Configuring Intrusion Detection and Prevention

In this article, we will understand what is a security vulnerability and how can a corporate network be protected from it by using Versa Secure SD-WAN’s IDS and IPS protection feature.
A security vulnerability is an unintended flaw that allows malicious users to surreptitiously attack a network. Attackers can exploit such vulnerabilities to break into and damage the network by changing, destroying, or stealing secured or confidential information, or by installing malware.
To protect a network against security vulnerabilities, Versa VOS’s unified threat management (UTM) capabilities include intrusion detection and prevention (IDP). IDP is a preemptive approach to network security that identifies potential threats and responds to them based on user-defined policy. IDP comprises two components:
- Intrusion Detection System (IDS) where the network is examined for any indications of vulnerabilities and detect inappropriate and anomalous activities.
- Intrusion Prevention System (IPS) where the system responds to inappropriate and anomalous thereby blocking the vulnerabilities.
Responses can include dropping data packets and disconnecting connections that are transmitting unauthorized data.
You commonly place an IPS system at the perimeter of a corporate network. IPS performs the following types of vulnerability detection to help prevent attacks, including zero-day attacks such as worms or viruses:
- Signature-based detection – Signatures are a set of rules that a vulnerability profile uses to detect intrusive activities. With signature-based detection, a security profile compares a software or application pattern with a database of signatures, identifying malicious activity by matching patterns to those in the database. Versa security packs (SPacks) provide a set of predefined signatures, and you can also create custom signatures.
- Anomaly detection – Anomaly detection monitors a network for unusual events or trends. You configure the vulnerability profile that compares an observed event with the baseline of the normal traffic. Anomaly detection detects patterns that are normally not present in the traffic and is useful for detecting new attacks.
Before we get into configuring the IDS, it is a good to have an understanding of the different IDS / IPS terminologies.
| True Positive | A legitimate attack which triggers to produce an alarm. Example: You have a brute force alert, and it creates a trigger. You investigate the alert and find out that somebody was indeed trying to break into one of your systems via brute force methods. |
| True Negative | An event when no attack has taken place and no detection is made. No attack occurred and your rule didn’t fire. |
| False Positive | IDS classified the BENIGN packet as malicious. An event signaling to produce an alarm when no attack has taken place. Example: You investigate another of these brute force alerts, and find out that it was just some user who had wrongly entered his/her password a bunch of times, not a real attack. |
| False Negative | IDS classified the MALICIOUS packet as benign. No alarm is raised when an attack has actually taken place. Example: There actually was someone trying to break into your system, but they did so below the threshold of your brute force attack logic. For example, you set your rule to look for 10 failed login attempts in a minute, and the attacker did only 9. The attack occurred, but your rule failed to detect it. |
| CVE | CVE stands for Common Vulnerability Enumeration, which is a dictionary of publicly known information security vulnerabilities and exposures. |
| CVSS | CVSS stands for Common Vulnerability Scoring System, which provides a score to indicate the severity of the CVE vulnerabilities. |
| Confidence | Versa recommends using a “Higher” value against the Confidence parameter. Every signature can potentially catch “True positive” (malicious traffic) and trigger “False positive” (benign traffic incorrectly get identified as malicious traffic) . Every signature has “confidence” field. The higher the value, the more confident we are that this signature will only catch “True positive” and not trigger “False positive”. |
High-Level Topology
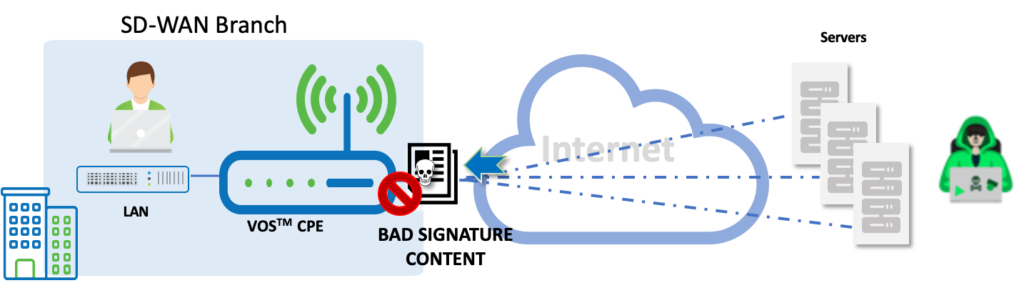
Configuration
We will configure IDS and IPS using the Versa Recommended Profile and see how it protects the user or the LAN form security vulnerabilities. We will also see how to analyze this using Versa Analytics.
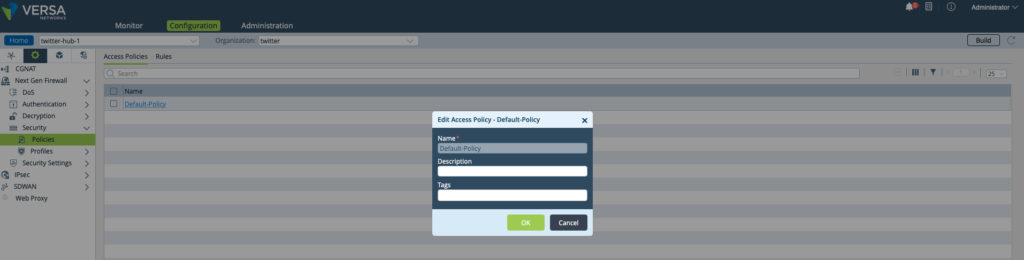
Step 1: Create a Security Policy - 'Default Policy'
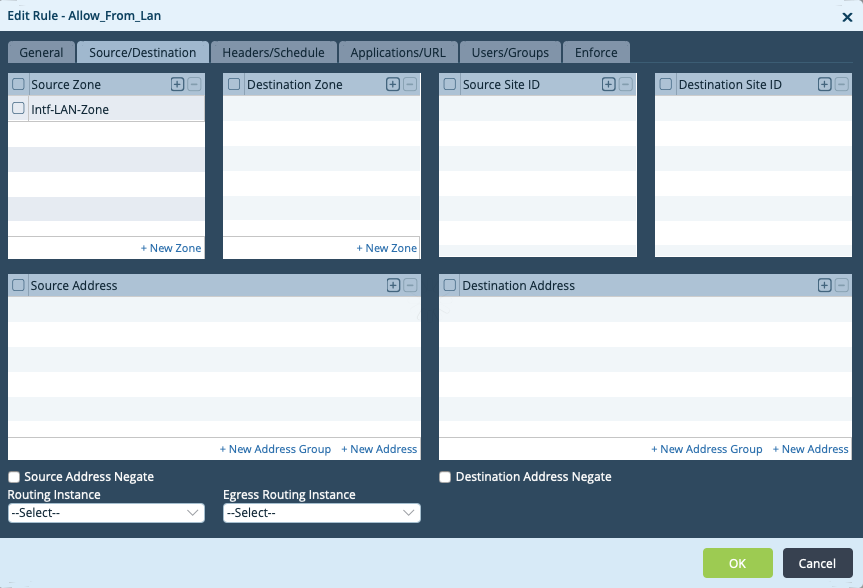
Step 2: Add a new Rule - 'Allow_From_Lan' - Specify the source as the LAN Network
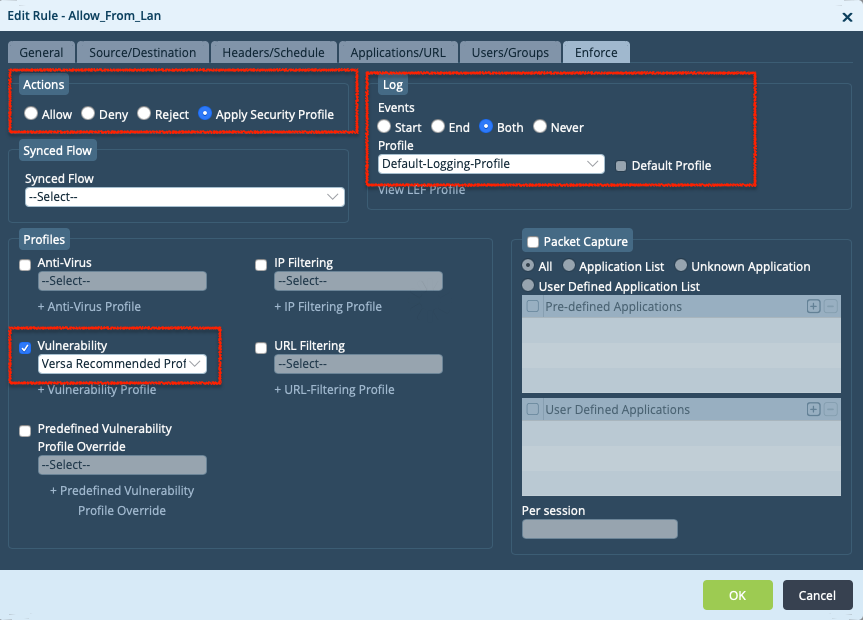
Step 3: In the 'Enforce tab' configure - Actions to 'Apply Security Profile' - Choose 'Versa Recommended Profile' - Enable logging
Verification
Versa IDS/IPS statistics and logs can be viewed on CLI and on GUI using Versa Analytics.
Once we enable IDS/IPS Profile, VOS will start compiling the Signatures. You can view the status of the compile-time using the CLI or the VD GUI
admin@twitter-hub1-cli> show security ips compile-status IGNORE LOAD IGNORE FAIL BRIEF LOAD IPS IPS FAIL IPS APPID APPID APPID COMPILE STATUS SIGNATURE SIGNATURE SIGNATURE SIGNATURE SIGNATURE SIGNATURE TIME ------------------------------------------------------------------------------------------------------------------------------- Ready 16914 12338 3 0 89 0 00:01:06 FILE LINE SID ERROR ----------------------------------------------------------------------------------- - 16405 4000137 Flowbit dependency failed - 27841 1181204012 Flowbit dependency failed - 34009 3000137 Flowbit dependency failed [ok][2020-01-15 10:44:10] admin@twitter-hub1-cli>
On the GUI, it can se seen on the Monitor tab under NGFW > Vulnerability > IPS Compile Status
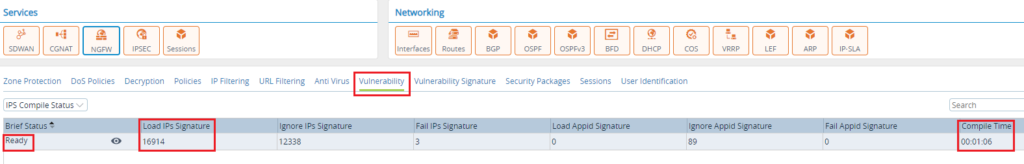
From the above logs, you can see that the VOS has compiled close to 17,000 IDS/IPS Signatures.
To trigger the IDS/IPS mechanism on VOS, we will trigger an attack from the Windows client connected to the LAN by running a test via https://http-evader.semantic-gap.de.
Verification via Monitor Tab
On the Appliance Monitor tab, we can see the number of Sessions incrementing under the “Vulnerability” tab.
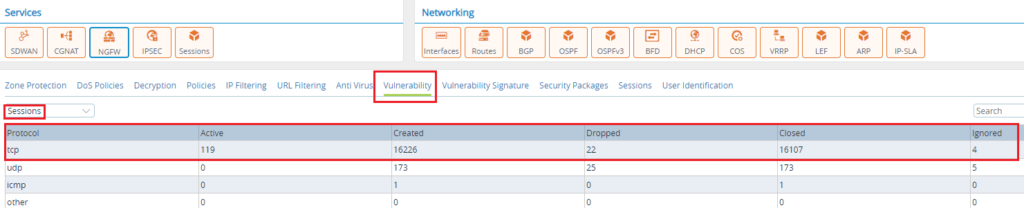
Verification of Analytics Log File
In the log files, we can see that the IDS/IPS module is intercepting the malicious traffic and rejecting it.
| Jan 20th 2020, 07:41:54 PM, EST | 2020-01-16T19:41:54+0000 idpLog, applianceName=twitter-hub1, tenantName=twitter, flowId=33938809, flowCookie=1579203751, signatureId=100092, groupId=1, signatureRev=0, vsnId=0, applianceId=1, tenantId=2, moduleId=11, signaturePriority=2, idpAction=reject, signatureMsg=”HTTP Anomaly invalid_command_format”, classMsg=”Potentially Bad or Protocol Anomaly Traffic”, threatType=bad-traffic, packetTime=01/16/2020-11:41:52.877550, HitCount=1, ipsProfile=Versa Recommended Profile, ipsProfileRule=Attack Severity Rule Filter, ipsDirection=ToClient, ipsProtocol=TCP, ipsApplication=http |
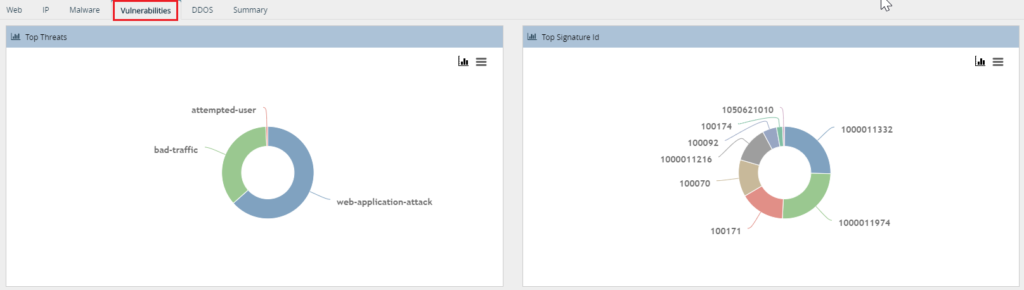
Verification via Analytics Tab
On the Analytics GUI, we can verify/confirm top threats/top signature ID hit using the IDP Log tab.
The rule hit count can be viewed under Security > Threats > Vulnerabilities
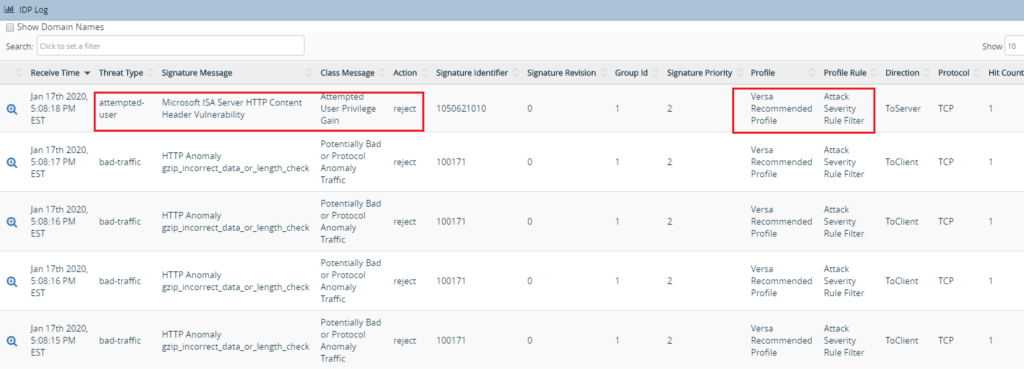
The logs menu on the the Analytics give the details of all sessions that have been intercepted by the IDS/IPS module and the action taken.
Summary
In this article, we saw how to enable IDS/IPS protection on the Versa VOS and how to verify the logs on Versa Analytics. We can create custom vulnerability IPS signature that includes with both predefined and custom signatures. A VOS device scans the network traffic for both predefined and custom vulnerabilities and enforces the configured security action if a match is found.

