IPsec VPN between Versa SD-WAN CPE and Cisco Routers
This article will showcase how to create Site to Site IPSEC Tunnel between a VOS SD-WAN CPE and a Cisco router. The procedure mentioned in this document was tested on VOS™ 20.2 Release
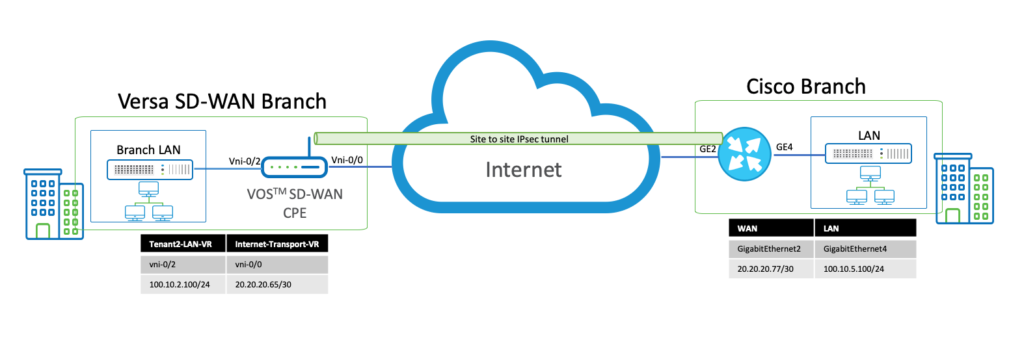
Topology
Configurations presented in this document are based on the following topology.
Configuration objectives
- Build IKE v1 site-to-site tunnel between SD-WAN Branch1 and Cisco Router
- Pre-shared key and IP address for peer authentication
- Cisco IPsec configuration
- Verification
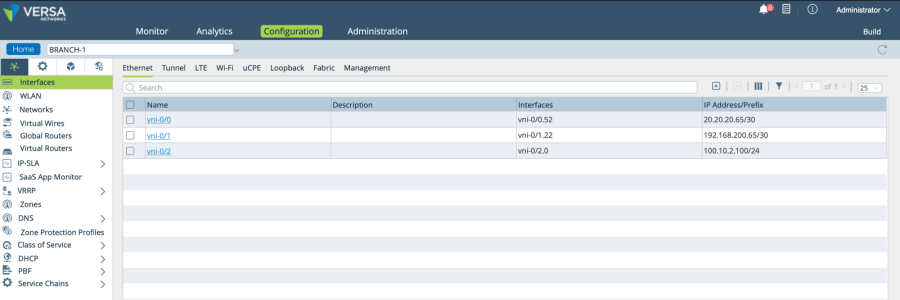
WAN and LAN configuration in Versa CPE.
The screenshot below shows the interface configurations that are present in Versa SD-WAN CPE
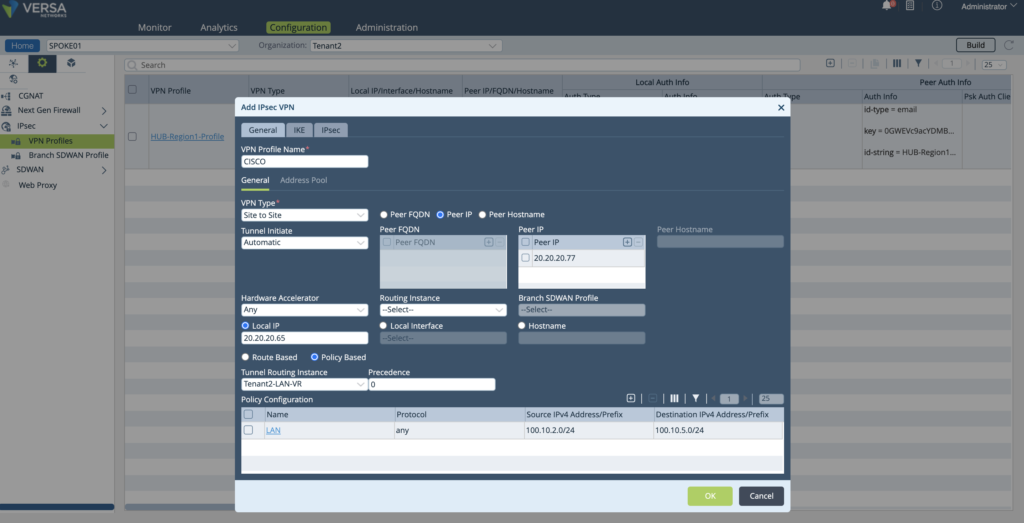
VPN profile configuration using Versa Director
To configure VPN profile, navigate correct template or appliance and then new VPN profile
Services > IPsec > VPN Profiles > Add by clicking ![]() sign on top right
sign on top right
IKE related parameters to be added in IKE tab as shown below
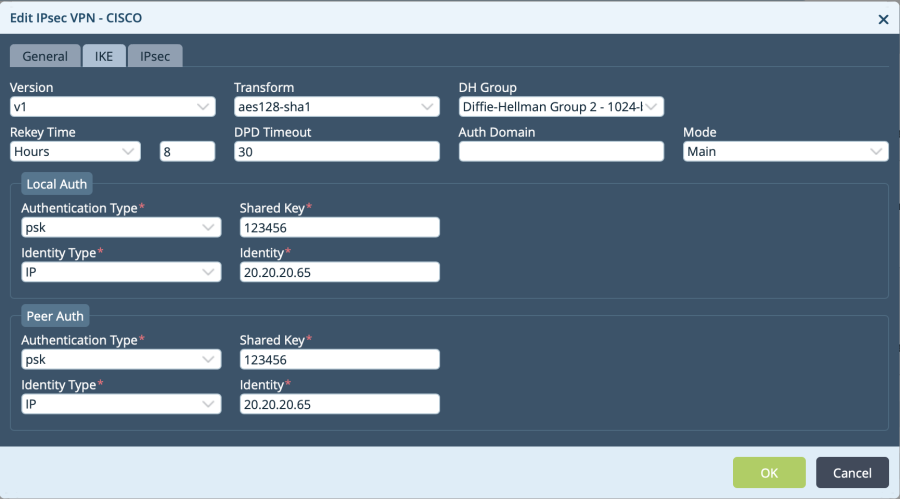
IPsec parameters to be added in IPsec tab
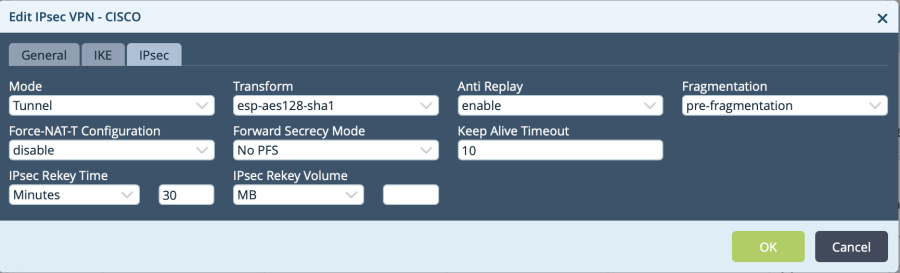
Configuration as seen using CLI
\\ set orgs org-services ISP ipsec vpn-profile CISCO vpn-type site-to-site set orgs org-services ISP ipsec vpn-profile CISCO local-auth-info set orgs org-services ISP ipsec vpn-profile CISCO local-auth-info auth-type psk set orgs org-services ISP ipsec vpn-profile CISCO local-auth-info id-type ip set orgs org-services ISP ipsec vpn-profile CISCO local-auth-info key 123456 set orgs org-services ISP ipsec vpn-profile CISCO local-auth-info id-string 20.20.20.65 set orgs org-services ISP ipsec vpn-profile CISCO local set orgs org-services ISP ipsec vpn-profile CISCO local address 20.20.20.65 set orgs org-services ISP ipsec vpn-profile CISCO routing-instance INTERNET-Transport-VR set orgs org-services ISP ipsec vpn-profile CISCO tunnel-routing-instance Tenant2-LAN-VR set orgs org-services ISP ipsec vpn-profile CISCO tunnel-initiate automatic \\ set orgs org-services ISP ipsec vpn-profile CISCO ipsec fragmentation pre-fragmentation set orgs org-services ISP ipsec vpn-profile CISCO ipsec force-nat-t disable set orgs org-services ISP ipsec vpn-profile CISCO ipsec transform esp-aes128-sha1 set orgs org-services ISP ipsec vpn-profile CISCO ipsec mode tunnel set orgs org-services ISP ipsec vpn-profile CISCO ipsec pfs-group mod-none set orgs org-services ISP ipsec vpn-profile CISCO ipsec anti-replay enable set orgs org-services ISP ipsec vpn-profile CISCO ipsec life duration 1800 \\ set orgs org-services ISP ipsec vpn-profile CISCO ike version v1 set orgs org-services ISP ipsec vpn-profile CISCO ike mode main set orgs org-services ISP ipsec vpn-profile CISCO ike group mod2 set orgs org-services ISP ipsec vpn-profile CISCO ike transform aes128-sha1 set orgs org-services ISP ipsec vpn-profile CISCO ike lifetime 28800 set orgs org-services ISP ipsec vpn-profile CISCO ike dpd-timeout 30 \\ set orgs org-services ISP ipsec vpn-profile CISCO peer-auth-info set orgs org-services ISP ipsec vpn-profile CISCO peer-auth-info auth-type psk set orgs org-services ISP ipsec vpn-profile CISCO peer-auth-info id-type ip set orgs org-services ISP ipsec vpn-profile CISCO peer-auth-info key 123456 set orgs org-services ISP ipsec vpn-profile CISCO peer-auth-info id-string 20.20.20.65 set orgs org-services ISP ipsec vpn-profile CISCO peer set orgs org-services ISP ipsec vpn-profile CISCO peer address \[ 20.20.20.77 \] set orgs org-services ISP ipsec vpn-profile CISCO hardware-accelerator any set orgs org-services ISP ipsec vpn-profile CISCO rule LAN protocol any set orgs org-services ISP ipsec vpn-profile CISCO rule LAN src inet 100.10.2.0/24 set orgs org-services ISP ipsec vpn-profile CISCO rule LAN src port 0 set orgs org-services ISP ipsec vpn-profile CISCO rule LAN dst inet 100.10.5.0/24 set orgs org-services ISP ipsec vpn-profile CISCO rule LAN dst port 0 \\
Cisco Configuration [ VPN only configuration shown]
crypto isakmp policy 1encr aesauthentication pre-sharegroup 2lifetime 28800crypto isakmp key 123456address 20.20.20.65crypto ipsec transform-set MYSET esp-aes esp-sha-hmacmode tunnelcrypto map MYTUNNEL 1ipsec-isakmpset peer 20.20.20.65set security-association lifetime seconds 1800set transform-set MYSETmatch address 100access-list 100permit ip 100.10.5.00.0.0.255100.10.2.00.0.0.255interfaceGigabitEthernet2ip address 20.20.20.77255.255.255.252negotiation autocrypto map MYTUNNEL
Verification Logs
To validate the tunnel status navigate to Monitor tab in versa director and choose the right CPE. IPsec tunnel status can be seen under Services>IPSEC as shown below.
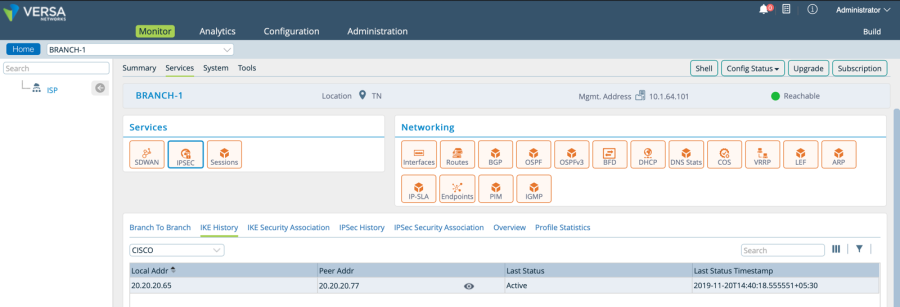
Verification on Cisco Router
CISCO-Br#show crypto isakmp saIPv4 Crypto ISAKMP SAdst src state conn-id status20.20.20.7720.20.20.65QM_IDLE 1023ACTIVEIPv6 Crypto ISAKMP SA#CISCO-Br#show crypto session detailCISCO-BrCrypto session current statusCode: C - IKE Configuration mode, D - Dead Peer DetectionK - Keepalives, N - NAT-traversal, T - cTCP encapsulationX - IKE Extended Authentication, F - IKE FragmentationR - IKE Auto ReconnectInterface: GigabitEthernet2Uptime: 6d19hSession status: UP-ACTIVEPeer: 20.20.20.65port 500fvrf: (none) ivrf: (none)Phase1_id: 20.20.20.65Desc: (none)Session ID: 0IKEv1 SA: local 20.20.20.77/500remote 20.20.20.65/500ActiveCapabilities:(none) connid:1023lifetime:05:42:15IPSEC FLOW: permit ip 100.10.5.0/255.255.255.0100.10.2.0/255.255.255.0Active SAs: 2, origin: crypto mapInbound: #pkts dec'ed 3715drop 0life (KB/Sec) 4607998/250Outbound: #pkts enc'ed 3719drop 0life (KB/Sec) 4607999/250CISCO-Br#show crypto ipsec sainterface: GigabitEthernet2Crypto map tag: MYTUNNEL, local addr 20.20.20.77protectedvrf: (none)local ident (addr/mask/prot/port): (100.10.5.0/255.255.255.0/0/0)remote ident (addr/mask/prot/port): (100.10.2.0/255.255.255.0/0/0)current_peer 20.20.20.65port 500PERMIT, flags={origin_is_acl,}#pkts encaps: 3719, #pkts encrypt: 3719, #pkts digest: 3719#pkts decaps: 3715, #pkts decrypt: 3715, #pkts verify: 3715#pkts compressed: 0, #pkts decompressed: 0#pkts not compressed: 0, #pkts compr. failed: 0#pkts not decompressed: 0, #pkts decompress failed: 0#send errors 0, #recv errors 0local crypto endpt.: 20.20.20.77, remote crypto endpt.: 20.20.20.65plaintext mtu 1438, path mtu 1500, ip mtu 1500, ip mtu idb GigabitEthernet2current outbound spi: 0x2006F97(33582999)PFS (Y/N): N, DH group: noneinbound esp sas:spi: 0xB35C201(188072449)transform: esp-aes esp-sha-hmac ,in use settings ={Tunnel, }conn id: 2779, flow_id: CSR:779, sibling_flags FFFFFFFF80000048, crypto map: MYTUNNELsa timing: remaining key lifetime (k/sec): (4607998/229)IV size: 16bytesreplay detection support: Yecn bit support: N status: offStatus: ACTIVE(ACTIVE)inbound ah sas:inbound pcp sas:outbound esp sas:spi: 0x2006F97(33582999)transform: esp-aes esp-sha-hmac ,in use settings ={Tunnel, }conn id: 2780, flow_id: CSR:780, sibling_flags FFFFFFFF80000048, crypto map: MYTUNNELsa timing: remaining key lifetime (k/sec): (4607999/229)IV size: 16bytesreplay detection support: Yecn bit support: N status: offStatus: ACTIVE(ACTIVE)outbound ah sas:outbound pcp sas:CISCO-Br#
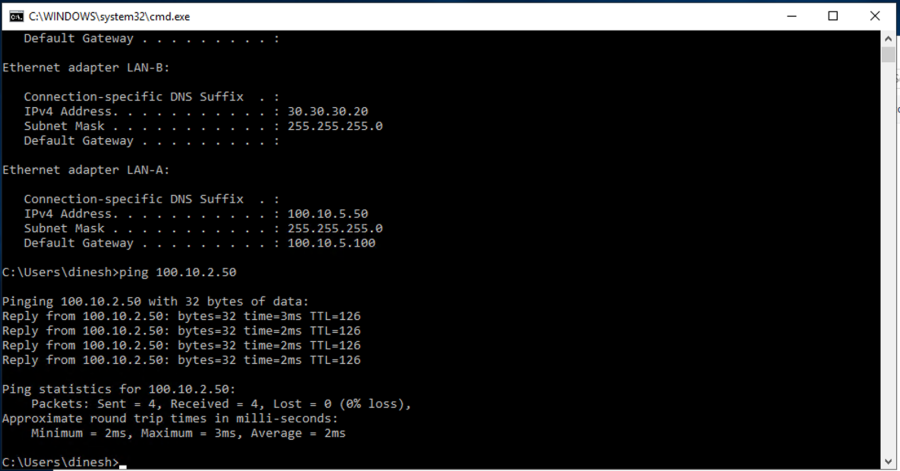
Branch to Branch traffic flow validation