Configuring and Verifying Destination NAT

Destination NAT
Network Address Translation (NAT) is the process of mapping IP addresses belonging to one address space into another.
Destination NAT or popularly referred to as DNAT is a method of transparently changing the destination IP address of a packet and inturn performing inverse function for the replies.
DNAT is widely used when you want a service available on a Private DMZ network to be publically accessible – e.g: a WebServer
This article explains how to configure Destination NAT in Versa’s VOS.
High Level Topology
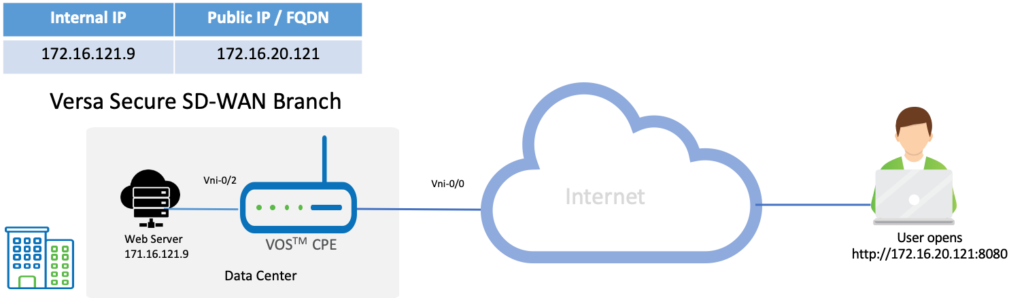
In this topology, we have an external user from the Internet trying to access a WebServer connected behind a Versa SD-WAN appliance. The user uses the external or the Public IP of the WebServer to access the resources.
Configuration
Objectives:
A. Configure a Destination NAT rule on the appliance
B. Verify if an external user is able to access the WebServer using the Public IP
CGNAT related configuration is located under the Configuration > Services Tab.
Step 1: Configure a CGNAT Pool
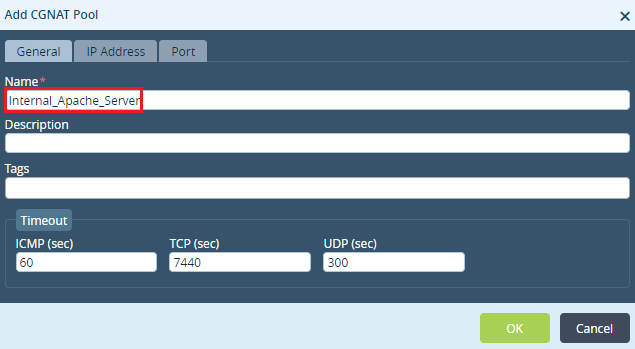
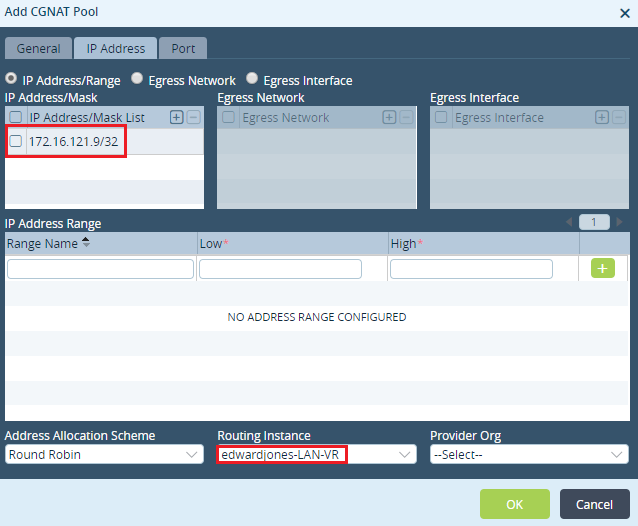
Step 2: Map the IP of the host - '172.16.121.9/32'in the CGNAT pool created above.
In Destination NAT, the CGNAT pool refers to the untranslated IP address of the host / network. These are Private IP addresses given to the hosts / servers which reside inside the network DMZ and will be accessed publicly using a Public IP address.
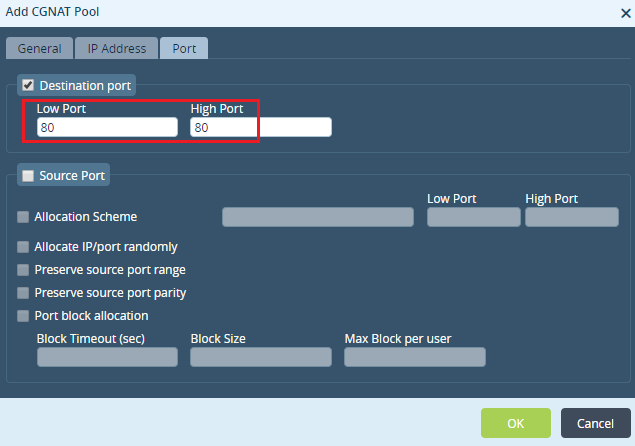
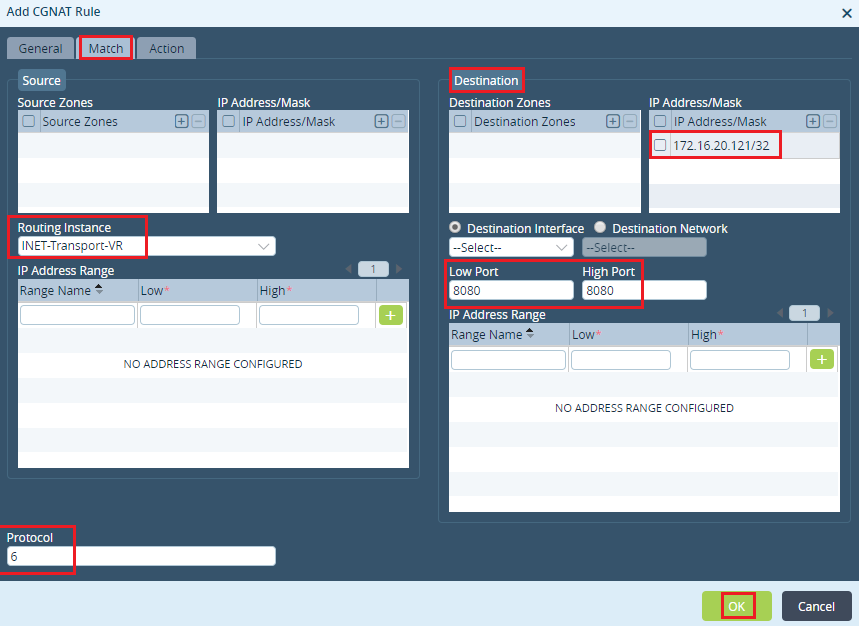
Step 3: Under the 'Port' tab - Check the 'Destination port' - Give the 'Low' and High 'Port' as '80' as we are usign a WebServer in this use case.
Step 4: Conifgure CGNAT Rule
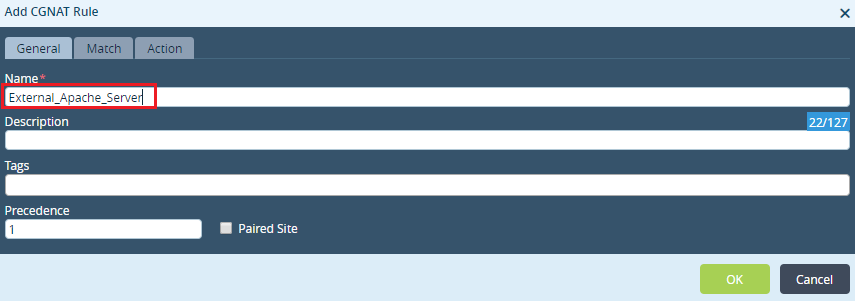
Step 5: Configure Public IP of Server in 'Destination'.
The Port Provided here can be different from that which the internal server is actually listening on. Enterprises can use this for additional security.
VOS automatically handles the Port Forwarding.
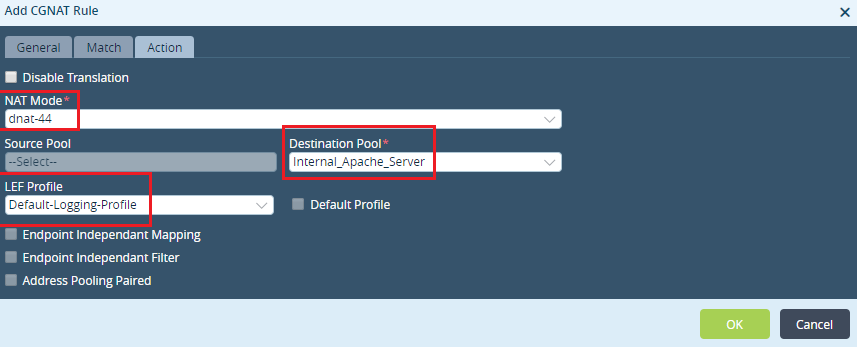
Step 6: Choose the NAT Mode as 'dnat-44' and map the destination pool created in Step 1 here. Logging can be enable to view the sessions in Analytics logs.
Verification
When an external user tries to access the WebServer using the Public IP, the public IP gets translated to the Private (internal Server IP).
The CLI logs of the outbound session show the NAT where the Remote user with an host IP of 10.40.146.204 is using https://172.16.20.121:8080 and the Versa SD-WAN appliance translates this to https://172.16.121.9:80
admin@Spoke1-edwardjones-cli> show orgs org edwardjones sessions nat brief NAT NAT NAT VSN VSN SESS DESTINATION SOURCE DESTINATION NAT SOURCE DESTINATION SOURCE DESTINATION ID VID ID SOURCE IP IP PORT PORT PROTOCOL NATTED SDWAN APPLICATION IP IP PORT PORT ----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- 0 2 6474 10.40.146.204 172.16.20.121 51767 8080 6 Yes No http 10.40.146.204 172.16.121.9 51767 80 [ok][2019-07-05 12:34:30] admin@Spoke1-edwardjones-cli>
Summary
In this article we saw how to configure Destination NAT and verify the logs on CLI.

