Security – Configuring and Verifying Reputation Based Filtering

Reputation Based Filtering
When traffic passes through the network there is a huge possibility of certain IP addresses are associated with a bad reputation and may cause a security risk to the Enterprise or Network. IP filtering based on attributes like IP reputation and Geo-location ensures that the traffic that passes through the security gateway blocks all such traffic.
The Versa Secure SD-WAN provides the capability to enforce filtering of traffic based not only on IP address but also based on Reputation and Geolocation.
This article explains how to implement IP filtering based on reputation, geographical location, and other known attacks like botnets/phishing/scanners.
High Level Topology
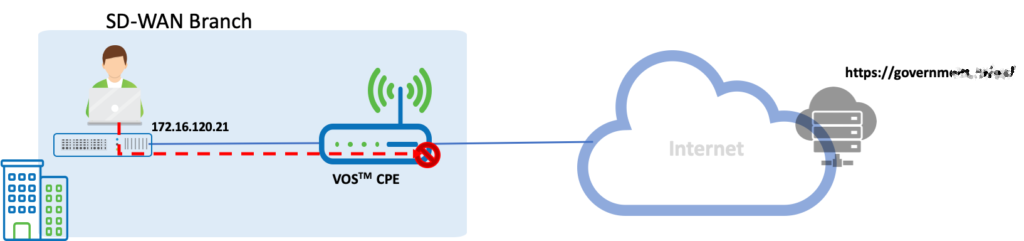
We have a branch LAN behind a Versa SDWAN appliance. The VOS software is configured with reputation-based filtering.
Configuration
Objectives:
A. Configure IP filtering based on reputation and geo-location from certain countries
B. Configure policies to block botnets, phishing and windows exploits
IP filtering can be configured in the Services Menu at Services > Security > Profiles > IP Filtering
The Default Policy action is to allow all – take no action against any IP sources or destinations.
Before we go into the configuration, we will understand the precedence in the IP filtering methods. The methods in order of preference from highest to lowest are
| 1 | Blacklist |
| 2 | Whitelist |
| 3 | Geo IP Based Action |
| 4 | Reputation Based Actions |
| 5 | Address Reverse Lookup |
There are two components to this
| IP Filtering Rule | Define the IPs and sources that need to be blocked |
| Security Policy | Map the IP Filtering Rule created above in a Security Policy |
We will now look at the step by step configuration of reputation based filtering.
Step 1: Create a IP Filtering Policy - Set the default action to 'Allow' - Choose the LEF Profile as 'Default-Logging-Profile'
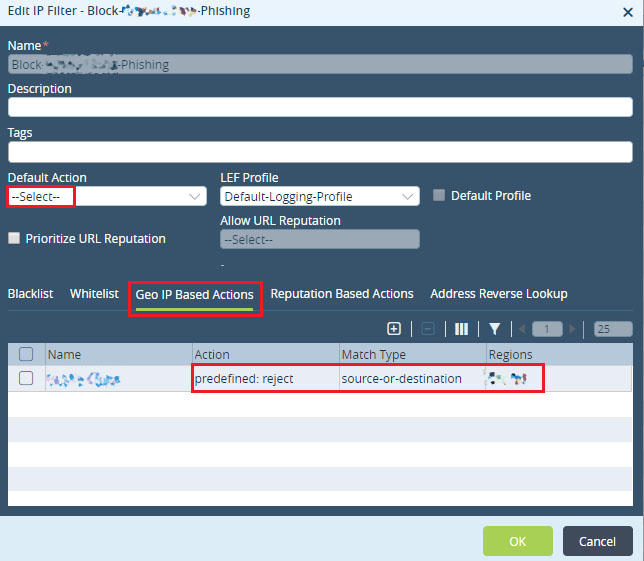
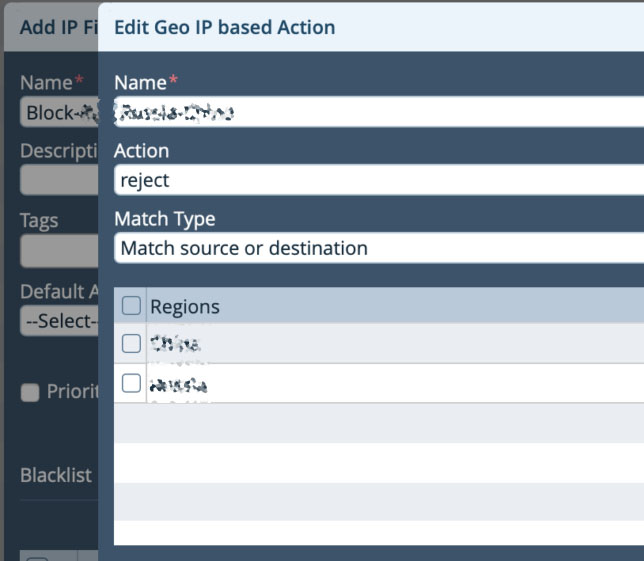
Step 2: Choose 'Geo IP Based Actions' - create a new Rule to match IPs belonging to the two regions which need to be blocked. - Since the default action is blank, it will allow all IPs. So a specific has to be defined inside the rule and in this case we will choose 'reject'
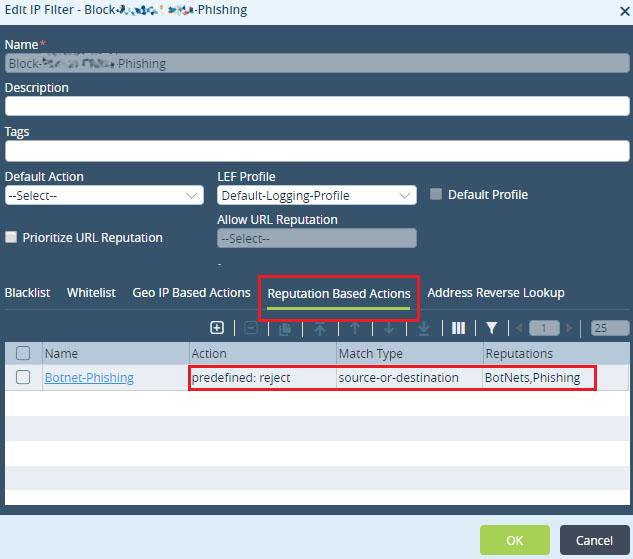
Step 2: Configure 'Reputation Based Actions' and add a rule to block BotNets and Phishing content. - Choose predefined actions as 'reject'
Step 3: Associate the IP Filtering rule created above to a security Policy - Choose 'Apply Security Profile' - Enable to logging using the 'Default-Logging-Profile' - Create a Rule with Source as LAN and map the IP filtering rule created above under 'IP Filtering'
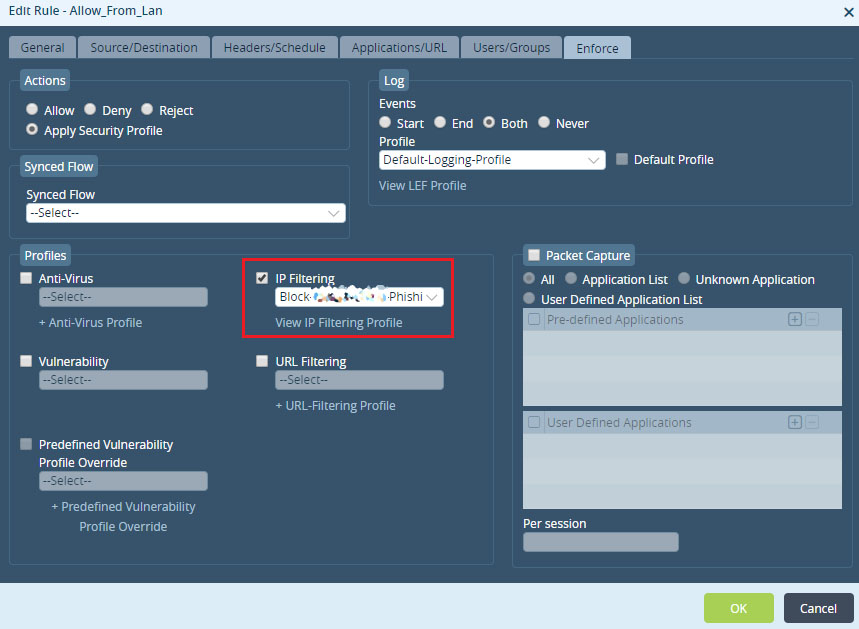
Verification
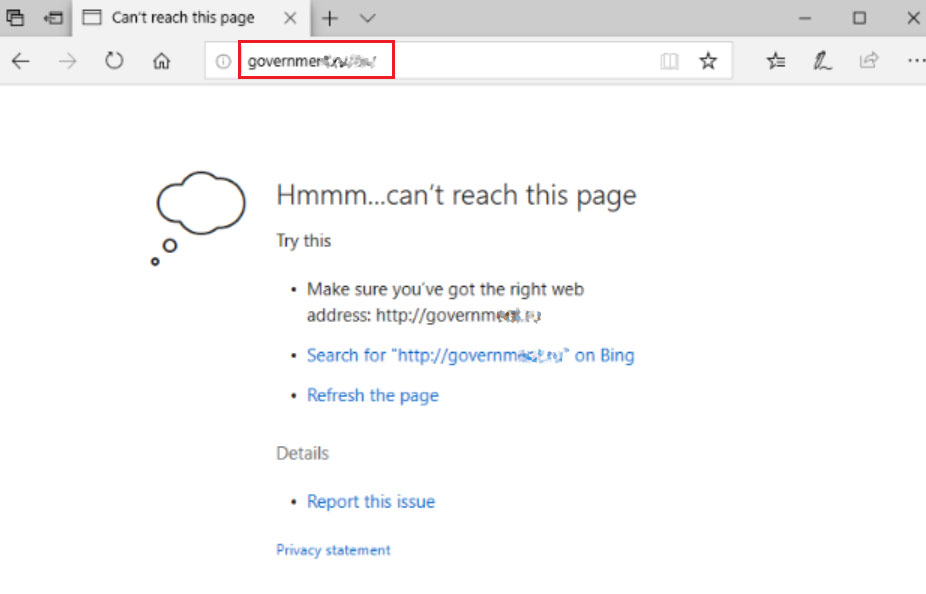
After applying the policy, when the user initiates traffic towards any of the sites in the countries specified in the rule, we see that the traffic is blocked.
Here the user is initiating traffic to the URL https://governmexxxx/xx/
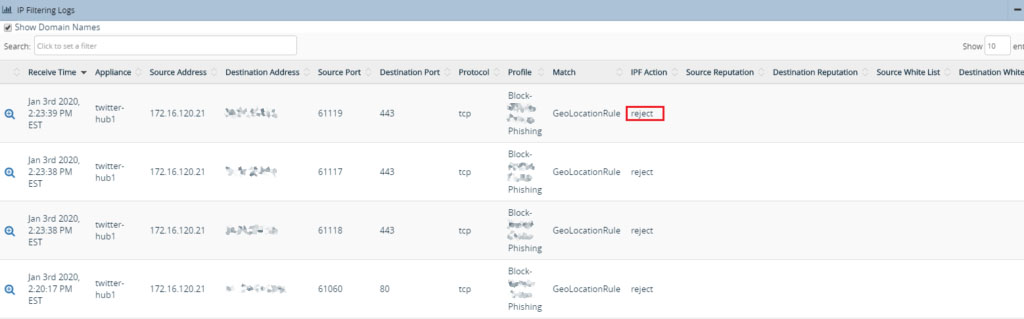
The site is blocked. And the Analytics IP Filtering log show the source and destination and the action taken by the VOS. It also shows details of the rule under which it is getting blocked.
Summary
In this article, we saw how to configure reputation and geo-location-based filtering policies. The policy can be more granularly defined by using the blacklisting, whitelisting options, and tweaking the default action behavior to suit the specific customer needs.

