Transparent Active Authentication
by Christian Casavant (Versa Networks)Introduction
The goal of this paper is to provide instructions on how to configure Transparent Active Authentication to accomplish three goals:- Allow the VOS to identify users by username as opposed to source IP address.
- Propagate the username information to Analytics.
- Enable the VOS to match security, QoS, and application steering policy on username or group membership.
- Passive Authentication using the Versa Messaging Service. This is a scalable and elegant method to authenticate and identify users without interactivity by the customer. An agent receives notifications from a Microsoft Active Directory Service and the Versa Messaging Service, which is a standalone headend component, and shares this with the VOS branches. The VOS can then apply policy based on the user or group membership.
- Active Authentication via a Captive Portal. In this method, after users log onto their Windows devices via the Microsoft Active Directory (AD) domain controller, users would be prompted to manually authenticate a 2nd time via the VOS captive portal. Once this second authentication is successfully completed, the VOS can apply policy based on the user or group membership.
 The Datacentre site consists of:
The Datacentre site consists of:
- Dual VOS appliances each connected to MPLS and Internet transports
- A domain controller, acting as a DNS server and Active Directory service.
- Server: for any number of various workloads. In this example, it’s an apache web server.
- Dual VOS appliances, one connected to the MPLS transport and the other connected to the Internet transport.
- A Windows10 machine for the user Alice, who is a member of the Marketing group.
- A Windows10 machine for the user Bob, who is a member of the Engineering group.
REQUIREMENTS
This document is written using 22.1.3, but all the required elements of this solution are available from 20.2 onwards. NB: 20.2.x was End of Support on June 30, 2023. Administrators are strongly advised to ensure they use minimum supported software versions which is 21.2.3 which goes End of Life on Sept 30, 2024 and End of Support on Sept 30, 2025. The following VOS features are required for this solution to work, and will be detailed in this document:- HTTP Proxy
- Captive Portal
- Kerberos Authentication
- LDAP Authentication
- Microsoft Server 2012: which is configured as a Domain Controller and DNS server.
- Windows10: any windows operating system will do.
BROWSER CONFIGURATION
Transparent Active Authentication relies on modern web browsers’ ability to silents authenticate users to captive portals via cached Windows domain credentials. The IT administrator will be responsible for the configuration of the browsers. Internet Explorer requires configuration in 3 places to support silent authentication, can be accessed from Explorer by clicking on Tools, then Internet Options, and then selecting the Security tab. 1 – In the Internet Zone, click on Custom level and scroll to the User Authentication section. Select “Automatic Log-on with current username and password.”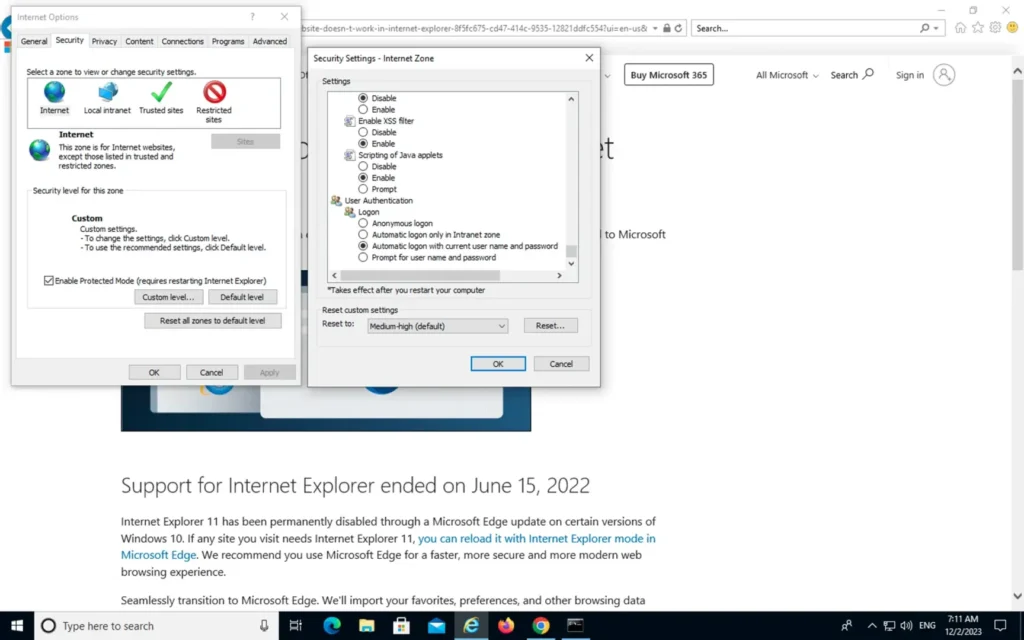 2 – Repeat the same process, but this in the Local Intranet Zone. Click on Custom level and scroll to the User Authentication section. Select “Automatic Log-on with current username and password.”
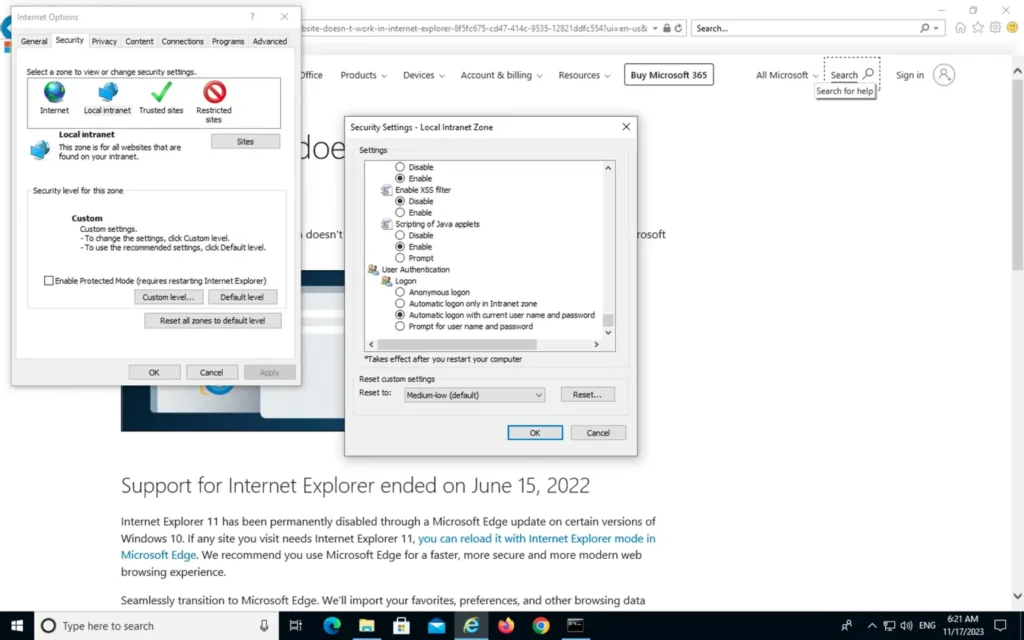
2 – Repeat the same process, but this in the Local Intranet Zone. Click on Custom level and scroll to the User Authentication section. Select “Automatic Log-on with current username and password.”
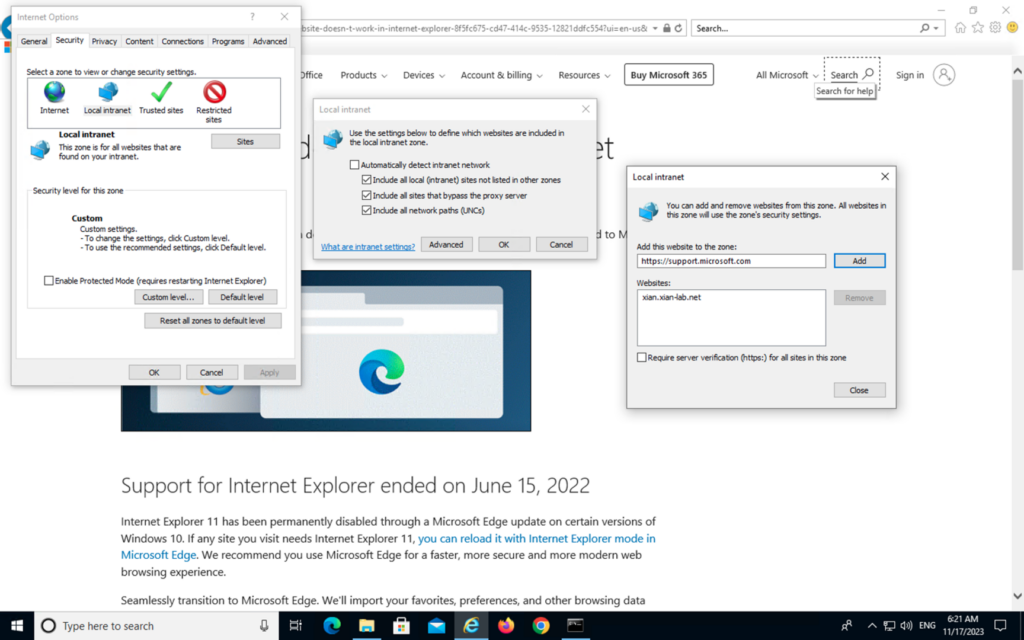
 3 – Still in the Local Intranet Zone. Click on Sites, then on Advanced. Enter the virtual URL that will be used for the captive portal authentication in the text field below “Add this website to the Zone” and then click on add, as can be seen in the screenshot below. It will then appear in the list of Websites. The Versa network administrator can choose any virtual URL.
3 – Still in the Local Intranet Zone. Click on Sites, then on Advanced. Enter the virtual URL that will be used for the captive portal authentication in the text field below “Add this website to the Zone” and then click on add, as can be seen in the screenshot below. It will then appear in the list of Websites. The Versa network administrator can choose any virtual URL.
Note: the virtual URL must resolve to an IP address, which should be the VRRP Virtual LAN IP address of the branch routers.
Ideally, this will be a result of DNS resolution, but it’s possible for the hosts file to be edited.
Note: the virtual URL is the same URL that will be used later in the VOS Kerberos configuration section.
AUTHENTICATION BYPASS
The Windows desktop device will need to authenticate to the domain controller and need to resolve DNS addresses, such as the Kerberos virtual URL mentioned above prior to the browser authenticating, so it’s important to configure authentication bypass rules. An example of the rule which excludes DNS and Active Directory from being authenticated is just:set orgs org-services XIAN security authentication-policies Default-Policy rules BYPASS-DC-SERVER rule-disable false set orgs org-services XIAN security authentication-policies Default-Policy rules BYPASS-DC-SERVER match destination address address-list [ DC-DOMAIN-CONTROLLER ] set orgs org-services XIAN security authentication-policies Default-Policy rules BYPASS-DC-SERVER match application predefined-application-list [ DNS DOMAIN MS_AD ] set orgs org-services XIAN security authentication-policies Default-Policy rules BYPASS-DC-SERVER set action no-authenticate set orgs org-services XIAN security authentication-policies Default-Policy rules BYPASS-DC-SERVER set logging false
HTTP PROXY
When traffic enters the VOS branch appliance the first thing the VOS will do when perfoming the transparent active authentication is to proxy the traffic that requires authentication. In order to ensure that the user is not forced to manually enter their username and password, the proxy is configured as transparent. In addition, since browser captive portal traffic will be both https and http traffic, it’s not necessary to configure an SSL decryption policy and so the proxy will only look into intercept port 80 traffic. The configuration required to support the HTTP proxy is:set orgs org-services XIAN vfp HTTPS-PROXY mode transparent set orgs org-services XIAN vfp HTTPS-PROXY port [ 80 ] set orgs org-services XIAN vfp HTTPS-PROXY routing-instance-list [ XIAN-LAN-VR ] set orgs org-services XIAN vfp HTTPS-PROXY lef-profile-default true set orgs org-services XIAN vfp HTTPS-PROXY parse-response no set orgs org-services XIAN vfp HTTPS-PROXY parse-request no set orgs org-services XIAN vfp HTTPS-PROXY honour-pbf false
CAPTIVE PORTAL
In the traditional sense, the captive portal’s function is to redirect web traffic to an authentication page to make sure only authorized users can access the network at which point users are required to manually enter their authentication credentials. Since we configured the browsers earlier to cache the user’s credentials, the user will not need to manually enter them, the browser will authenticate the user on their behalf. The configuration required to enable the captive portal is just below: Soldeu-R1 Branch Router:set orgs org-services XIAN security captive-portal expiration-time 30 set orgs org-services XIAN security captive-portal anchoring ip-address-based set orgs org-services XIAN security captive-portal service-endpoints XIAN-LAN-VR http-port 44490 set orgs org-services XIAN security captive-portal service-endpoints XIAN-LAN-VR https-port 44991 set orgs org-services XIAN security captive-portal service-endpoints XIAN-LAN-VR ip-addresses [ 172.16.120.2 ] set orgs org-services XIAN security captive-portal service-endpoints XIAN-LAN-VR cookie-auth-profile KERBEROS-AUTHENTICATION-PROFILESoldeu-R2 Branch Router:
set orgs org-services XIAN security captive-portal expiration-time 30 set orgs org-services XIAN security captive-portal anchoring ip-address-based set orgs org-services XIAN security captive-portal service-endpoints XIAN-LAN-VR http-port 44490 set orgs org-services XIAN security captive-portal service-endpoints XIAN-LAN-VR https-port 44991 set orgs org-services XIAN security captive-portal service-endpoints XIAN-LAN-VR ip-addresses [ 172.16.120.3 ] set orgs org-services XIAN security captive-portal service-endpoints XIAN-LAN-VR cookie-auth-profile KERBEROS-AUTHENTICATION-PROFILE
Note the difference between the captive portal IP addresses on Soldeu-R1 and Soldeu-R2. Each device is configured for the captive portal on their physical LAN interface, even though the virtual URL resolves to the VRRP.
KERBEROS AUTHENTICATION
Kerberos is an authentication protocol that uses “tickets” for the client and the server to authenticate each other. Functionality of the protocol is beyond the scope of this document. The captive portal is used to gather the Windows domain user credentials and pass them to the Kerberos authentication service on the VOS. In this section, action is required by the tenant’s IT administrator on the Domain Controller. Three things are required:- Create a user that will be used as the Kerberos user
- Create a Kerberos Keytab. Keytabs are used to authenticate to Kerberos automatically without asking a user to enter a password.Note: If the Kerberos user’s password is changed for whatever reason, the keytabs need to be regenerated and redistributed to all the VOS appliances using the transparent active authentication.
- If the administrator has not configured NTP on the server, they should do at this point.
Kerberos User
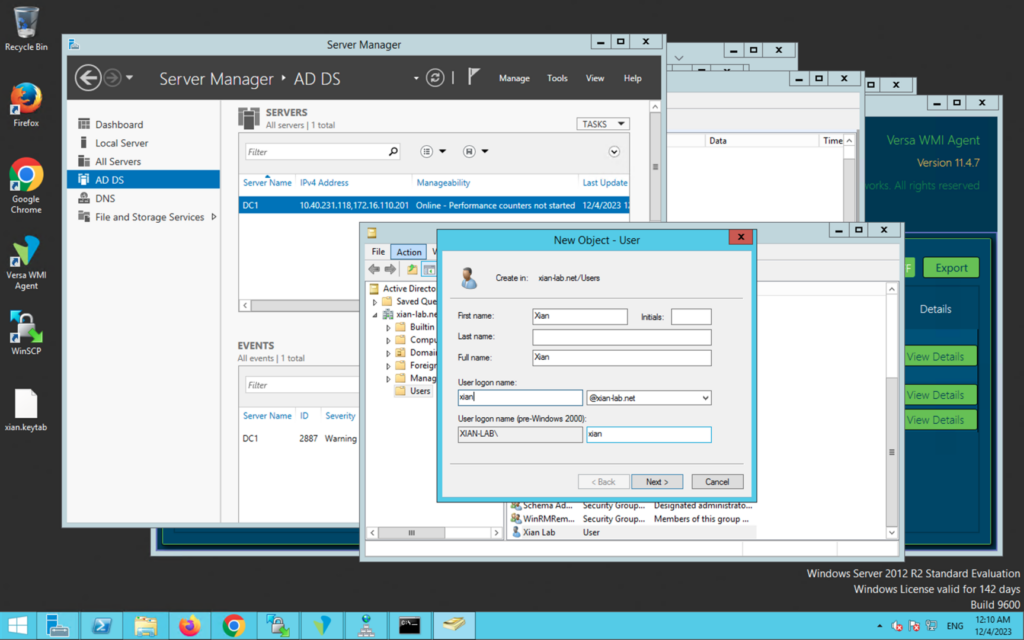
From the Windows Server Manager, clock on Tools and then Active Directory Users and Computers. Click on Action, New and select User. This is standard user creation, but you should take note of the following information when creating the user:- Username, in our example, xian
- The windows domain, in our example, xian-lab.net
 Click on next and you will be presented with the password settings. Note the password options. We do not want the password to be reset at first log on. Given that if the password changes the keytabs need to recreated and redistributed, password never expired is also selected. Therefore the Domain and network administrators can more effectively control the change.
Click on next and you will be presented with the password settings. Note the password options. We do not want the password to be reset at first log on. Given that if the password changes the keytabs need to recreated and redistributed, password never expired is also selected. Therefore the Domain and network administrators can more effectively control the change.
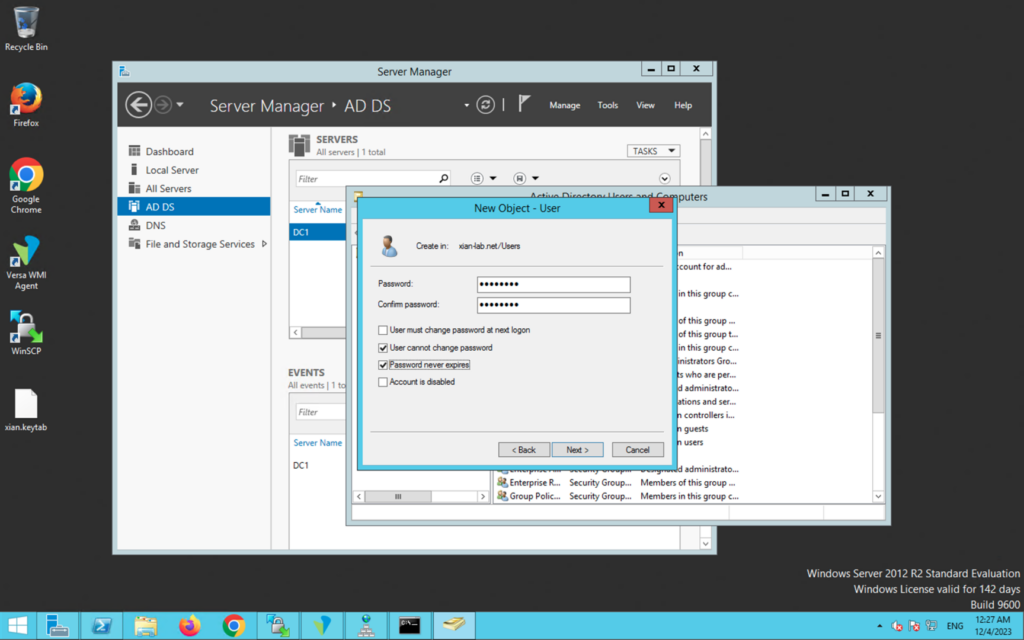 Click on next and then finish. You will see from the Server Manager GUI, the user is created, but additional verification is available running the following command from Powershell: aduser xian
Click on next and then finish. You will see from the Server Manager GUI, the user is created, but additional verification is available running the following command from Powershell: aduser xian
PS C:\User\Administrator\Desktop> aduser xian DistinguishedName : CN=Xian Lab,CN=Users,DC=xian-lab,DC=net Enabled : True GivenName : Xian Name : Xian Lab ObjectClass : user ObjectGUID : f0773c0e-78d0-43fd-951caee80cdd SamAccountName : xian SID : S-1-5-21-9903592883-3735217373-2052298951-1106 Surname : Lab UserPrincipalName : xian@xian-lab.net
Note the UserPrincipalName is xian@xian-lab.net
Keytab Creation
Open Powershell and enter the following command based on the user credentials we took note of above:ktpass.exe -princ HTTP/xian.xian-lab.net@XIAN-LAB -mapuser xian -mapOp set -pass Versa123@ -crypto all -ptype KRB5_NT_PRINCIPAL -out xian.keytabTo verify the keytab creation, you can run the following command from Powershell: aduser xian
PS C:\User\Administrator\Desktop> aduser xian DistinguishedName : CN=Xian Lab,CN=Users,DC=xian-lab,DC=net Enabled : True GivenName : Xian Name : Xian Lab ObjectClass : user ObjectGUID : f0773c0e-78d0-43fd-951caee80cdd SamAccountName : xian SID : S-1-5-21-9903592883-3735217373-2052298951-1106 Surname : Lab UserPrincipalName : HTTP/xian.xian-lab.net@XIAN-LAB
Note the user principal name has changed from xian@xian-lab.net which was seen during original user creation to the SPN (Service Principal Name) HTTP/xian.xian-lab.net@XIAN-LAB
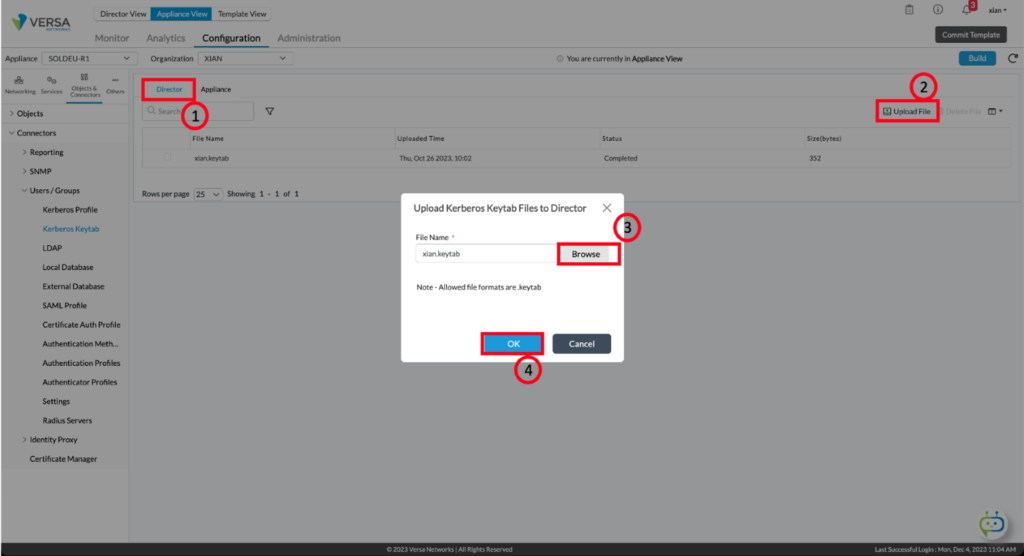
Upload Keytab to Director and VOS.
The keytab that was generated in the step above must be uploaded first to the Director and to each of the VOS appliances that may authenticate the users. Ideally, the Windows Server will have reachability to the Director and the tenant administrator can log in and upload from there. In the environment that was used for this, there was no access to the Director, and so scp was required to get the xian.keytab file from the Windows Server to the device from which the Director GUI was accessed. To upload the keytab file to the Director, navigate to the device appliance context, select Objects & Connectors, expand Connectors, expand Users/Groups, and click on Kerberos Keytab. From there, you must:- Make sure you are on the Director tab
- Click on upload file
- Browse to the keytab file location
- Click OK to upload it.
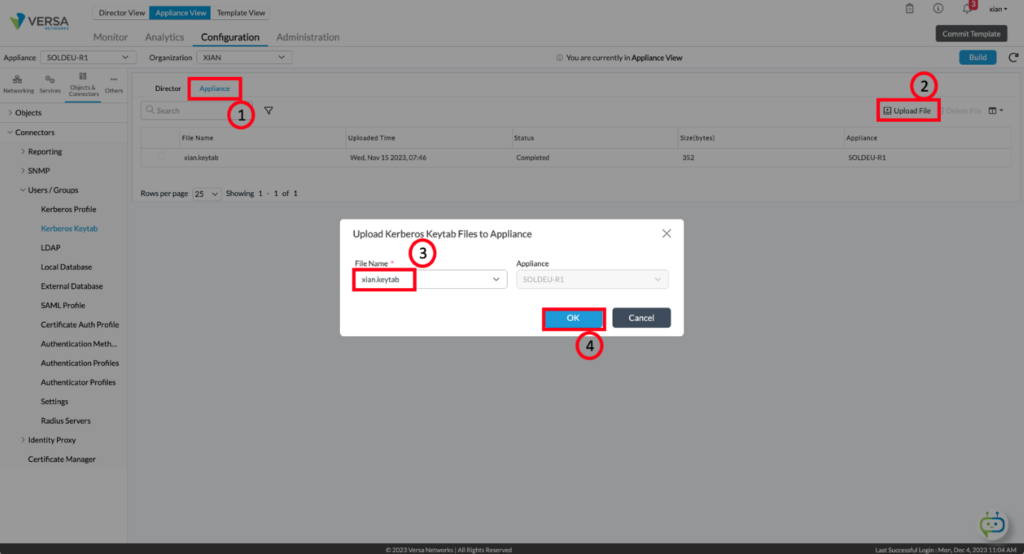
 The keytab then needs to get placed onto the Appliance from the Director from the same screen:
The keytab then needs to get placed onto the Appliance from the Director from the same screen:
- Click on the appliance tab
- Click on upload file
- Select the Keytab file from the pulldown menu
- Click OK to upload it.
Deploy Kerberos on VOS
After the keytab has been uploaded to the VOS, the rest of the Kerberos authentication can be configured. Three things will need to be configured in this order:- Kerberos Profile
- Authentication Method
- Authentication Profiles
set orgs org-services XIAN user-identification kerberos-profiles KERBEROS-PROFILE keytab xian.keytab set orgs org-services XIAN user-identification kerberos-profiles KERBEROS-PROFILE spn HTTP/xian.xian-lab.net@XIAN-LAB set orgs org-services XIAN user-identification kerberos-profiles KERBEROS-PROFILE virtual-url xian.xian-lab.net set orgs org-services XIAN user-identification authentication-methods KERBEROS-AUTHENTICATION-METHOD method kerberos KERBEROS-PROFILE set orgs org-services XIAN user-identification authentication-profiles KERBEROS-AUTHENTICATION-PROFILE expiration-time 10 set orgs org-services XIAN user-identification authentication-profiles KERBEROS-AUTHENTICATION-PROFILE lef-profile-default true set orgs org-services XIAN user-identification authentication-profiles KERBEROS-AUTHENTICATION-PROFILE authentication-type active set orgs org-services XIAN user-identification authentication-profiles KERBEROS-AUTHENTICATION-PROFILE caching-mode IP-based set orgs org-services XIAN user-identification authentication-profiles KERBEROS-AUTHENTICATION-PROFILE expiration-mode inactivity set orgs org-services XIAN user-identification authentication-profiles KERBEROS-AUTHENTICATION-PROFILE concurrent-login 5 set orgs org-services XIAN user-identification authentication-profiles KERBEROS-AUTHENTICATION-PROFILE default-method [ KERBEROS-AUTHENTICATION-METHOD ]In the Kerberos-profiles section, note the three parameters that have been configured:
- The xian.keytab file which was generated and uploaded earlier.
- The SPN, which we chose during the Kerberos user configuration, and can see from the output of the “aduser xian” Powershell command.
- The virtual URL, which we also specified in the keytab creation, is derived from the SPN. This URL must resolve to either the physical LAN IP address of the VOS, or in the case of a high availability deployment, the VRRP Virtual IP address.
- This is an active authentication type and must be selected.
- The caching mode is IP based.
- The expiration timer has been set to 10 minutes.
- The expiration mode is inactivity.
- Logging has been enabled: it’s up to the administrator to decide whether to log authentication activity. Factors in this decision may be things such as the rate of authentication activity and load on the Analytics.
Authentication Policies
The last elements of the kerberos authentication configuration are the authentication policies. Fundamentally only two authentication policies are required to support this particular use case:- A “bypass” rule, which allows the windows devices to use the domain controllers for domain name resolution as well as to allows the user to authenticate to their active directory.
- The rule to authenticate the HTTP traffic for the browser.
set orgs org-services XIAN security authentication-policies Default-Policy rules BYPASS-DC-SERVER rule-disable false set orgs org-services XIAN security authentication-policies Default-Policy rules BYPASS-DC-SERVER match destination address address-list [ DC-DOMAIN-CONTROLLER ] set orgs org-services XIAN security authentication-policies Default-Policy rules BYPASS-DC-SERVER match application predefined-application-list [ DNS DOMAIN MS_AD ] set orgs org-services XIAN security authentication-policies Default-Policy rules BYPASS-DC-SERVER set action no-authenticate set orgs org-services XIAN security authentication-policies Default-Policy rules BYPASS-DC-SERVER set logging false set orgs org-services XIAN security authentication-policies Default-Policy rules AUTHENTICATE-HTTP rule-disable false set orgs org-services XIAN security authentication-policies Default-Policy rules AUTHENTICATE- HTTP match services predefined-services-list [ http ] set orgs org-services XIAN security authentication-policies Default-Policy rules AUTHENTICATE- HTTP set action authenticate set orgs org-services XIAN security authentication-policies Default-Policy rules AUTHENTICATE- HTTP set authentication-profile KERBEROS-AUTHENTICATION-PROFILE set orgs org-services XIAN security authentication-policies Default-Policy rules AUTHENTICATE- HTTP set logging true set orgs org-services XIAN security authentication-policies Default-Policy rules AUTHENTICATE- HTTP set lef-profile-default trueAs can be seen in the AUTHENTICATE-HTTP rule, the authentication policy refers to the KERBEROS-AUTHENTICATION profile that was just defined. In addition, logging has been enabled. The administrator will need to decide whether long term persistent logging of authentication is required depending on Analytics capacity. Versa would recommend logging is enabled during testing, and once it has been ascertained authentication works as designed, logging can then be disabled.
KERBEROS VERIFICATION & TROUBLESHOOTING
Basic infrastructure verification isn’t covered in this document, however, if users aren’t successfully authenticating, then it may be of value to do basic health checks such as verifying the routing table and pinging from the windows device to the domain controller. To that end adding ICMP to the authentication bypass rules configured above could be a good tactical step to verify end to end reachability prior to looking at the Kerberos. To verify user authentication, we have a number of methods available from the GUI as well as from the CLI- Verify Authentication Profiles
- Verify Authentication Policies
- Verify the Kerberos Profile
- See list of live users.
- Debug Identity.
Verify Authentication Profile
Via the GUI, authentication profile statistics to see if the profile itself is getting hits by navigating to Monitor -> Devices and select the appropriate device. In this example, it’s SOLDEU-R1. From there, click on the Services tab, select NGFW, scroll to the right along the features, and click on User Authentication. From the pulldown menu, select Authentication Profile and you will see the statistics for the KERBEROS Authentication profile.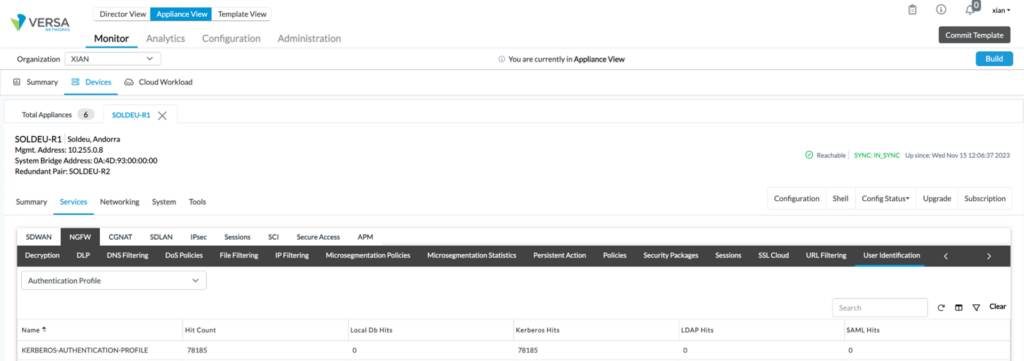 From the CLI, issue the following command:
From the CLI, issue the following command:
show orgs org-services XIAN user-identification authentication-profiles-stats statistics KERBEROS-AUTHENTICATION-PROFILEBoth commands will show the hit count of the profile as well as the Kerberos hits. If the number increments then we can tell the authentication profile is working properly.

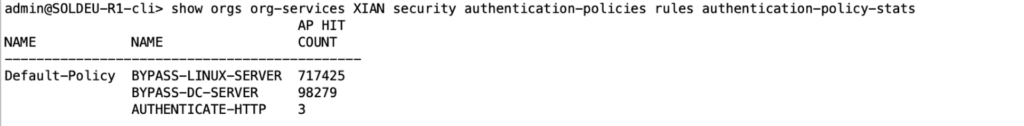
Verify Authentication Policies
To verify that users can bypass authentication as well as check that the HTTP authentication policy is matching. A positive integer indicates the policy has successfully matched, a zero integer, or if numbers don’t increment, it could indicate a configuration issue. Still in the monitor NGFW tab, click on Authentication Policies and select Default-Policy from the pulldown menu. The same command is available via the CLI
The same command is available via the CLI
show orgs org-services XIAN security authentication-policies rules authentication-policy-stats
Verify Kerberos Profile
Looking at the Kerberos profile will show us whether the profile is being hit at all, whether proxy sessions have been established, how many Kerberos tokens have been received as well as successful and failed authentications. Still in the monitor NGFW tab, click on User-Identification and select Kerberos profile from the pulldown menu.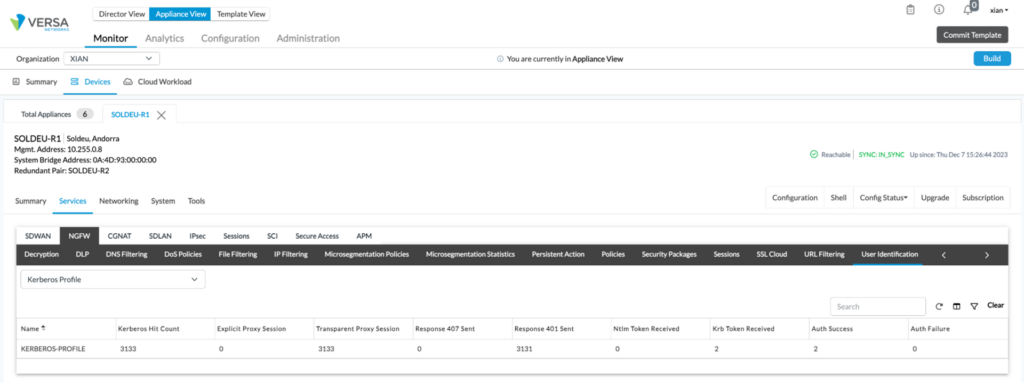 From the CLI, the following command will give the same information:
From the CLI, the following command will give the same information:
show orgs org-services XIAN user-identification kerberos-profiles-stats statistics
 Incrementing hit counts are positive indications, especially in the KRB token and auth success columns.
If there are no hit counts or if there are no KRB tokens received, review the kerberos authentication profile.
If there are auth failures, check to make sure the correct keytab has been properly uploaded to the VOS appliance, and also confirm that the VOS and the DC have NTP synced time.
Incrementing hit counts are positive indications, especially in the KRB token and auth success columns.
If there are no hit counts or if there are no KRB tokens received, review the kerberos authentication profile.
If there are auth failures, check to make sure the correct keytab has been properly uploaded to the VOS appliance, and also confirm that the VOS and the DC have NTP synced time.
Live User List
If authentication is successful, we will see the IP to user mapping in the live user list. Still in the Director GUI Monitor NGFW tab, scroll back to the right and select User-Identification. Select Live Users from the pulldown menu and choose between brief and detail.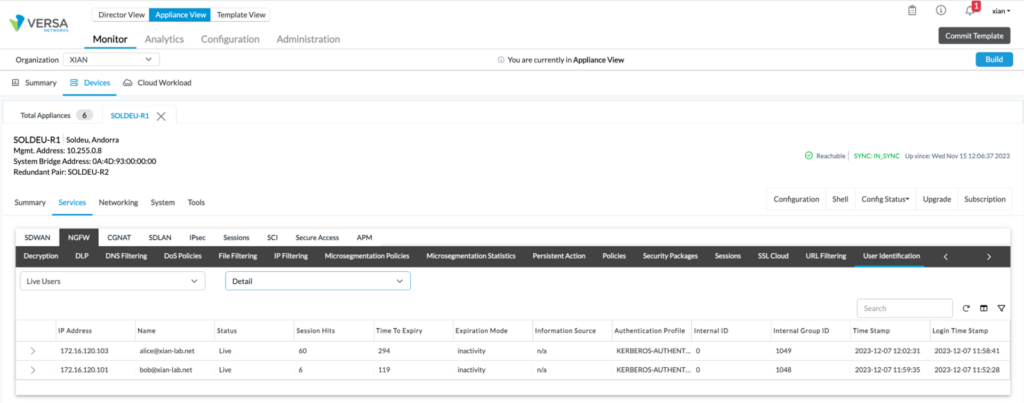 Here we will see the username and their IP address, and importantly we can see how much time is left before the user expires. And, as usual, this information is available via the CLI with the following command:
Here we will see the username and their IP address, and importantly we can see how much time is left before the user expires. And, as usual, this information is available via the CLI with the following command:
show orgs org-services XIAN user-identification live-users list brief
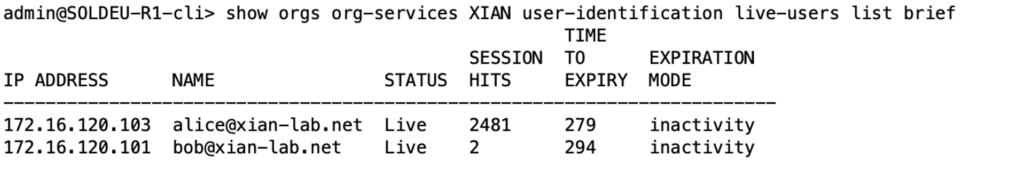 The only thing that we are looking for at this stage is to ensure that we have users that are authenticated, and therefore “known” to the VOS.
The only thing that we are looking for at this stage is to ensure that we have users that are authenticated, and therefore “known” to the VOS.
Analytics Verification
Director verification is real time. If we want to view historical logs, we can view them from the Analytics. From Director, click on the Analytics tab, and then navigate to the Logs dashboard and select Authentication.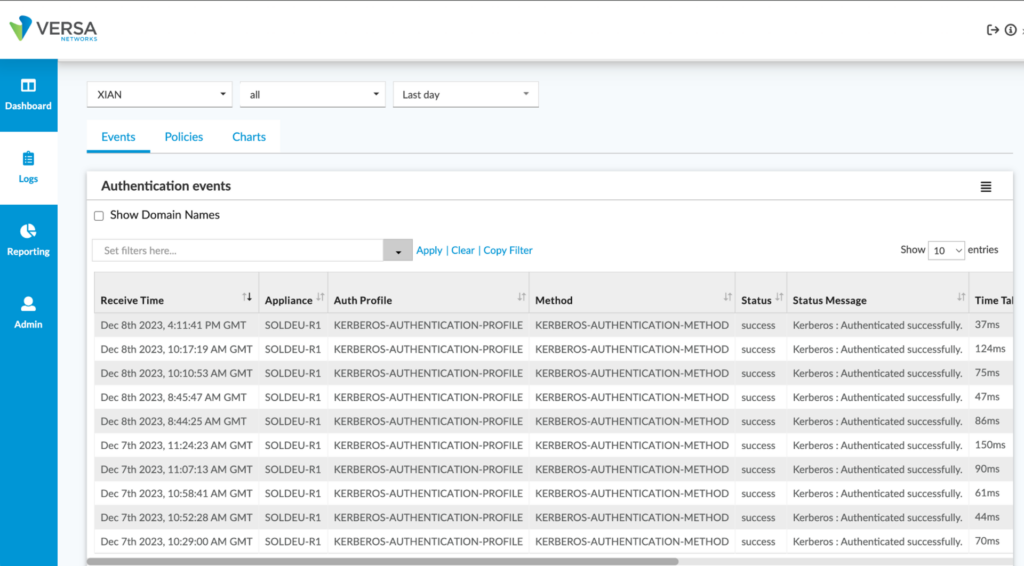
ACTIVE DIRECTORY AUTHENTICATION
Now that we can identify users by authenticating them with Kerberos, the next step is to be able to apply policy based on the user or the group membership. In order to accomplish this task, we will need to do two things:- Create the LDAP connectors so VOS can fetch the list of users and groups from the Active Directory server against which to apply policy.
- The Director will need to have an LDAP proxy so that rules can be configured.
LDAP Connectors
It is strongly recommended to deploy the LDAP configuration via the workflow. It’s not mandatory, however to configure the LDAP service, you will need to configure the servers, paired TVI interfaces for the hostbound LDAP traffic, traffic identification for these interfaces, NGFW rules for the hostbound traffic, SNAT rules, CGNAT rules, ldap profiles, and the routing. By using the workflow templates from the director all of that configuration is automatically deployed. To achieve this, go to the Director view and clock on Workflows. Select your template, and then go the Management Servers section and click on LDAP Servers. You will need the following pieces of information to complete this task, all except the first item needs to be given by the AD Server administrator.
You will need the following pieces of information to complete this task, all except the first item needs to be given by the AD Server administrator.
- On which VR will the AD server be reachable
- IP address of the server
- Domain Name
- Base DN
- Bind DN
- Bind Password
set orgs org-services XIAN user-identification ldap-profiles LARGE-LAN-172.16.110.201-Profile servers LARGE-LAN-172.16.110.201-Server routing-instances XIAN-LAN-VRA screenshot of the Device Template Configuration can be seen just below. Navigate to Objects & Connectors -> Users/Groups -> LDAP. Select the LDAP Server Profiles and then click on Servers tab and choose the correct routing instance for the dropdown list.

Director Appliance Proxy
To support the configuration of user and group policy configuration, the Director needs to be able to query the LDAP server. To do this, you will need to go into the Director View, click on the Administration tab, and select organizations. Select the appliance through which the LDAP service is reachable, the LDAP Server Profile and Click okay.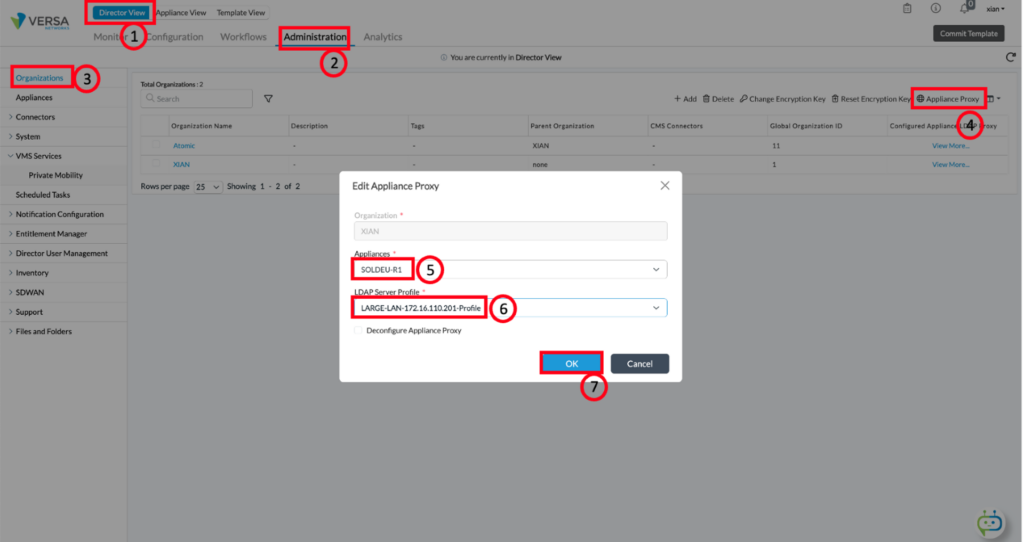 You can view the list of appliance proxies, by clicking on View More to the right of the organization:
You can view the list of appliance proxies, by clicking on View More to the right of the organization:
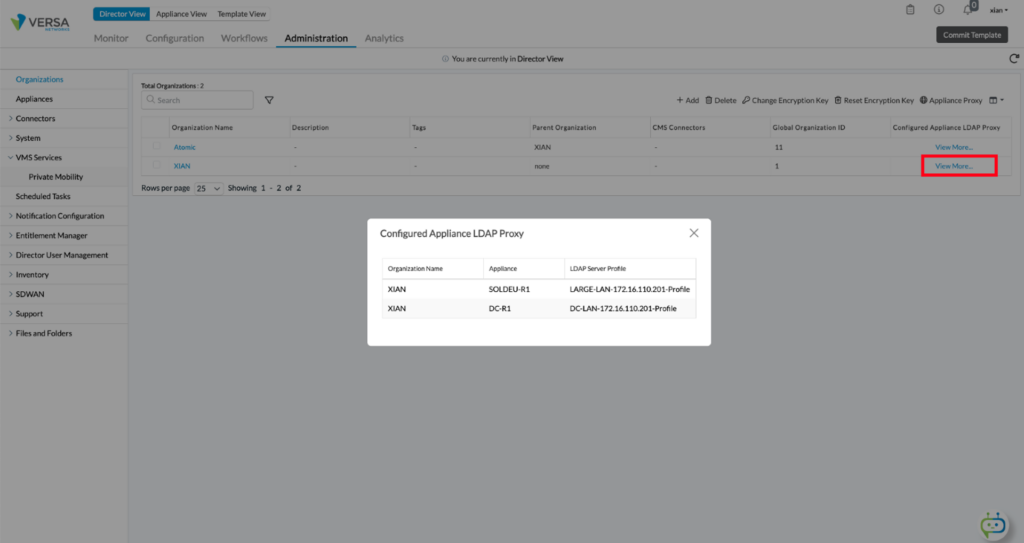
Verification
Since Kerberos is authenticating users and not LDAP, looking at the user-identification output in the Director will not show any hits: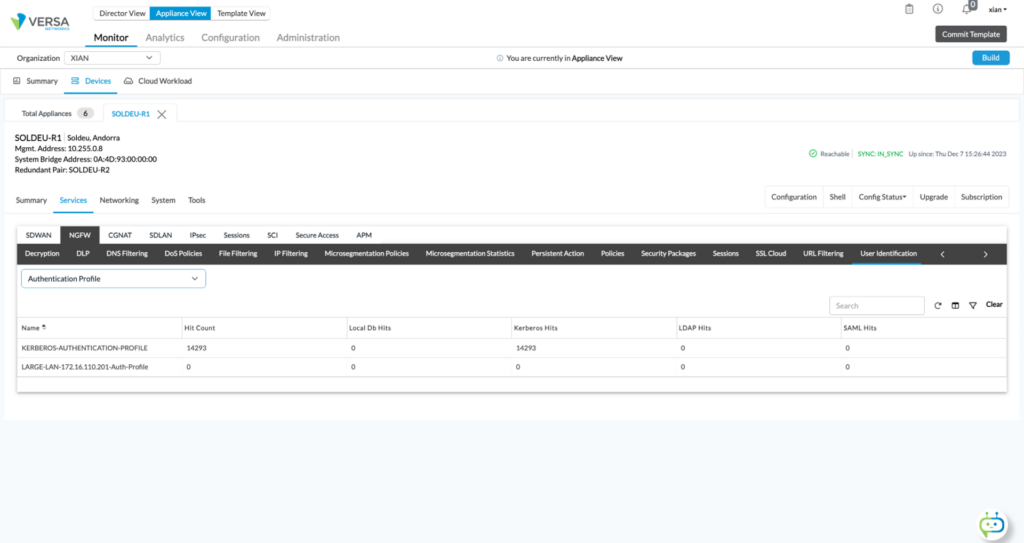 The only option is to access the CLI of the VOS appliance and issue the following command:
The only option is to access the CLI of the VOS appliance and issue the following command:
show orgs org-services XIAN user-identification ldap-server-data users briefIf the LDAP configuration is working properly, then the output will give you a list of the LDAP users the VOS fetched. If you would like to view the list of groups, then replace the word users with groups.
 To Verify the Director Appliance Proxy is working properly, you need to configure a policy. From the Director, click on Appliance View and click on Configuration. Select Services, Next Generation Firewall, and select a rule to edit. Click on the Users/Groups tab and from the match users pulldown menu, choose Selected. Then, from the User Group Profile, select the User Group profile. Add a group and start to type. In the screenshot below, you can see “Ma” was typed. If the LDAP proxy is working, then you will see Marketing will be populated into the pulldown menu:
To Verify the Director Appliance Proxy is working properly, you need to configure a policy. From the Director, click on Appliance View and click on Configuration. Select Services, Next Generation Firewall, and select a rule to edit. Click on the Users/Groups tab and from the match users pulldown menu, choose Selected. Then, from the User Group Profile, select the User Group profile. Add a group and start to type. In the screenshot below, you can see “Ma” was typed. If the LDAP proxy is working, then you will see Marketing will be populated into the pulldown menu:
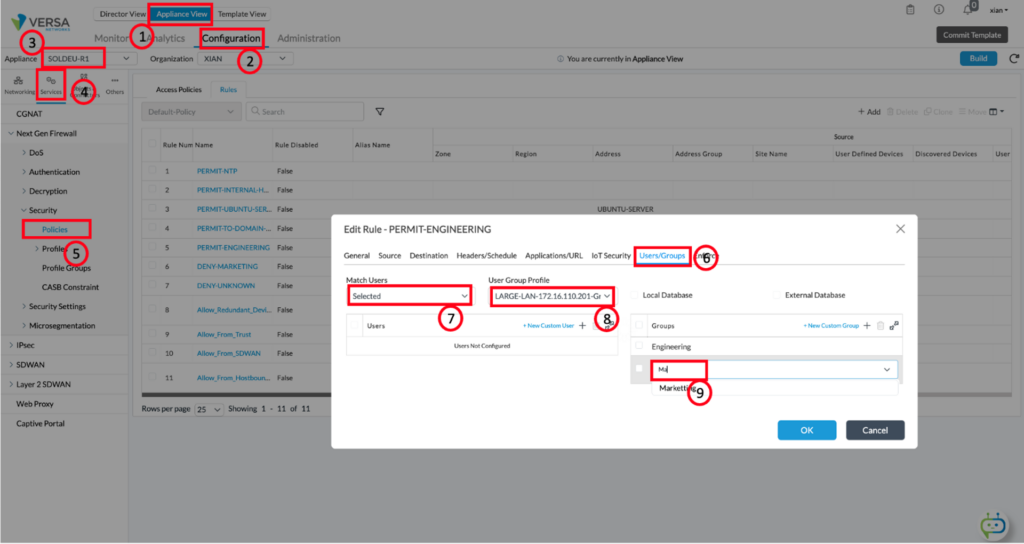
POLICY CONFIGURATION
It is possible to leverage user-identification to apply other policies such as application steering or to match per-user policer policies, but the most common use case for identifying users is to apply security policy to group membership. For SD-WAN or Security policies, the way to configure policy match is the same. When creating or editing SD-WAN and Security policies the configuration is the same as the verification policy listed above. In the screenshot below, where we can see how user and group policy is configured, the starting point is the policy rule editing.
- Click on the User/Group Policy
- Match Users
- Any: this applies to any user; known, unknown, or selected. If Any is selected, steps 3, 4, and 5 will be skipped.
- Known: if the IP to username mapping for traffic sourced from a user exists in the VOS, this rule will match. If Known is selected, steps 3, 4, and 5 will be skipped.
- Unknown: if the IP to username mapping for traffic sourced from a user does not exist in the VOS, this rule will match. If Unknown is selected, steps 3, 4, and 5 will be skipped.
- Selected: if traffic is sourced from a specific user, list of users, group, or list of groups this rule will match. Proceed to step 3.
- Select the User Group Profile
- In this case, the policy will be applied to group membership, as opposed to a specific user or list of users. Technically, both can be used, but applying policy to individual users is not scalable, and it’s recommended to match on groups.
- Choose the groups from which to apply the policy and then click on Okay.
- Permit traffic to internal subnets from all users
- Deny traffic from users in Marketing group
- Permit traffic from users in the Engineering group.
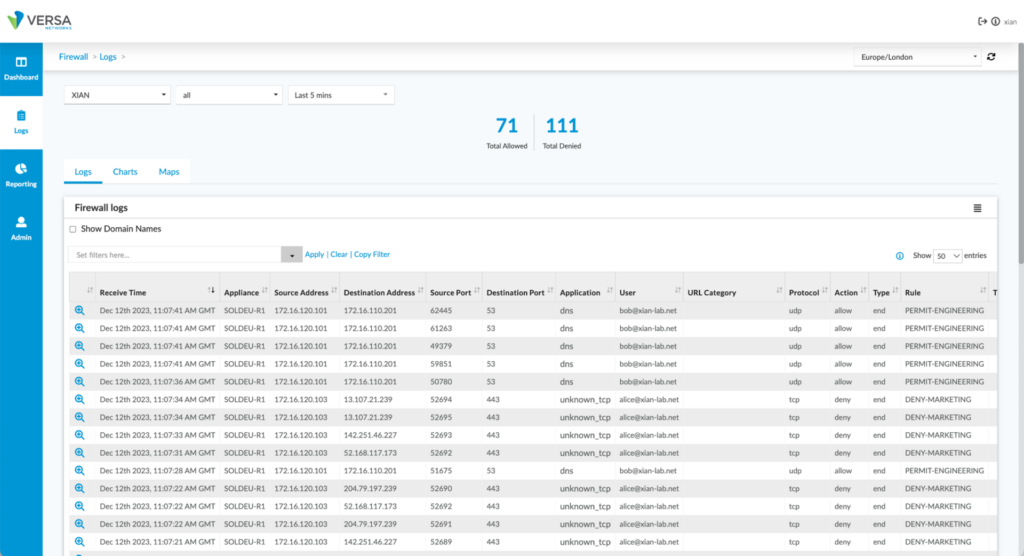
Verification
In Analytics, on the branch site which has the Kerberos authentication and which has identified the user we can now see the user referenced by their user-principal-name as evidenced by the following screenshot: To verify that security policy has permitted traffic from Engineering and denied traffic from Marketing, we can view the firewall logs in which we can see:
To verify that security policy has permitted traffic from Engineering and denied traffic from Marketing, we can view the firewall logs in which we can see:
- Traffic from Alice, who is in the Marketing group is denied
- Traffic from Bob, who is in the Engineering group is allowed.
CONCLUSION
The Transparent Active Authentication solution described in this document is an alternative to the Passive Authentication solution powered by the Versa Messaging Server and the Identity & Authentication Engine, however it is not without constraints and limitations such as:- The live-user database is only populated on the local VOS. The implication of this limitation is that we will only see the user populated on the local branch. The username will not appear in Analytics for the DC.
- If the DC is being used as a central internet breakout, it’s not possible to authenticate users in the same way. Transparent Active Authentication is ideally used for Direct Internet Access or to apply perimeter security policy for the SD-WAN estate.
- Requires effort on the part of the customer LAN IT administrator to ensure the AD server has a Kerberos account as well as ensuring the
- This solution is easily configured via Device Templates or Device Context, but is a much more complex task to do with service templates because every LDAP server profiles will need to be duplicated in the service template.
Additional Resources
Please visit the Versa Documentation page for additional information on the following components: Kerberos Authentication: https://docs.versa-networks.com/Secure_SD-WAN/01_Configuration_from_Director/Security_Configuration/Configure_Kerberos_Authentication Configure User and Group Policy: https://docs.versa-networks.com/Secure_SD-WAN/01_Configuration_from_Director/Security_Configuration/Configure_User_and_Group_Policy Captive Portal: https://docs.versa-networks.com/Secure_SD-WAN/01_Configuration_from_Director/Security_Configuration/Configure_URL_Filtering#Configure_Captive_Portal HTTP Proxy: https://docs.versa-networks.com/Secure_SD-WAN/01_Configuration_from_Director/Security_Configuration/Configure_HTTP%2F%2FHTTPS_Proxy#Configure_a_Transparent_Proxy Passive Authentication: https://docs.versa-networks.com/Management_and_Orchestration/Versa_Messaging_Service/Passive_Authentication/Configure_Passive_Authentication_for_VMSAnnex: Director Template Configuration
set devices template LARGE config orgs org-services XIAN user-identification kerberos-profiles kerberos-profile KERBEROS-PROFILE keytab xian.keytab set devices template LARGE config orgs org-services XIAN user-identification kerberos-profiles kerberos-profile KERBEROS-PROFILE spn HTTP/xian.xian-lab.net@XIAN-LAB set devices template LARGE config orgs org-services XIAN user-identification kerberos-profiles kerberos-profile KERBEROS-PROFILE virtual-url xian.xian-lab.net set devices template LARGE config orgs org-services XIAN user-identification authentication-methods authentication-method KERBEROS-AUTHENTICATION-METHOD method kerberos KERBEROS-PROFILE set devices template LARGE config orgs org-services XIAN user-identification authentication-methods authentication-method LARGE-LAN-172.16.110.201-Auth-Method method ldap LARGE-LAN-172.16.110.201-Profile set devices template LARGE config orgs org-services XIAN user-identification authentication-profiles authentication-profile KERBEROS-AUTHENTICATION-PROFILE expiration-time 10 set devices template LARGE config orgs org-services XIAN user-identification authentication-profiles authentication-profile KERBEROS-AUTHENTICATION-PROFILE lef-profile-default true set devices template LARGE config orgs org-services XIAN user-identification authentication-profiles authentication-profile KERBEROS-AUTHENTICATION-PROFILE authentication-type active set devices template LARGE config orgs org-services XIAN user-identification authentication-profiles authentication-profile KERBEROS-AUTHENTICATION-PROFILE caching-mode IP-based set devices template LARGE config orgs org-services XIAN user-identification authentication-profiles authentication-profile KERBEROS-AUTHENTICATION-PROFILE expiration-mode inactivity set devices template LARGE config orgs org-services XIAN user-identification authentication-profiles authentication-profile KERBEROS-AUTHENTICATION-PROFILE concurrent-login 5 set devices template LARGE config orgs org-services XIAN user-identification authentication-profiles authentication-profile KERBEROS-AUTHENTICATION-PROFILE default-method [ KERBEROS-AUTHENTICATION-METHOD ] set devices template LARGE config orgs org-services XIAN user-identification authentication-profiles authentication-profile KERBEROS-AUTHENTICATION-PROFILE proactive-reauth disabled set devices template LARGE config orgs org-services XIAN user-identification authentication-profiles authentication-profile LARGE-LAN-172.16.110.201-Auth-Profile expiration-time 1 set devices template LARGE config orgs org-services XIAN user-identification authentication-profiles authentication-profile LARGE-LAN-172.16.110.201-Auth-Profile lef-profile-default false set devices template LARGE config orgs org-services XIAN user-identification authentication-profiles authentication-profile LARGE-LAN-172.16.110.201-Auth-Profile caching-mode IP-based set devices template LARGE config orgs org-services XIAN user-identification authentication-profiles authentication-profile LARGE-LAN-172.16.110.201-Auth-Profile expiration-mode inactivity set devices template LARGE config orgs org-services XIAN user-identification authentication-profiles authentication-profile LARGE-LAN-172.16.110.201-Auth-Profile concurrent-login 1 set devices template LARGE config orgs org-services XIAN user-identification authentication-profiles authentication-profile LARGE-LAN-172.16.110.201-Auth-Profile default-method [ LARGE-LAN-172.16.110.201-Auth-Method ] set devices template LARGE config orgs org-services XIAN user-identification ldap-profiles server-profile LARGE-LAN-172.16.110.201-Profile state enabled set devices template LARGE config orgs org-services XIAN user-identification ldap-profiles server-profile LARGE-LAN-172.16.110.201-Profile domain-name xian-lab.net set devices template LARGE config orgs org-services XIAN user-identification ldap-profiles server-profile LARGE-LAN-172.16.110.201-Profile ldap-base CN=Users,DC=xian-lab,DC=net set devices template LARGE config orgs org-services XIAN user-identification ldap-profiles server-profile LARGE-LAN-172.16.110.201-Profile bind-dn CN=Administrator,CN=Users,DC=xian-lab,DC=net set devices template LARGE config orgs org-services XIAN user-identification ldap-profiles server-profile LARGE-LAN-172.16.110.201-Profile bind-password JqJzzLk9MjLmWP0PPC4Dz+iZD6YotTzjo4Q0DZ1iY7nU8WIcWysIomh42vjlTzH1rscCaT/ALLS0jKP+otPLU6IHLH73Vlg1Zb1hFEXQA8UMkZUlEWsEWB33DvudGyuAKcIDD4Tc+dBs9NjJDapWXCbS9OQBdd49mCtMGnwXly5v8CO73OioBq73CZMV+C6orVkrg4rL5kGN7QhC2JWrKmazGREGEfRbRg14uq2gKfyb8qm98pK7mteES/wNOjh4osckbF2HSncRpKybTY0DJZ3I9y3Yy6WvQRpo7EMJ9iUgAFk/FXYDfGRRqtO87IrnlYfANouNbverhv9tHJ4jwg== set devices template LARGE config orgs org-services XIAN user-identification ldap-profiles server-profile LARGE-LAN-172.16.110.201-Profile server-type active-directory set devices template LARGE config orgs org-services XIAN user-identification ldap-profiles server-profile LARGE-LAN-172.16.110.201-Profile use-ssl disabled set devices template LARGE config orgs org-services XIAN user-identification ldap-profiles server-profile LARGE-LAN-172.16.110.201-Profile search-timeout 30 set devices template LARGE config orgs org-services XIAN user-identification ldap-profiles server-profile LARGE-LAN-172.16.110.201-Profile bind-timeout 30 set devices template LARGE config orgs org-services XIAN user-identification ldap-profiles server-profile LARGE-LAN-172.16.110.201-Profile servers server LARGE-LAN-172.16.110.201-Server ip-address 172.16.110.201 set devices template LARGE config orgs org-services XIAN user-identification ldap-profiles server-profile LARGE-LAN-172.16.110.201-Profile servers server LARGE-LAN-172.16.110.201-Server port 389 set devices template LARGE config orgs org-services XIAN user-identification ldap-profiles server-profile LARGE-LAN-172.16.110.201-Profile servers server LARGE-LAN-172.16.110.201-Server routing-instances XIAN-LAN-VR set devices template LARGE config orgs org-services XIAN user-identification group-mapping-profiles map-profile LARGE-LAN-172.16.110.201-Group-Profile state enabled set devices template LARGE config orgs org-services XIAN user-identification group-mapping-profiles map-profile LARGE-LAN-172.16.110.201-Group-Profile group-object-class group set devices template LARGE config orgs org-services XIAN user-identification group-mapping-profiles map-profile LARGE-LAN-172.16.110.201-Group-Profile group-name name set devices template LARGE config orgs org-services XIAN user-identification group-mapping-profiles map-profile LARGE-LAN-172.16.110.201-Group-Profile group-member memberof set devices template LARGE config orgs org-services XIAN user-identification group-mapping-profiles map-profile LARGE-LAN-172.16.110.201-Group-Profile user-object-class user set devices template LARGE config orgs org-services XIAN user-identification group-mapping-profiles map-profile LARGE-LAN-172.16.110.201-Group-Profile user-name userPrincipalName set devices template LARGE config orgs org-services XIAN user-identification group-mapping-profiles map-profile LARGE-LAN-172.16.110.201-Group-Profile refresh-interval 60 set devices template LARGE config orgs org-services XIAN user-identification group-mapping-profiles map-profile LARGE-LAN-172.16.110.201-Group-Profile ldap-server-profile LARGE-LAN-172.16.110.201-Profile set devices template LARGE config orgs org-services XIAN user-identification group-mapping-profiles map-profile LARGE-LAN-172.16.110.201-Group-Profile group-include-list groups-included CN=Engineering,CN=Users,DC=xian-lab,DC=net set devices template LARGE config orgs org-services XIAN user-identification group-mapping-profiles map-profile LARGE-LAN-172.16.110.201-Group-Profile group-include-list groups-included CN=Marketting,CN=Users,DC=xian-lab,DC=net ! set devices template LARGE config orgs org-services XIAN security captive-portal expiration-time 30 set devices template LARGE config orgs org-services XIAN security captive-portal anchoring ip-address-based set devices template LARGE config orgs org-services XIAN security captive-portal service-endpoints service-endpoints XIAN-LAN-VR http-port 44490 set devices template LARGE config orgs org-services XIAN security captive-portal service-endpoints service-endpoints XIAN-LAN-VR https-port 44991 set devices template LARGE config orgs org-services XIAN security captive-portal service-endpoints service-endpoints XIAN-LAN-VR ip-addresses [ 172.16.120.2 ] set devices template LARGE config orgs org-services XIAN security captive-portal service-endpoints service-endpoints XIAN-LAN-VR cookie-auth-profile KERBEROS-AUTHENTICATION-PROFILE ! set devices template LARGE config orgs org-services XIAN vfp profile HTTPS-PROXY mode transparent set devices template LARGE config orgs org-services XIAN vfp profile HTTPS-PROXY port [ 80 ] set devices template LARGE config orgs org-services XIAN vfp profile HTTPS-PROXY routing-instance-list [ XIAN-LAN-VR ] set devices template LARGE config orgs org-services XIAN vfp profile HTTPS-PROXY lef-profile-default true set devices template LARGE config orgs org-services XIAN vfp profile HTTPS-PROXY parse-response no set devices template LARGE config orgs org-services XIAN vfp profile HTTPS-PROXY parse-request no set devices template LARGE config orgs org-services XIAN vfp profile HTTPS-PROXY honour-pbf false ! set devices template LARGE config orgs org-services XIAN security authentication-policies authentication-group Default-Policy rules authentication-policy BYPASS-LINUX-SERVER rule-disable false set devices template LARGE config orgs org-services XIAN security authentication-policies authentication-group Default-Policy rules authentication-policy BYPASS-LINUX-SERVER match source address address-list [ UBUNTU-SERVER UBUNTU-DESKTOP ] set devices template LARGE config orgs org-services XIAN security authentication-policies authentication-group Default-Policy rules authentication-policy BYPASS-LINUX-SERVER set action no-authenticate set devices template LARGE config orgs org-services XIAN security authentication-policies authentication-group Default-Policy rules authentication-policy BYPASS-LINUX-SERVER set logging false set devices template LARGE config orgs org-services XIAN security authentication-policies authentication-group Default-Policy rules authentication-policy BYPASS-DC-SERVER rule-disable false set devices template LARGE config orgs org-services XIAN security authentication-policies authentication-group Default-Policy rules authentication-policy BYPASS-DC-SERVER match destination address address-list [ DC-DOMAIN-CONTROLLER ] set devices template LARGE config orgs org-services XIAN security authentication-policies authentication-group Default-Policy rules authentication-policy BYPASS-DC-SERVER match application predefined-application-list [ DNS DOMAIN MS_AD ] set devices template LARGE config orgs org-services XIAN security authentication-policies authentication-group Default-Policy rules authentication-policy BYPASS-DC-SERVER set action no-authenticate set devices template LARGE config orgs org-services XIAN security authentication-policies authentication-group Default-Policy rules authentication-policy BYPASS-DC-SERVER set logging false set devices template LARGE config orgs org-services XIAN security authentication-policies authentication-group Default-Policy rules authentication-policy AUTHENTICATE-ALL rule-disable false set devices template LARGE config orgs org-services XIAN security authentication-policies authentication-group Default-Policy rules authentication-policy AUTHENTICATE-ALL match services predefined-services-list [ http ] set devices template LARGE config orgs org-services XIAN security authentication-policies authentication-group Default-Policy rules authentication-policy AUTHENTICATE-ALL set action authenticate set devices template LARGE config orgs org-services XIAN security authentication-policies authentication-group Default-Policy rules authentication-policy AUTHENTICATE-ALL set authentication-profile KERBEROS-AUTHENTICATION-PROFILE set devices template LARGE config orgs org-services XIAN security authentication-policies authentication-group Default-Policy rules authentication-policy AUTHENTICATE-ALL set logging true set devices template LARGE config orgs org-services XIAN security authentication-policies authentication-group Default-Policy rules authentication-policy AUTHENTICATE-ALL set lef-profile-default true set devices template LARGE-BACKUP config orgs org-services XIAN user-identification kerberos-profiles kerberos-profile KERBEROS-PROFILE keytab xian.keytab set devices template LARGE-BACKUP config orgs org-services XIAN user-identification kerberos-profiles kerberos-profile KERBEROS-PROFILE spn HTTP/xian.xian-lab.net@XIAN-LAB set devices template LARGE-BACKUP config orgs org-services XIAN user-identification kerberos-profiles kerberos-profile KERBEROS-PROFILE virtual-url xian.xian-lab.net set devices template LARGE-BACKUP config orgs org-services XIAN user-identification authentication-methods authentication-method LARGE-LAN-172.16.110.201-Auth-Method method ldap LARGE-LAN-172.16.110.201-Profile set devices template LARGE-BACKUP config orgs org-services XIAN user-identification authentication-methods authentication-method KERBEROS-AUTHENTICATION-METHOD method kerberos KERBEROS-PROFILE set devices template LARGE-BACKUP config orgs org-services XIAN user-identification authentication-profiles authentication-profile LARGE-LAN-172.16.110.201-Auth-Profile expiration-time 1 set devices template LARGE-BACKUP config orgs org-services XIAN user-identification authentication-profiles authentication-profile LARGE-LAN-172.16.110.201-Auth-Profile lef-profile-default false set devices template LARGE-BACKUP config orgs org-services XIAN user-identification authentication-profiles authentication-profile LARGE-LAN-172.16.110.201-Auth-Profile caching-mode IP-based set devices template LARGE-BACKUP config orgs org-services XIAN user-identification authentication-profiles authentication-profile LARGE-LAN-172.16.110.201-Auth-Profile expiration-mode inactivity set devices template LARGE-BACKUP config orgs org-services XIAN user-identification authentication-profiles authentication-profile LARGE-LAN-172.16.110.201-Auth-Profile concurrent-login 1 set devices template LARGE-BACKUP config orgs org-services XIAN user-identification authentication-profiles authentication-profile LARGE-LAN-172.16.110.201-Auth-Profile default-method [ LARGE-LAN-172.16.110.201-Auth-Method ] set devices template LARGE-BACKUP config orgs org-services XIAN user-identification authentication-profiles authentication-profile KERBEROS-AUTHENTICATION-PROFILE expiration-time 10 set devices template LARGE-BACKUP config orgs org-services XIAN user-identification authentication-profiles authentication-profile KERBEROS-AUTHENTICATION-PROFILE lef-profile-default true set devices template LARGE-BACKUP config orgs org-services XIAN user-identification authentication-profiles authentication-profile KERBEROS-AUTHENTICATION-PROFILE authentication-type active set devices template LARGE-BACKUP config orgs org-services XIAN user-identification authentication-profiles authentication-profile KERBEROS-AUTHENTICATION-PROFILE caching-mode IP-based set devices template LARGE-BACKUP config orgs org-services XIAN user-identification authentication-profiles authentication-profile KERBEROS-AUTHENTICATION-PROFILE expiration-mode inactivity set devices template LARGE-BACKUP config orgs org-services XIAN user-identification authentication-profiles authentication-profile KERBEROS-AUTHENTICATION-PROFILE concurrent-login 5 set devices template LARGE-BACKUP config orgs org-services XIAN user-identification authentication-profiles authentication-profile KERBEROS-AUTHENTICATION-PROFILE default-method [ KERBEROS-AUTHENTICATION-METHOD ] set devices template LARGE-BACKUP config orgs org-services XIAN user-identification authentication-profiles authentication-profile KERBEROS-AUTHENTICATION-PROFILE proactive-reauth disabled set devices template LARGE-BACKUP config orgs org-services XIAN user-identification ldap-profiles server-profile LARGE-LAN-172.16.110.201-Profile state enabled set devices template LARGE-BACKUP config orgs org-services XIAN user-identification ldap-profiles server-profile LARGE-LAN-172.16.110.201-Profile domain-name xian-lab.net set devices template LARGE-BACKUP config orgs org-services XIAN user-identification ldap-profiles server-profile LARGE-LAN-172.16.110.201-Profile ldap-base CN=Users,DC=xian-lab,DC=net set devices template LARGE-BACKUP config orgs org-services XIAN user-identification ldap-profiles server-profile LARGE-LAN-172.16.110.201-Profile bind-dn CN=Administrator,CN=Users,DC=xian-lab,DC=net set devices template LARGE-BACKUP config orgs org-services XIAN user-identification ldap-profiles server-profile LARGE-LAN-172.16.110.201-Profile bind-password JqJzzLk9MjLmWP0PPC4Dz+iZD6YotTzjo4Q0DZ1iY7nU8WIcWysIomh42vjlTzH1rscCaT/ALLS0jKP+otPLU6IHLH73Vlg1Zb1hFEXQA8UMkZUlEWsEWB33DvudGyuAKcIDD4Tc+dBs9NjJDapWXCbS9OQBdd49mCtMGnwXly5v8CO73OioBq73CZMV+C6orVkrg4rL5kGN7QhC2JWrKmazGREGEfRbRg14uq2gKfyb8qm98pK7mteES/wNOjh4osckbF2HSncRpKybTY0DJZ3I9y3Yy6WvQRpo7EMJ9iUgAFk/FXYDfGRRqtO87IrnlYfANouNbverhv9tHJ4jwg== set devices template LARGE-BACKUP config orgs org-services XIAN user-identification ldap-profiles server-profile LARGE-LAN-172.16.110.201-Profile server-type active-directory set devices template LARGE-BACKUP config orgs org-services XIAN user-identification ldap-profiles server-profile LARGE-LAN-172.16.110.201-Profile use-ssl disabled set devices template LARGE-BACKUP config orgs org-services XIAN user-identification ldap-profiles server-profile LARGE-LAN-172.16.110.201-Profile search-timeout 30 set devices template LARGE-BACKUP config orgs org-services XIAN user-identification ldap-profiles server-profile LARGE-LAN-172.16.110.201-Profile bind-timeout 30 set devices template LARGE-BACKUP config orgs org-services XIAN user-identification ldap-profiles server-profile LARGE-LAN-172.16.110.201-Profile servers server LARGE-LAN-172.16.110.201-Server ip-address 172.16.110.201 set devices template LARGE-BACKUP config orgs org-services XIAN user-identification ldap-profiles server-profile LARGE-LAN-172.16.110.201-Profile servers server LARGE-LAN-172.16.110.201-Server port 389 set devices template LARGE-BACKUP config orgs org-services XIAN user-identification ldap-profiles server-profile LARGE-LAN-172.16.110.201-Profile servers server LARGE-LAN-172.16.110.201-Server routing-instances XIAN-LAN-VR set devices template LARGE-BACKUP config orgs org-services XIAN user-identification group-mapping-profiles map-profile LARGE-LAN-172.16.110.201-Group-Profile state enabled set devices template LARGE-BACKUP config orgs org-services XIAN user-identification group-mapping-profiles map-profile LARGE-LAN-172.16.110.201-Group-Profile group-object-class group set devices template LARGE-BACKUP config orgs org-services XIAN user-identification group-mapping-profiles map-profile LARGE-LAN-172.16.110.201-Group-Profile group-name name set devices template LARGE-BACKUP config orgs org-services XIAN user-identification group-mapping-profiles map-profile LARGE-LAN-172.16.110.201-Group-Profile group-member memberof set devices template LARGE-BACKUP config orgs org-services XIAN user-identification group-mapping-profiles map-profile LARGE-LAN-172.16.110.201-Group-Profile user-object-class user set devices template LARGE-BACKUP config orgs org-services XIAN user-identification group-mapping-profiles map-profile LARGE-LAN-172.16.110.201-Group-Profile user-name userPrincipalName set devices template LARGE-BACKUP config orgs org-services XIAN user-identification group-mapping-profiles map-profile LARGE-LAN-172.16.110.201-Group-Profile refresh-interval 60 set devices template LARGE-BACKUP config orgs org-services XIAN user-identification group-mapping-profiles map-profile LARGE-LAN-172.16.110.201-Group-Profile ldap-server-profile LARGE-LAN-172.16.110.201-Profile set devices template LARGE-BACKUP config orgs org-services XIAN user-identification group-mapping-profiles map-profile LARGE-LAN-172.16.110.201-Group-Profile group-include-list groups-included CN=Engineering,CN=Users,DC=xian-lab,DC=net set devices template LARGE-BACKUP config orgs org-services XIAN user-identification group-mapping-profiles map-profile LARGE-LAN-172.16.110.201-Group-Profile group-include-list groups-included CN=Marketting,CN=Users,DC=xian-lab,DC=net set devices template LARGE-BACKUP config orgs org-services XIAN security captive-portal expiration-time 30 set devices template LARGE-BACKUP config orgs org-services XIAN security captive-portal anchoring ip-address-based set devices template LARGE-BACKUP config orgs org-services XIAN security captive-portal service-endpoints service-endpoints XIAN-LAN-VR http-port 44490 set devices template LARGE-BACKUP config orgs org-services XIAN security captive-portal service-endpoints service-endpoints XIAN-LAN-VR https-port 44991 set devices template LARGE-BACKUP config orgs org-services XIAN security captive-portal service-endpoints service-endpoints XIAN-LAN-VR ip-addresses [ 172.16.120.2 ] set devices template LARGE-BACKUP config orgs org-services XIAN security captive-portal service-endpoints service-endpoints XIAN-LAN-VR cookie-auth-profile KERBEROS-AUTHENTICATION-PROFILE set devices template LARGE-BACKUP config orgs org-services XIAN vfp profile HTTPS-PROXY mode transparent set devices template LARGE-BACKUP config orgs org-services XIAN vfp profile HTTPS-PROXY port [ 80 ] set devices template LARGE-BACKUP config orgs org-services XIAN vfp profile HTTPS-PROXY routing-instance-list [ XIAN-LAN-VR ] set devices template LARGE-BACKUP config orgs org-services XIAN vfp profile HTTPS-PROXY lef-profile-default true set devices template LARGE-BACKUP config orgs org-services XIAN vfp profile HTTPS-PROXY parse-response no set devices template LARGE-BACKUP config orgs org-services XIAN vfp profile HTTPS-PROXY parse-request no set devices template LARGE-BACKUP config orgs org-services XIAN vfp profile HTTPS-PROXY honour-pbf false set devices template LARGE-BACKUP config orgs org-services XIAN security authentication-policies authentication-group Default-Policy rules authentication-policy BYPASS-LINUX-SERVER rule-disable false set devices template LARGE-BACKUP config orgs org-services XIAN security authentication-policies authentication-group Default-Policy rules authentication-policy BYPASS-LINUX-SERVER match source address address-list [ UBUNTU-SERVER UBUNTU-DESKTOP ] set devices template LARGE-BACKUP config orgs org-services XIAN security authentication-policies authentication-group Default-Policy rules authentication-policy BYPASS-LINUX-SERVER set action no-authenticate set devices template LARGE-BACKUP config orgs org-services XIAN security authentication-policies authentication-group Default-Policy rules authentication-policy BYPASS-LINUX-SERVER set logging false set devices template LARGE-BACKUP config orgs org-services XIAN security authentication-policies authentication-group Default-Policy rules authentication-policy BYPASS-DC-SERVER rule-disable false set devices template LARGE-BACKUP config orgs org-services XIAN security authentication-policies authentication-group Default-Policy rules authentication-policy BYPASS-DC-SERVER match destination address address-list [ DC-DOMAIN-CONTROLLER ] set devices template LARGE-BACKUP config orgs org-services XIAN security authentication-policies authentication-group Default-Policy rules authentication-policy BYPASS-DC-SERVER match application predefined-application-list [ DNS DOMAIN MS_AD ] set devices template LARGE-BACKUP config orgs org-services XIAN security authentication-policies authentication-group Default-Policy rules authentication-policy BYPASS-DC-SERVER set action no-authenticate set devices template LARGE-BACKUP config orgs org-services XIAN security authentication-policies authentication-group Default-Policy rules authentication-policy BYPASS-DC-SERVER set logging false set devices template LARGE-BACKUP config orgs org-services XIAN security authentication-policies authentication-group Default-Policy rules authentication-policy AUTHENTICATE-ALL rule-disable false set devices template LARGE-BACKUP config orgs org-services XIAN security authentication-policies authentication-group Default-Policy rules authentication-policy AUTHENTICATE-ALL match services predefined-services-list [ http ] set devices template LARGE-BACKUP config orgs org-services XIAN security authentication-policies authentication-group Default-Policy rules authentication-policy AUTHENTICATE-ALL set action authenticate set devices template LARGE-BACKUP config orgs org-services XIAN security authentication-policies authentication-group Default-Policy rules authentication-policy AUTHENTICATE-ALL set authentication-profile KERBEROS-AUTHENTICATION-PROFILE set devices template LARGE-BACKUP config orgs org-services XIAN security authentication-policies authentication-group Default-Policy rules authentication-policy AUTHENTICATE-ALL set logging true set devices template LARGE-BACKUP config orgs org-services XIAN security authentication-policies authentication-group Default-Policy rules authentication-policy AUTHENTICATE-ALL set lef-profile-default true





