Configure App Based Traffic Steering over Secure SD-WAN Gateway

SDWAN-Application Based Traffic Steering over Secure SD-WAN Gateways
Application based Traffic Forwarding refers to the process of forwarding application traffic to pre-defined secure Gateways based on the Enterprise needs and network conditions. This is slightly different from Traffic Engineering which is basically routing the traffic on specific available local WAN-links and continually evaluating them for SLA metrics and switching the traffic forwarding to alternate links in case of a SLA violation.
Typical enterprise networks will have a high capacity Internet circuit at their Hub locations and could be having a Firewall or a Proxy in place with controlled Internet access while a local break out at the Branches would be required for SaaS traffic to have a seamless user experience.
Legacy routing uses PBR based forwarding policies which act on layer-3 and forward traffic to appropriate gateways. This isn’t scalable when the applications today are hosted on cloud and new network and servers keep getting added. Versa Secure SD-WAN Application based forwarding capability, gives the flexibility to match and forward traffic based on Layer 3 and right upto Layer 7. This can also be tagged with Traffic Engineering and the traffic can be forwarded to the most optimal Gateway or exit point in the network.
This article will provide information about application based traffic forwarding configuration and verifying the same using Versa SD-WANs CLI and big data Analytics.
Versa SD-WAN Application Based Forwarding is an easy to configure policy and has a single touch point – the SDWAN Policy
| SDWAN Policy | – Define the Application(s) to be matched and forwarding action to be taken – Define the default action for all other Internet bound traffic to be matched and the forwarding action |
High Level Topology
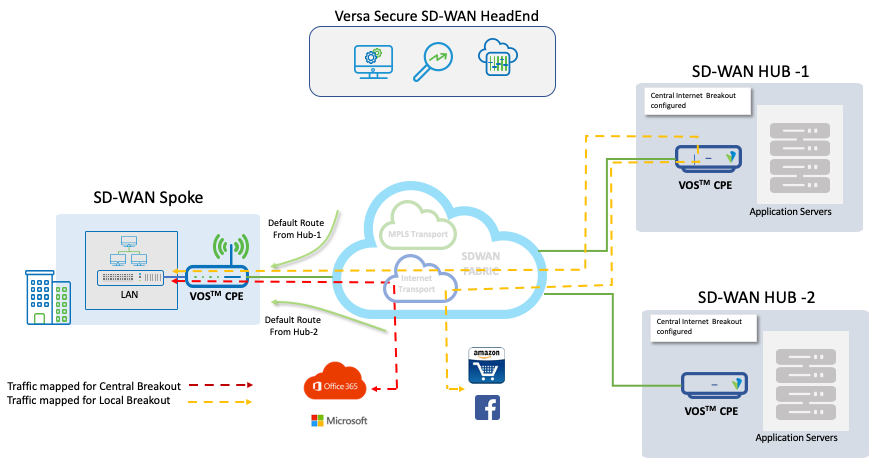
Hubs and the Spoke sites have two Transports enabled – a MPLS and a Internet with a local DIA (Direct Internet Access) break out enabled at all the sites. The Spoke site gets two Default Routes (0.0.0.0/0) – one from Hub-1 and the other from Hub-2 and in addition has its local DIA. The Default routes present in the Spoke with the next Hop towards 10.1.224.102 and 10.1.224.103 represent the Hub-1 and Hub-2 Control-VR-IPs and ‘indirect’ reference in the routing table classifies it as a route is received over the SDWAN fabric.
In steady state the traffic destined for central breakout prefers the SD-WAN Gateway at Hub-1.
admin@T3-Spoke-1-cli> show route routing-instance Tenant-3-LAN-VR Routes for Routing instance : Tenant-3-LAN-VR AFI: ipv4 SAFI: unicast Codes: E1 - OSPF external type 1, E2 - OSPF external type 2 IA - inter area, iA - intra area, L1 - IS-IS level-1, L2 - IS-IS level-2 N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2 RTI - Learnt from another routing-instance + - Active Route Prot Type Dest Address/Mask Next-hop Age Interface name ---- ---- ----------------- -------- --- -------------- BGP N/A +0.0.0.0/0 10.1.224.102 1d03h29m Indirect BGP N/A 0.0.0.0/0 10.1.224.103 1d07h15m Indirect BGP N/A 0.0.0.0/0 169.254.0.2 1d07h04m tvi-0/603.0
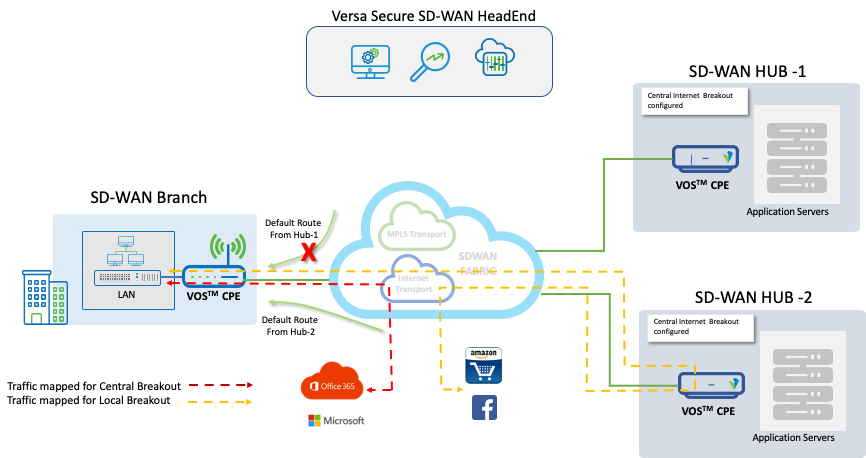
On failure of the Internet circuit at Hub-1, the default route from Hub-1 towards the Spoke is withdrawn and traffic intended for Central breakout will prefer Hub-2 as SD-WAN Gateway.
Configuration
Objectives:
- Configure a default policy for all SDWAN traffic – Branch to Branch
- Configure a Policy use the Hub as Gateway – Hub-1 and in case of failure towards Hub-2 for all traffic matching the applications – Facebook & Amazon
- All other Internet bound traffic should use the local breakout (DIA) at the Spoke site
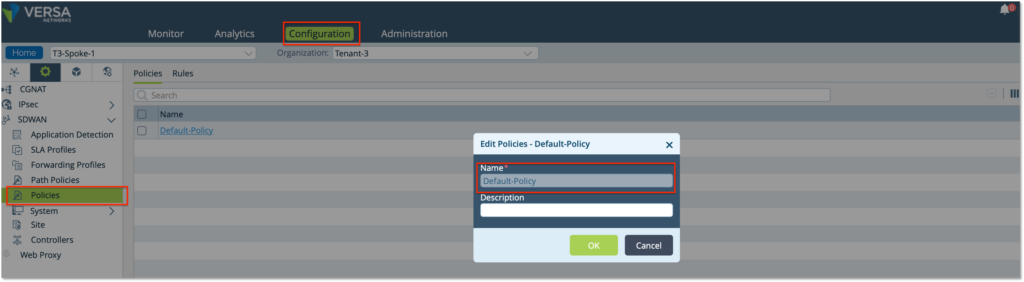
Step 1: Configure a SDWAN Policy. Under the Service Tab, create a SDWAN Policy – ‘Default-Policy’
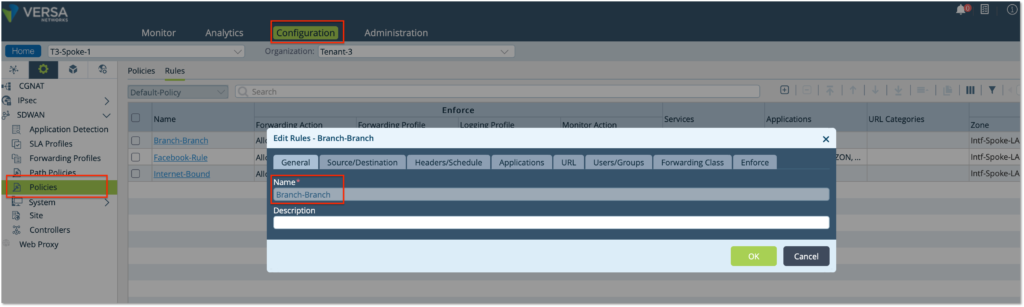
Step 2: Configure a rule for all LAN-to-LAN traffic
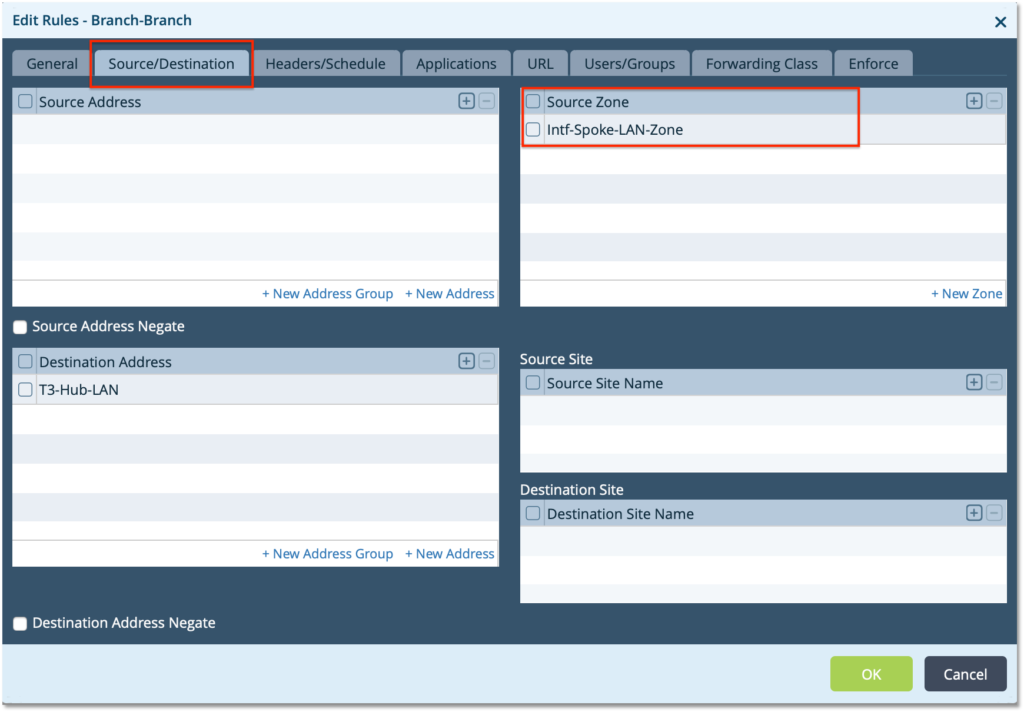
– Create a Rule ‘Branch-Branch’. Choose the source Zone as LAN zone ‘Intf-Spoke-LAN-Zone’ to match all traffic coming from the LAN
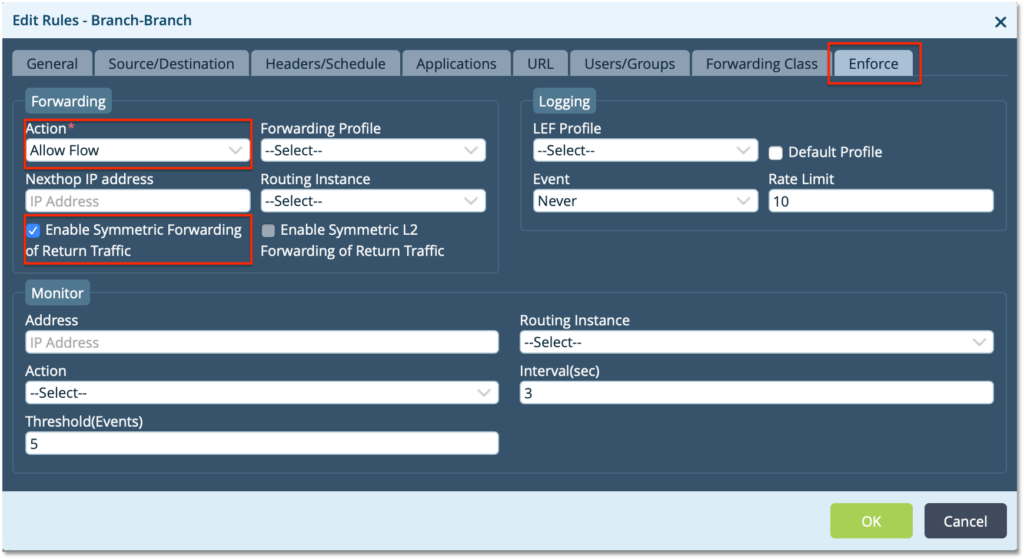
– Use the Enforce tab to define the Action to ‘Allow Flow’ and select ‘Enable Symmetric Forwarding’
Step 3: Configure a rule for all traffic that has to go to the Central – Hub break out. We will match all traffic going to Amazon & Facebook
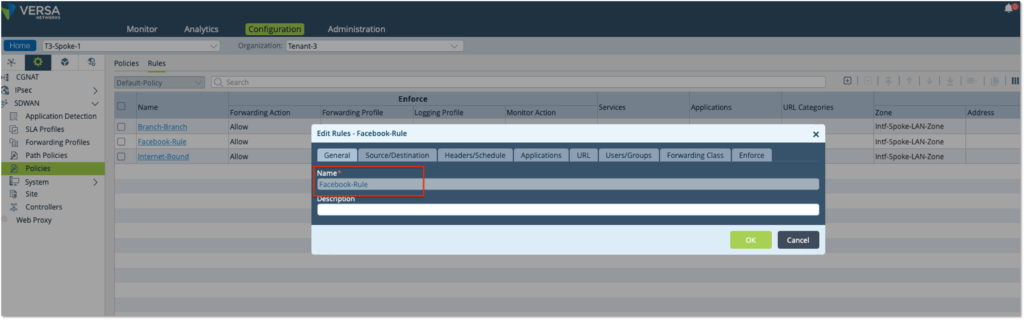
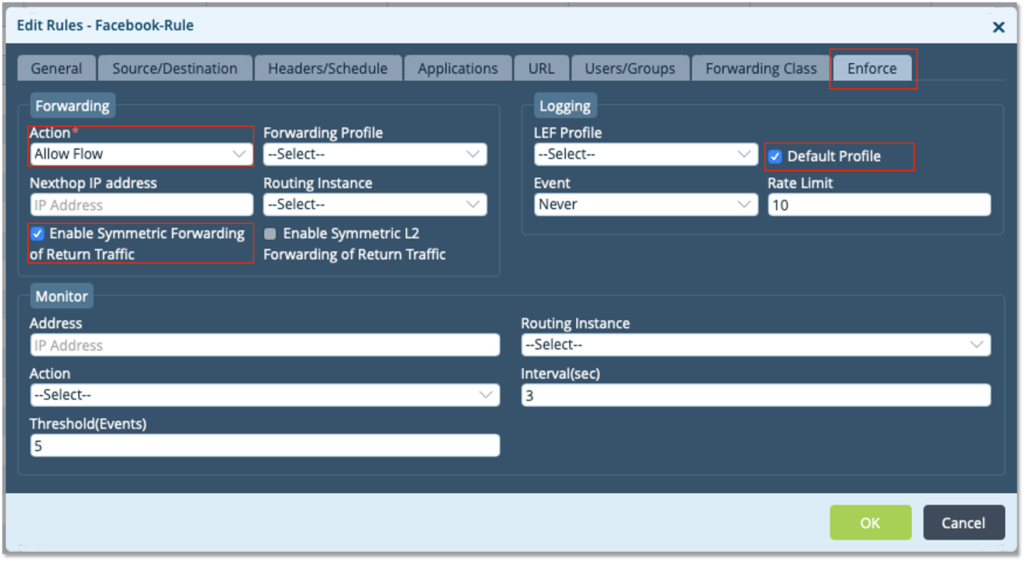
– Create a Rule ‘Facebook-Rule’. Choose the source Zone as LAN zone ‘Intf-Spoke-LAN-Zone’ to match all traffic coming from the LAN
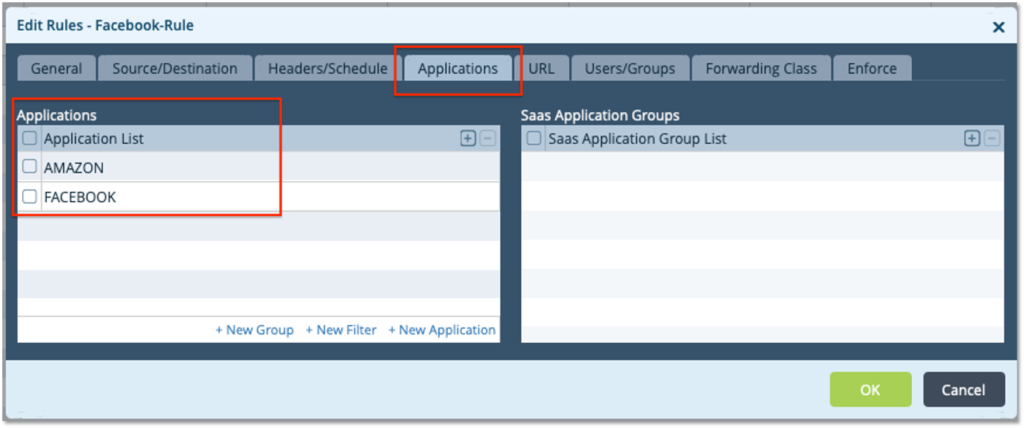
– On the Applications Tab – select ‘Facebook’ and ‘Amazon’
– Use the Enforce tab to define the Action to ‘Allow Flow’ and select ‘Enable Symmetric Forwarding’
– Select ‘Default Profile’ to enable logging and get the Analytics view
Step 4: Configure a rule for all traffic that has to go to the Central – Hub break out. We will match all traffic going to Amazon & Facebook
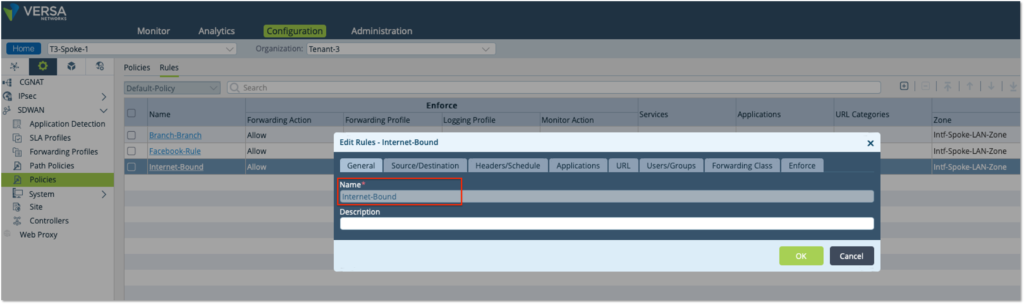
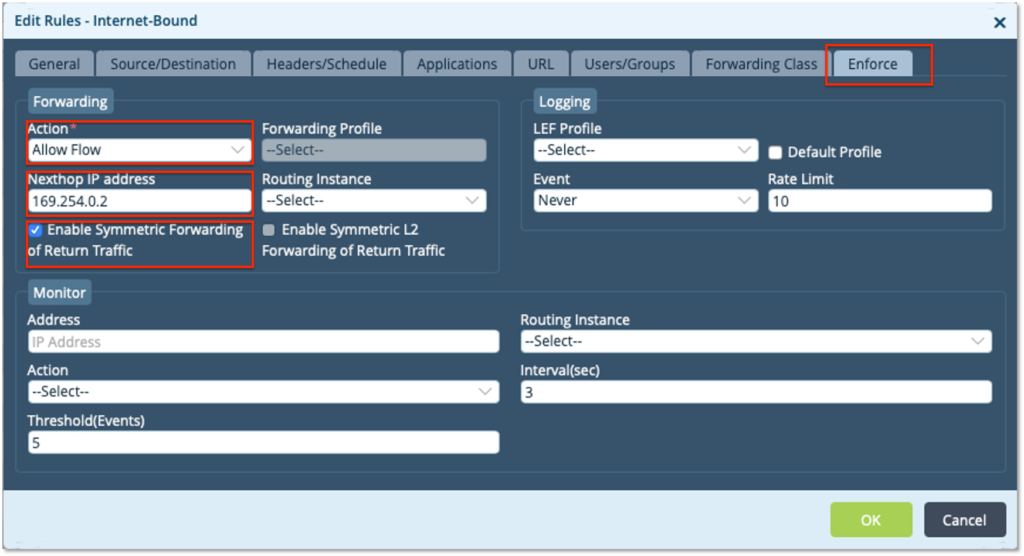
– Create a Rule ‘Internet-Bound’. Choose the source Zone as LAN zone ‘Intf-Spoke-LAN-Zone’ to match all traffic coming from the LAN
– Use the Enforce tab to define the Action to ‘Allow Flow’
– Choose the next hop as ‘169.254.0.2’ (the local DIA breakout) and select ‘Enable Symmetric Forwarding’
– Select ‘Default Profile’ to enable logging and get the Analytics view
Verification
In steady state the traffic towards Facebook & Amazon traffic take the Hub-1 SD-WAN Gateway and all other Internet traffic takes the DIA. CLI output shows the traffic towards Facebook and Amazon as SD-WAN traffic exiting the spoke and reaching Hub-1 and traffic towards other applications like Twitter and Facebook go out as DIA traffic via the local break out.
In the output below, the traffic towards Amazon is going out as SDWAN traffic the from the Branch and not getting NATTED.
admin@T3-Spoke-1-cli> show orgs org Tenant-3 sessions brief | match amazon 0 2 11737 10.10.30.30 13.32.36.24 43262 443 6 No Yes amazon 0 2 11752 10.10.30.30 54.239.26.255 44942 443 6 No Yes amazon 0 2 11764 10.10.30.30 54.239.26.255 44946 443 6 No Yes amazon 0 2 11777 10.10.30.30 54.209.9.51 40738 443 6 No Yes amazon 0 2 11782 10.10.30.30 34.192.208.233 34980 443 6 No Yes amazon [ok][2020-07-14 05:26:06]
admin@T3-Spoke-1-cli> show orgs org Tenant-3 sessions sdwan brief VSN VSN SESS SOURCE DESTINATION TX ID VID ID SOURCE IP DESTINATION IP PORT PORT PROTOCOL NATTED SDWAN APPLICATION RX WAN CKT TX WAN CKT BRANCH ------------------------------------------------------------------------------------------------------------------------------------------------------------ 0 2 11719 52.206.125.160 10.10.30.30 443 40926 6 No Yes - Internet:Internet Internet:Internet T3-Hub-1 0 2 11720 10.10.30.30 13.249.217.20 58232 443 6 No Yes - MPLS:MPLS MPLS:MPLS T3-Hub-1 0 2 11737 10.10.30.30 13.32.36.24 43262 443 6 No Yes amazon Internet:Internet Internet:Internet T3-Hub-1 0 2 11752 10.10.30.30 54.239.26.255 44942 443 6 No Yes amazon MPLS:MPLS MPLS:MPLS T3-Hub-1 0 2 11756 10.10.30.30 52.46.130.13 33778 443 6 No Yes - MPLS:MPLS MPLS:MPLS T3-Hub-1 0 2 11761 10.10.30.30 52.46.135.211 42514 443 6 No Yes - Internet:Internet Internet:Internet T3-Hub-1 0 2 11764 10.10.30.30 54.239.26.255 44946 443 6 No Yes amazon MPLS:MPLS MPLS:MPLS T3-Hub-1 0 2 11777 10.10.30.30 54.209.9.51 40738 443 6 No Yes amazon Internet:Internet Internet:Internet T3-Hub-1 0 2 11782 10.10.30.30 34.192.208.233 34980 443 6 No Yes amazon MPLS:MPLS MPLS:MPLS T3-Hub-1 0 2 11787 10.10.30.30 104.115.92.65 39318 443 6 No Yes - Internet:Internet Internet:Internet T3-Hub-1
admin@T3-Spoke-1-cli> show orgs org Tenant-3 sessions sdwan brief VSN VSN SESS SOURCE DESTINATION TX ID VID ID SOURCE IP DESTINATION IP PORT PORT PROTOCOL NATTED SDWAN APPLICATION RX WAN CKT TX WAN CKT BRANCH ------------------------------------------------------------------------------------------------------------------------------------------------------------ 0 2 11719 52.206.125.160 10.10.30.30 443 40926 6 No Yes - Internet:Internet Internet:Internet T3-Hub-1 0 2 11844 10.10.30.30 13.32.36.24 43300 443 6 No Yes amazon MPLS:MPLS MPLS:MPLS T3-Hub-1 0 2 11866 10.10.30.30 13.249.213.191 44818 443 6 No Yes amazon MPLS:MPLS MPLS:MPLS T3-Hub-1 0 2 11976 10.10.30.30 52.46.141.49 49296 443 6 No Yes amazon MPLS:MPLS MPLS:MPLS T3-Hub-1 0 2 11979 10.10.30.30 157.240.16.35 40536 443 6 No Yes facebook Internet:Internet Internet:Internet T3-Hub-1 0 2 12008 10.10.30.30 31.13.79.26 60246 443 6 No Yes facebook MPLS:MPLS MPLS:MPLS T3-Hub-1 0 2 12021 10.10.30.30 157.240.16.35 40578 443 6 No Yes facebook Internet:Internet Internet:Internet T3-Hub-1
The SDWAN Traffic sessions below show, the traffic to Amazon and Facebook taking the Hub-1 as SD-WAN Gateway to the Internet.
All other Internet bound traffic is taking the local DIA at the Spoke where the traffic is getting Natted and going as a non-SD-WAN traffic and no SD-WAN sessions are built for traffic destined to other Internet sites like Microsoft, Office365, Google etc.
admin@T3-Spoke-1-cli> show orgs org Tenant-3 sessions brief VSN VSN SESS SOURCE DESTINATION ID VID ID SOURCE IP DESTINATION IP PORT PORT PROTOCOL NATTED SDWAN APPLICATION --------------------------------------------------------------------------------------------------------------- 0 2 12074 10.10.30.30 13.90.213.204 41976 80 6 No No office365 0 2 12075 10.10.30.30 13.90.213.204 41976 80 6 Yes No office365 0 2 12080 10.10.30.30 184.84.103.195 45806 443 6 No No office365 0 2 12081 10.10.30.30 184.84.103.195 45806 443 6 Yes No office365 0 2 12086 10.10.30.30 104.115.94.4 55820 443 6 No No microsoft 0 2 12087 10.10.30.30 104.115.94.4 55820 443 6 Yes No microsoft 0 2 12102 10.10.30.30 13.235.101.167 40172 443 6 No No microsoft 0 2 12103 10.10.30.30 13.235.101.167 40172 443 6 Yes No microsoft 0 2 12109 10.10.30.30 104.77.173.32 48436 443 6 No No microsoft 0 2 12112 10.10.30.30 104.77.173.32 48436 443 6 Yes No microsoft 0 2 12182 10.10.30.30 117.18.232.200 46762 443 6 No No windows_azure 0 2 12183 10.10.30.30 117.18.232.200 46762 443 6 Yes No windows_azure 0 2 12284 10.10.30.30 172.217.163.78 37362 443 6 No No youtube 0 2 12285 10.10.30.30 172.217.163.78 37362 443 6 Yes No youtube 0 2 12292 10.10.30.30 172.217.160.131 48630 80 6 No No ocsp 0 2 12293 10.10.30.30 172.217.160.131 48630 80 6 Yes No ocsp 0 2 12316 10.10.30.30 172.217.163.202 36366 443 6 No No google_gen 0 2 12317 10.10.30.30 172.217.163.202 36366 443 6 Yes No google_gen 0 2 12318 10.10.30.30 142.250.67.77 60364 443 6 No No google_accounts 0 2 12319 10.10.30.30 142.250.67.77 60364 443 6 Yes No google_accounts s
On Internet link failure at Hub-1, the SD-WAN automatically withdraws the default route from Hub-1 and make that out of Hub-2 as indicated by the next hop of 10.1.224.103 as the best path.
admin@T3-Spoke-1-cli> show route routing-instance Tenant-3-LAN-VR Routes for Routing instance : Tenant-3-LAN-VR AFI: ipv4 SAFI: unicast Codes: E1 - OSPF external type 1, E2 - OSPF external type 2 IA - inter area, iA - intra area, L1 - IS-IS level-1, L2 - IS-IS level-2 N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2 RTI - Learnt from another routing-instance + - Active Route Prot Type Dest Address/Mask Next-hop Age Interface name ---- ---- ----------------- -------- --- -------------- BGP N/A +0.0.0.0/0 10.1.224.103 1d08h01m Indirect BGP N/A 0.0.0.0/0 169.254.0.2 1d07h50m tvi-0/603.0
All traffic destines to Amazon and Facebook take the SD-WAN Gateway at Hub-2 to reach the application.
admin@T3-Spoke-1-cli> show orgs org Tenant-3 sessions sdwan brief VSN VSN SESS SOURCE DESTINATION TX ID VID ID SOURCE IP DESTINATION IP PORT PORT PROTOCOL NATTED SDWAN APPLICATION RX WAN CKT TX WAN CKT BRANCH ------------------------------------------------------------------------------------------------------------------------------------------------------------- 0 2 12567 10.10.30.30 176.32.103.205 50098 80 6 No Yes amazon MPLS:MPLS MPLS:MPLS T3-Hub-2 0 2 12568 10.10.30.30 176.32.103.205 45608 443 6 No Yes amazon Internet:Internet Internet:Internet T3-Hub-2 0 2 12569 10.10.30.30 176.32.103.205 45610 443 6 No Yes amazon MPLS:MPLS MPLS:MPLS T3-Hub-2 0 2 12576 10.10.30.30 13.32.36.24 43730 443 6 No Yes amazon Internet:Internet Internet:Internet T3-Hub-2 0 2 12597 10.10.30.30 104.115.92.65 39886 443 6 No Yes amazon MPLS:MPLS MPLS:MPLS T3-Hub-2 0 2 12598 10.10.30.30 104.115.92.65 39888 443 6 No Yes amazon Internet:Internet Internet:Internet T3-Hub-2 0 2 12599 10.10.30.30 104.115.92.65 39890 443 6 No Yes amazon MPLS:MPLS MPLS:MPLS T3-Hub-2 0 2 12616 10.10.30.30 104.115.92.65 39906 443 6 No Yes amazon Internet:Internet Internet:Internet T3-Hub-2 0 2 12617 10.10.30.30 104.115.92.65 39908 443 6 No Yes amazon MPLS:MPLS MPLS:MPLS T3-Hub-2 0 2 12628 10.10.30.30 157.240.16.20 49240 443 6 No Yes facebook Internet:Internet Internet:Internet T3-Hub-2 0 2 12629 10.10.30.30 157.240.16.20 49242 443 6 No Yes facebook MPLS:MPLS MPLS:MPLS T3-Hub-2 0 2 12630 10.10.30.30 157.240.16.20 49244 443 6 No Yes facebook Internet:Internet Internet:Internet T3-Hub-2 0 2 12631 10.10.30.30 157.240.16.20 49246 443 6 No Yes facebook MPLS:MPLS MPLS:MPLS T3-Hub-2 0 2 12632 10.10.30.30 157.240.16.20 49248 443 6 No Yes facebook Internet:Internet Internet:Internet T3-Hub-2 0 2 12633 10.10.30.30 157.240.16.20 49250 443 6 No Yes facebook MPLS:MPLS MPLS:MPLS T3-Hub-2
The traffic for Microsoft and Twitter continues as is via the local DIA.
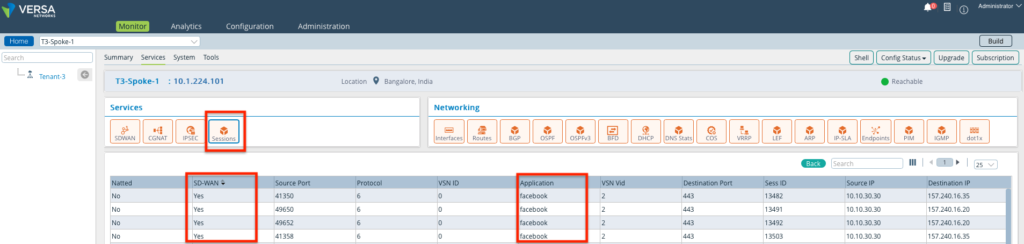
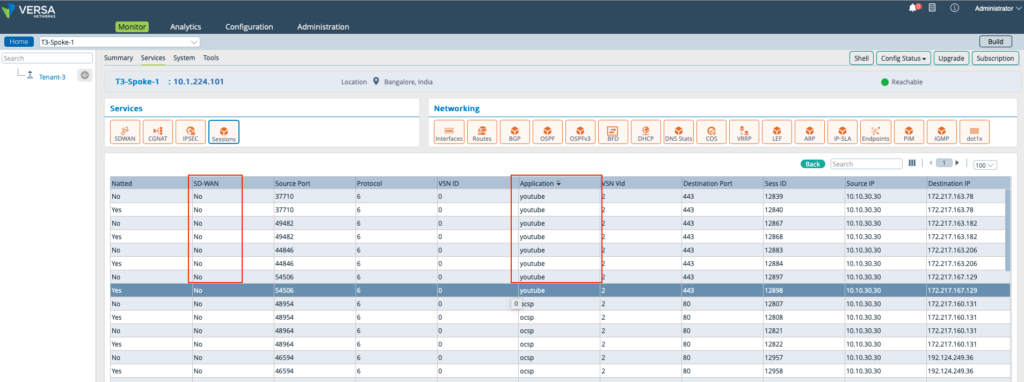
Traffic logs on the Monitor Tab
Near Real time traffic can be monitored using the Monitor feature on the Director. This show traffic sessions for Facebook which are considered as SDWAN and that for Microsoft considered as non-SDWAN DIA traffic.
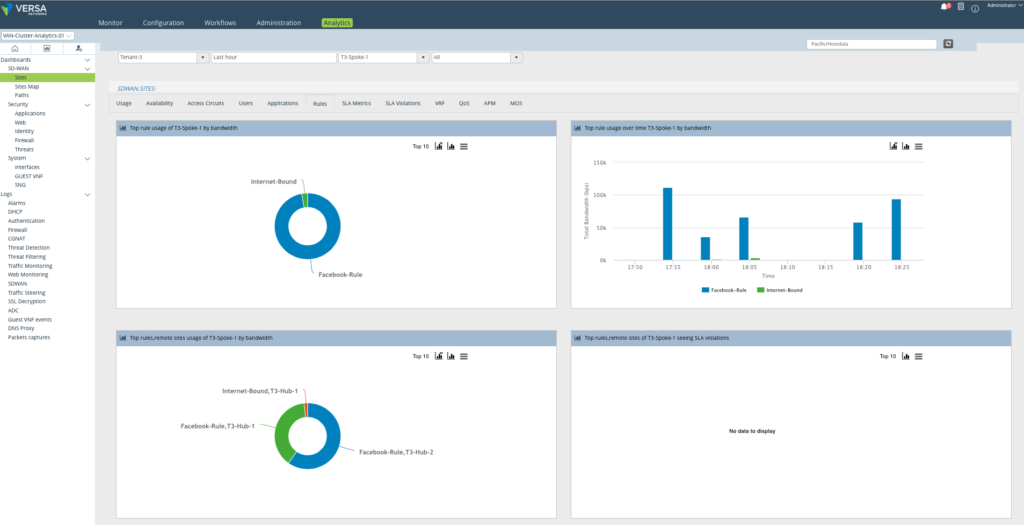
Analytics Logs
Big Data Analytics shows the Rules which match the traffic of interest. The remote usage of sites shows the volume of traffic going via each of the Hubs mapped against the Rules.
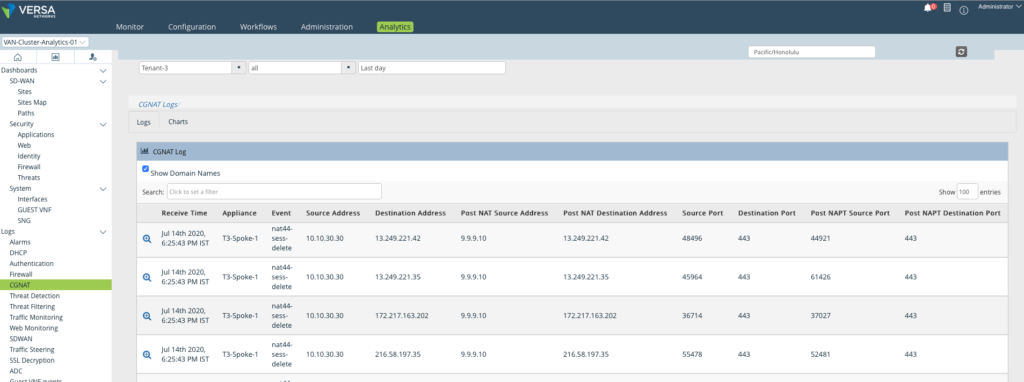
The analytics logs confirms that the Traffic going to Internet getting NATTED as it goes out via the Local break out.
Summary
This document explained the feature of Application Based Traffic forwarding over secure SD-WAN Gateways. While creating these Policies, we can tie with Traffic Engineering by creating SLA profiles to automatically remove or switch to alternate Gateway in case of degradation in link quality. This gives the enterprise more control over the policy and gives best user experience and application performance.

