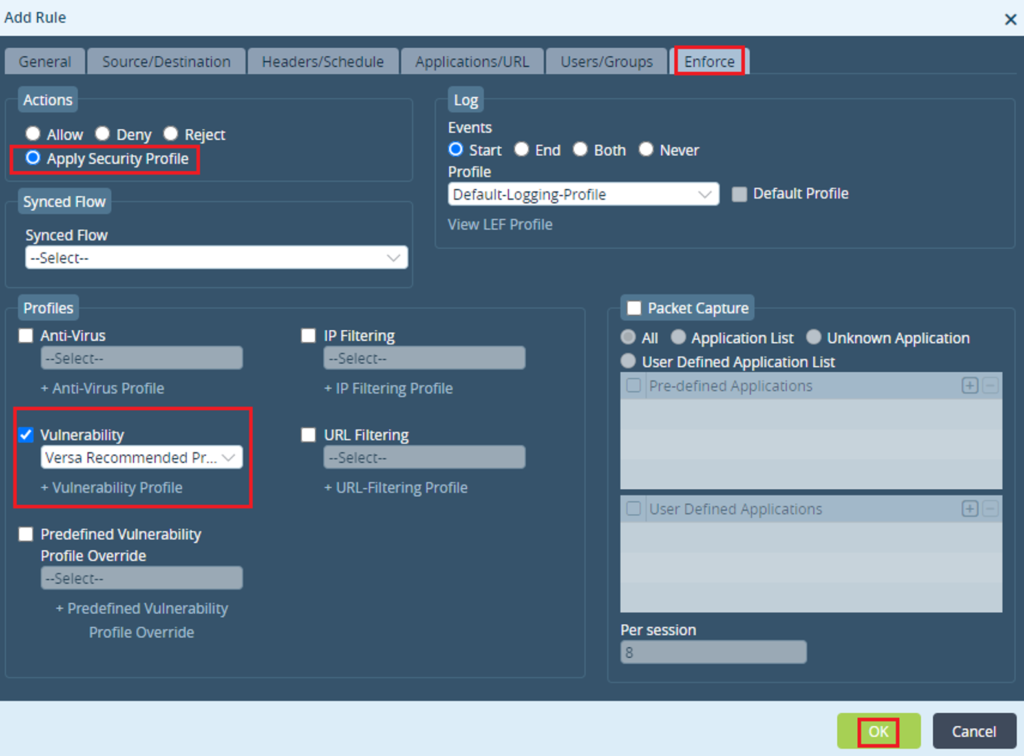
Verifications
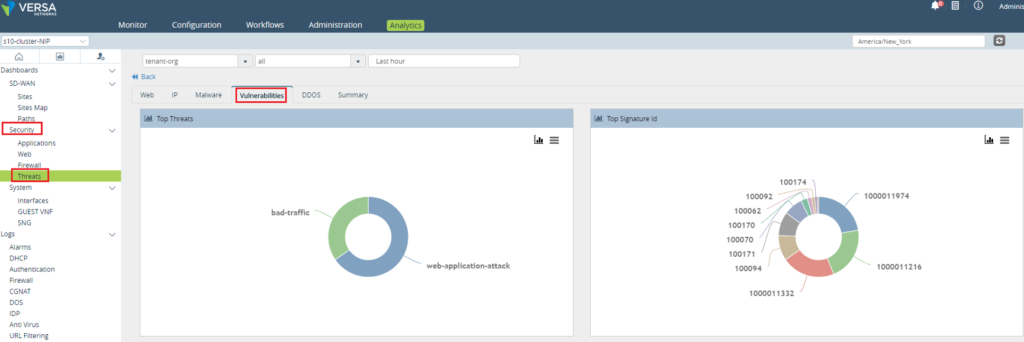
IPS/IDS logs are captured in the Analytics Logs section as shown below. The image below shows last 30 mins IPS/IDS logs for a tenant named “tenant-org”
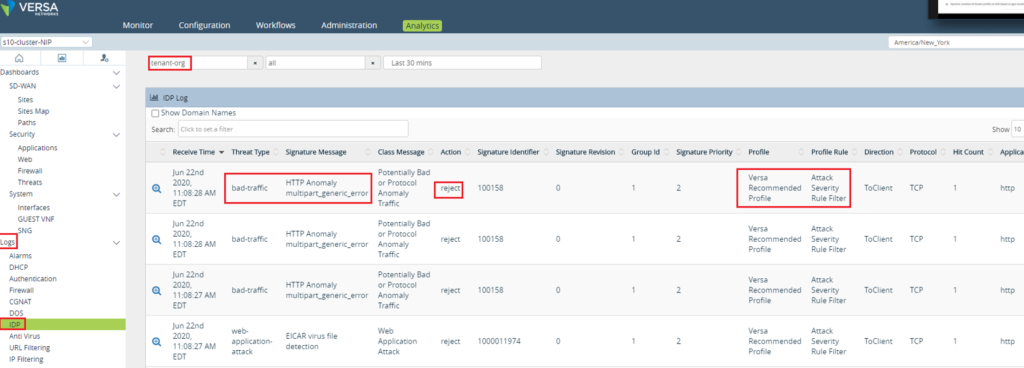
To view identified vulnerabilities, navigate to Security –> Threats –> vulnerabilities section in the Analytics