Configure and Verify Basic NAT – Enterprise

Basic NAT – Single Enterprise on Versa SD-WAN
Network Address Translation (NAT) is the process of mapping IP addresses belonging to one address space into another.
A Basic NAT is one where a router has an inside (typically a LAN) interface and outside (Internet) interface. A one to one NAT maps an internal (inside) IP address towards an external (outside) IP address.
Versa Secure SD-WAN supports various types of NAT – Basic one to one NAT, One to many NAT (PAT), Twice basic NAT, Destination NAT and Dynamic NAT.
This article explains how to configure a Basic NAT (one to one) on Versa Operating System having a Single Tenant – i.e., no Parent-Child organization relationship as the case would be in a Service Provider environment.
High Level Topology
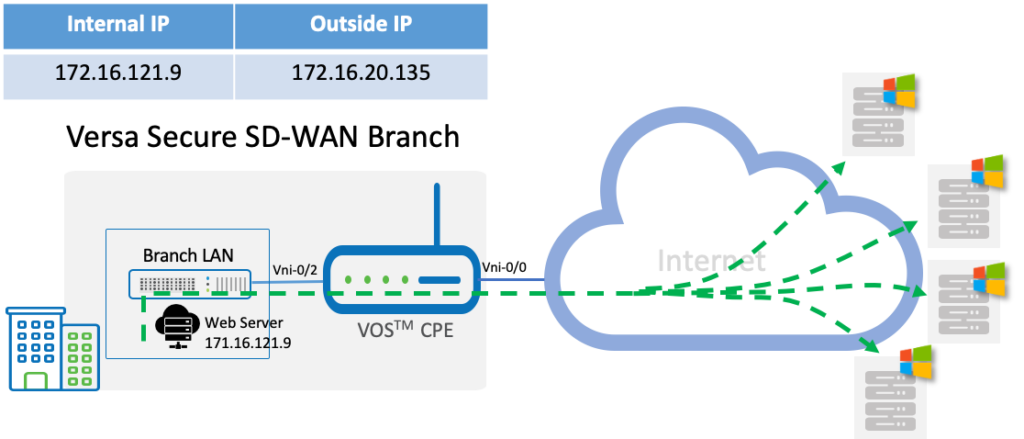
The topology here has a web server that is on a customer LAN environment that needs access to the Internet to download patches, updates, etc.
Versa Operating System when performing Basic NAT automatically creates a bi-directional NAT entry.
Configuration
Objectives:
A. Define a CGNAT pool – the Outside IP address to which the Internal server address will be translated to while accessing the Internet
B. Create a CGNAT rule to match the source address of the internal machine and map it to the CGNAT pool and define the type of NAT.
Step 1: Create a CGNAT Pool
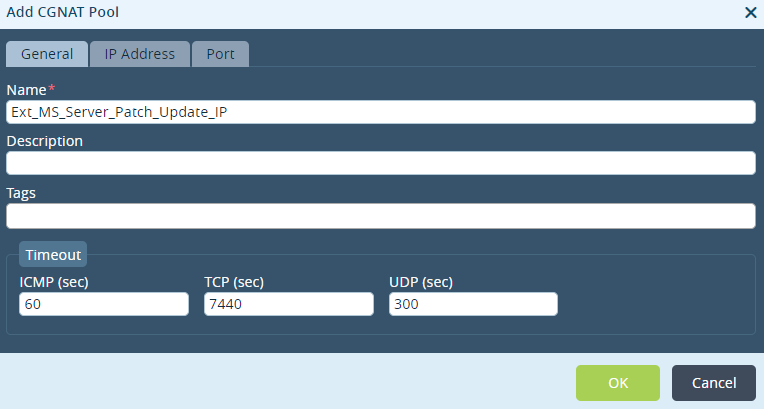
Step 2: Configure the Outside IP address of the NAT pool created above and choose the routing instance as 'INET-Transport-VR'
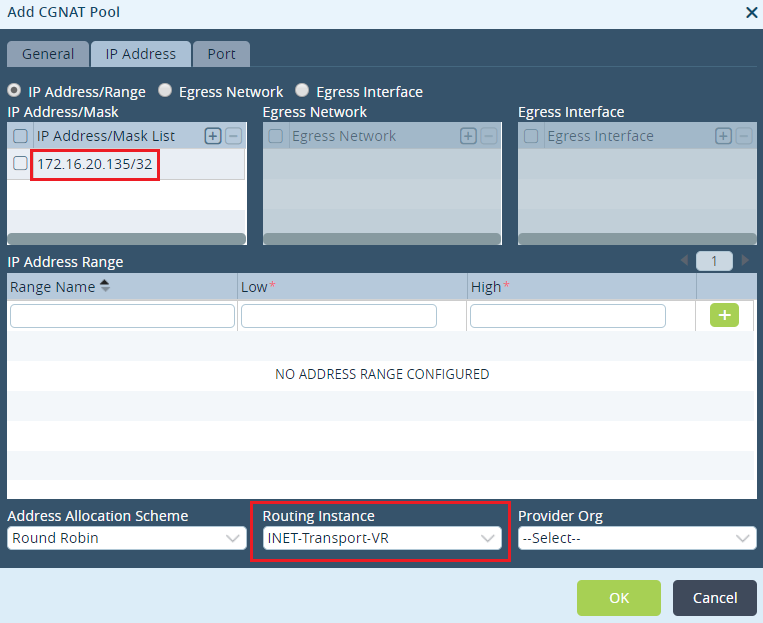
Step 3: In the 'Port' tab, do not choose any source or destination ports as this is not required for this use case. Click on 'Ok' to create the CGNAT pool.
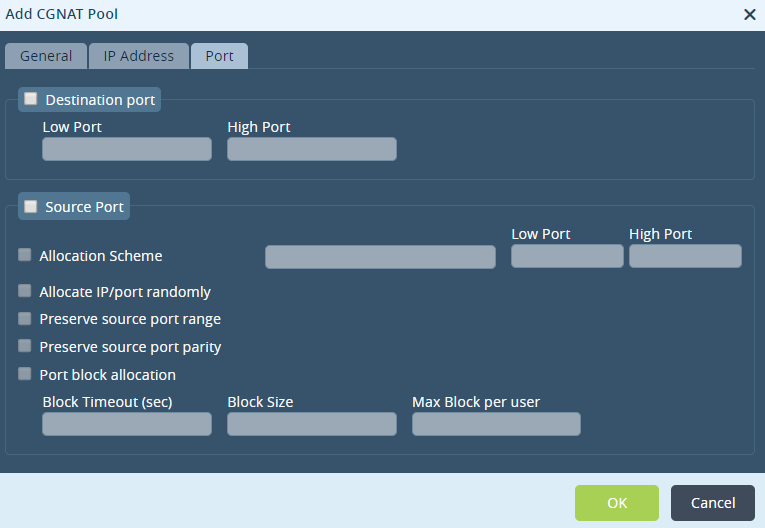
Step 4: Define a CGNAT rule name

Step 5: Match the IP address of the Internal Server that has to be Natted
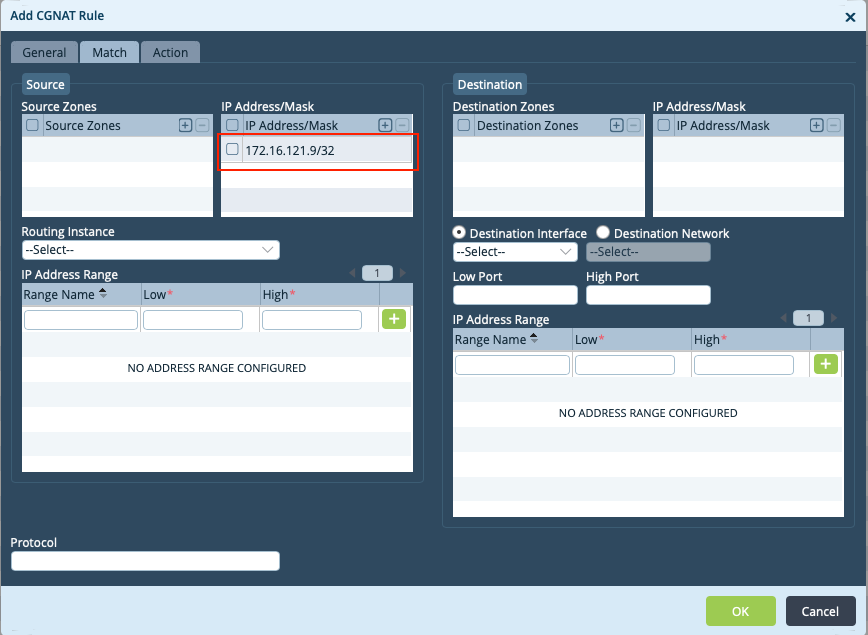
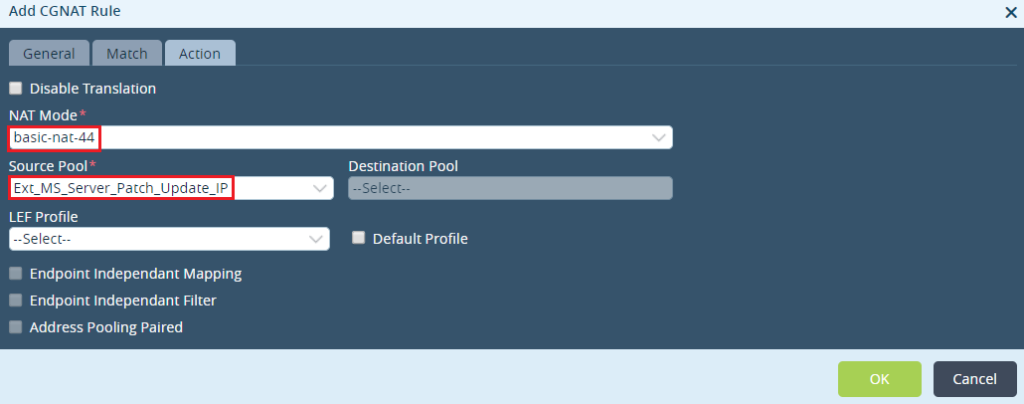
Step 6: Define the type of NAT to be done. In this case choose 'basic-nat-44' and then select the Source NAT pool created earlier 'Ext_MS_Server_Patch_Update_IP'
Verification
The NAT translations can be verified on the CLI and monitor tabs. If logging is enabled for the NAT translations, the logs will be available on the Analytics under the CGNAT tab.
Here the source IP of the machine 172.16.121.9 accessing the Internet is translated to the IP 172.16.20.135.
admin@Hub-Twitter-cli> show orgs org twitter sessions nat brief NAT NAT NAT VSN VSN SESS DESTINATION SOURCE DESTINATION NAT SOURCE DESTINATION SOURCE DESTINATION ID VID ID SOURCE IP IP PORT PORT PROTOCOL NATTED SDWAN APPLICATION IP IP PORT PORT ----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- 0 2 514 172.16.121.9 8.8.8.8 55107 53 17 Yes No dns 172.16.20.135 8.8.8.8 55107 53 0 2 522 172.16.121.9 23.220.168.116 57961 443 6 Yes No akamai 172.16.20.135 23.220.168.116 57961 443 0 2 523 172.16.121.9 23.220.168.116 57962 443 6 Yes No akamai 172.16.20.135 23.220.168.116 57962 443 0 2 169 172.16.121.9 184.51.49.106 57712 443 6 Yes No http2 172.16.20.135 184.51.49.106 57712 443 0 2 358 172.16.121.9 8.8.8.8 52404 53 17 Yes No dns 172.16.20.135 8.8.8.8 52404 53 0 2 401 172.16.121.9 184.51.49.106 57871 443 6 Yes No http2 172.16.20.135 184.51.49.106 57871 443 0 2 515 172.16.121.9 40.90.23.209 57955 443 6 Yes No windowslive 172.16.20.135 40.90.23.209 57955 443 [ok][2019-07-05 12:34:30] admin@Hub-Twitter-cli>
The bi-directional NAT sessions are also automatically formed.
Even though there was no prior NAT session from Inside to Outside, the Internet user is able to reach the user 172.16.121.9 by referring to its outside IP 172.16.20.135. So the Basic NAT automatically creates and Inbound NAT session.
admin@Hub-Twitter-cli> show orgs org twitter sessions nat brief NAT NAT NAT VSN VSN SESS DESTINATION SOURCE DESTINATION NAT SOURCE DESTINATION SOURCE DESTINATION ID VID ID SOURCE IP IP PORT PORT PROTOCOL NATTED SDWAN APPLICATION IPIP PORT PORT ----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- 0 2 13458 10.40.146.204 172.16.20.135 30498 30498 1 Yes No icmp 10.40.146.204 172.16.121.9 30498 30498 [ok][2019-07-05 12:34:30] admin@Hub-Twitter-cli>
Analytics logs show the NAT translation details.
| Jul 15th 2020, 11:59:46 AM IST | 2020-07-15T06:29:46Z cgnatLog, tenant=twitter, flowDuration=0, postNAPTDestPort=443, postNAPTSrcPort=57961, destPort=443, natEvent=nat44-sess-create, srcPort=57961, natRuleName=Internal_MS_Server, destNatPoolName=-, destAddr=23.220.168.116, rcvTimeSec=46, srcAddr=172.16.121.9, protocolId=6, flowKey=0x5f0ea1ce01000200441f, postNATSrcAddr=172.16.20.135, postNATDestAddr=23.220.168.116, at=Thu Jul 16 00:00:00 PDT 2020, deviceKey=-, applianceName=Hub-Twitter, srcNatPoolName=Ext_MS_Server_Patch_Update_IP |
Summary
In this article, we saw how a Basic NAT is configured on the Versa Operating System. More granular control in the NAT can be achieved by defining the Ports as well depending on the use case.

