Security – Configure SSL Inspection

SSL Inspection
SSL / TLS Inspection is the process where the SSL / TLS encrypted traffic is intercepted between a client and server machine. This interception can be initiated by either the client towards the server or vice-versa.
Although all traffic send over SSL / TLS is encrypted, there could also be instance where malicious content also gets encrypted and pass on as legitimate traffic thus getting past the security perimeter of the Branch.
“67% of all malware in Q1 2020 as delivered by HTTPS connections”
WatchGuard, June 2020
Versa Secure SD-WAN SSL Inspection is a feature by which the Versa Operating System inspects the SSL certificates for expired or rogue certificates there by protecting the end hosts connected on the LAN.
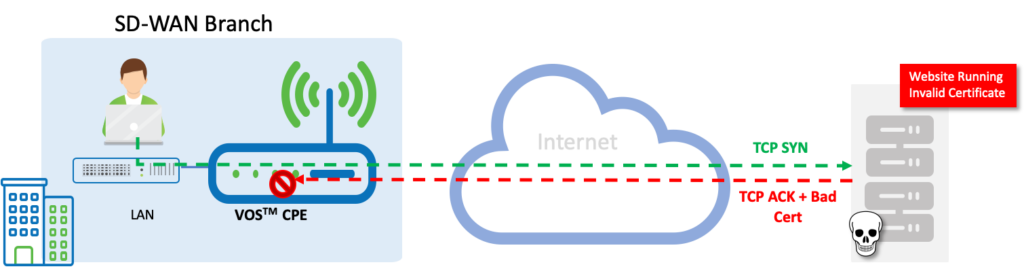
High Level Topology
Here we have a user behind a Versa SD-WAN appliance connected to the Internet and trying to access a web portal that is having invalid/rogue SSL Certificates. The VOS, by inspecting the Server Response and looking deep into the SSL Certificates, detects the anomalies, and instead of forwarding the server response to the end host, the VOS drop/rejects the bad SSL packets and in turn protects the end host.
Configuration
Objectives
A. Generate a Key and Self-Signed Certificate on the Versa appliance. (Customers can choose to use registered certificate in real world)
B. Create a Decryption Profile and associate this into a Decryption Policy to inspect the Traffic.
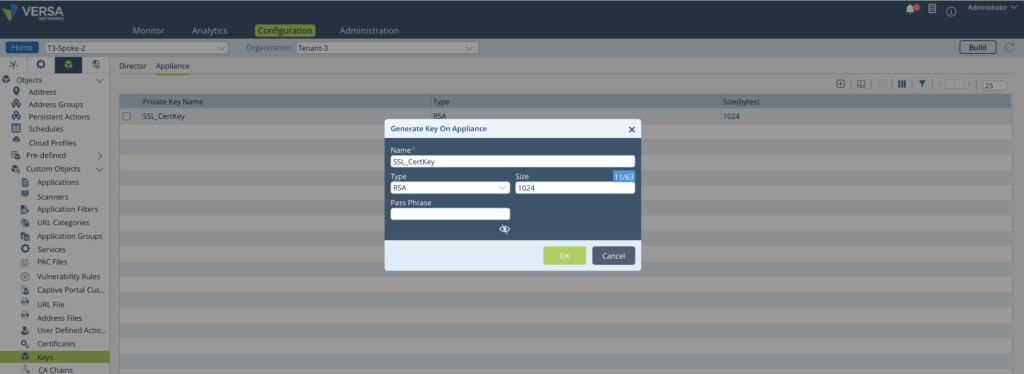
Step 1: Generate a Key in the Appliance Context.
Step 2: Generate a Self Signed Certificate on the Appliance.
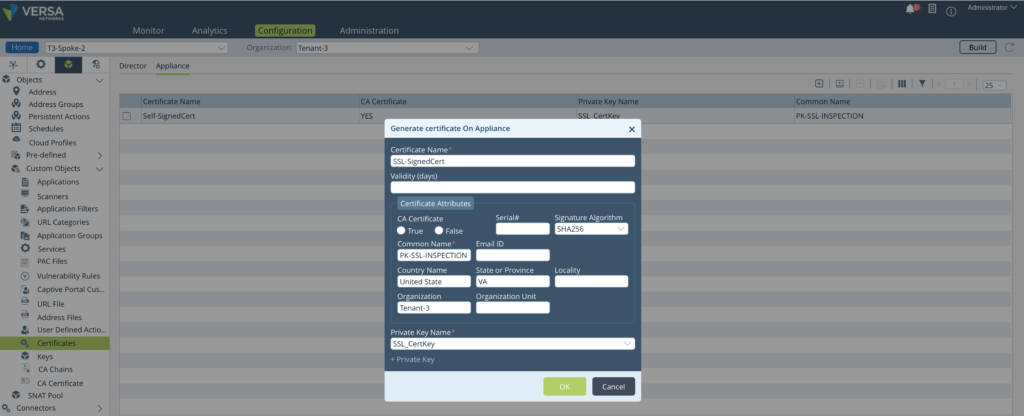
CA certificate ideally is not required for SSL inspection. However, since we are using same profile for inspection and decryption, it is required to create a certificate and attach it.
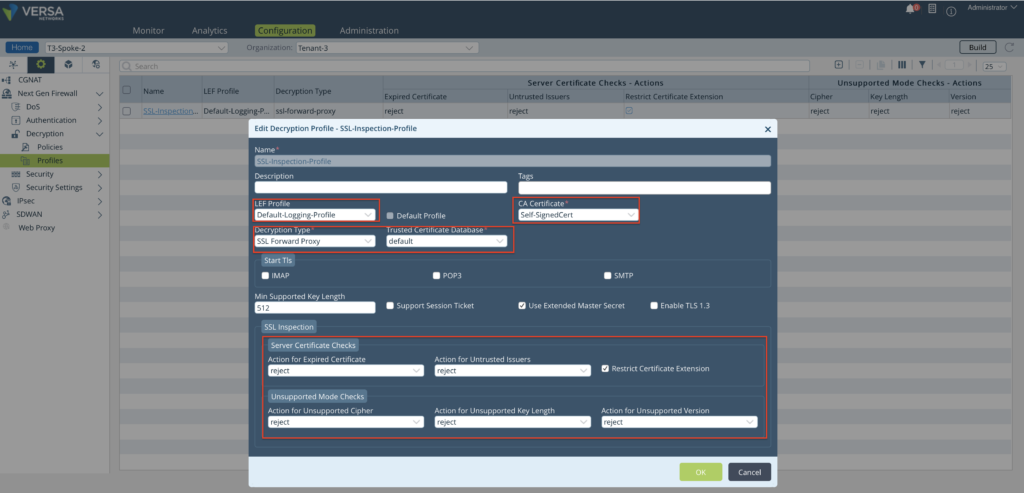
Step 3: Configure a SSL Inspection Profile and map the Self Signed Certificated created above under the CA Certificate in the Profile Choose the Decryption type as 'SSL Forward Proxy' and choose 'reject' for all SSL Certificate Checks.
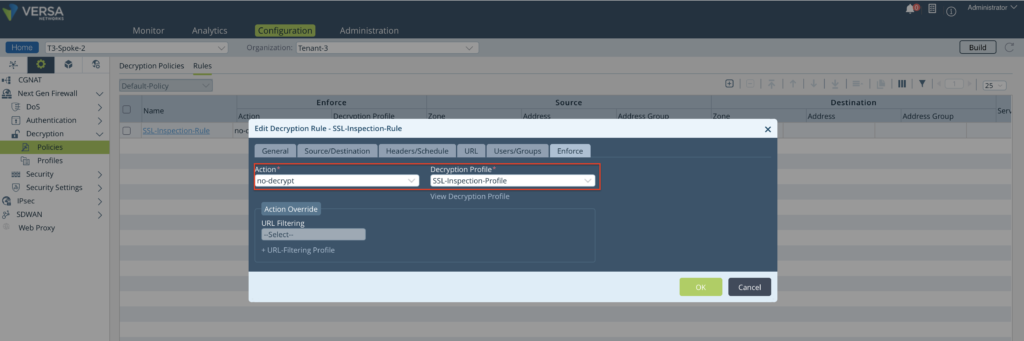
Step 4: Create a Decryption Policy - 'Default Policy' and Create a Rule to match all Traffic going towards Internet. In the Enforce Tab, choose Action as 'no-decrypt' and map the Decryption Profile created earlier.
Verification
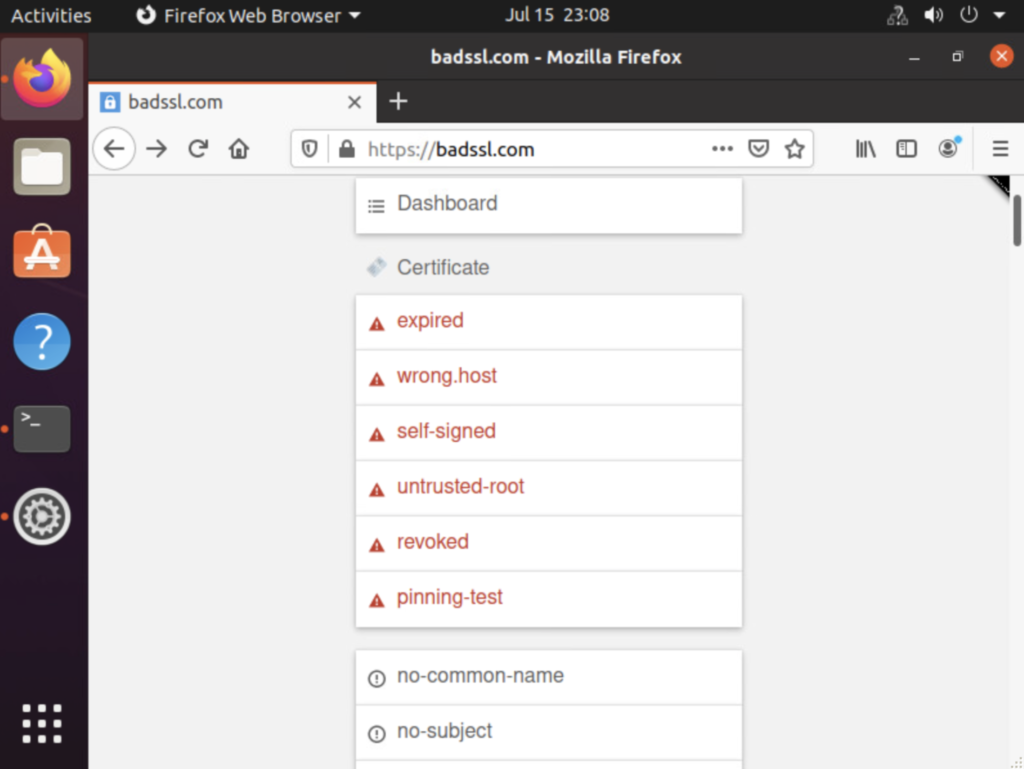
Initiate traffic by visiting the site https://badssl.com
From within the site choose any of the links with the ‘bad ssl’ category defined in it.The site gets blocked and does not open.
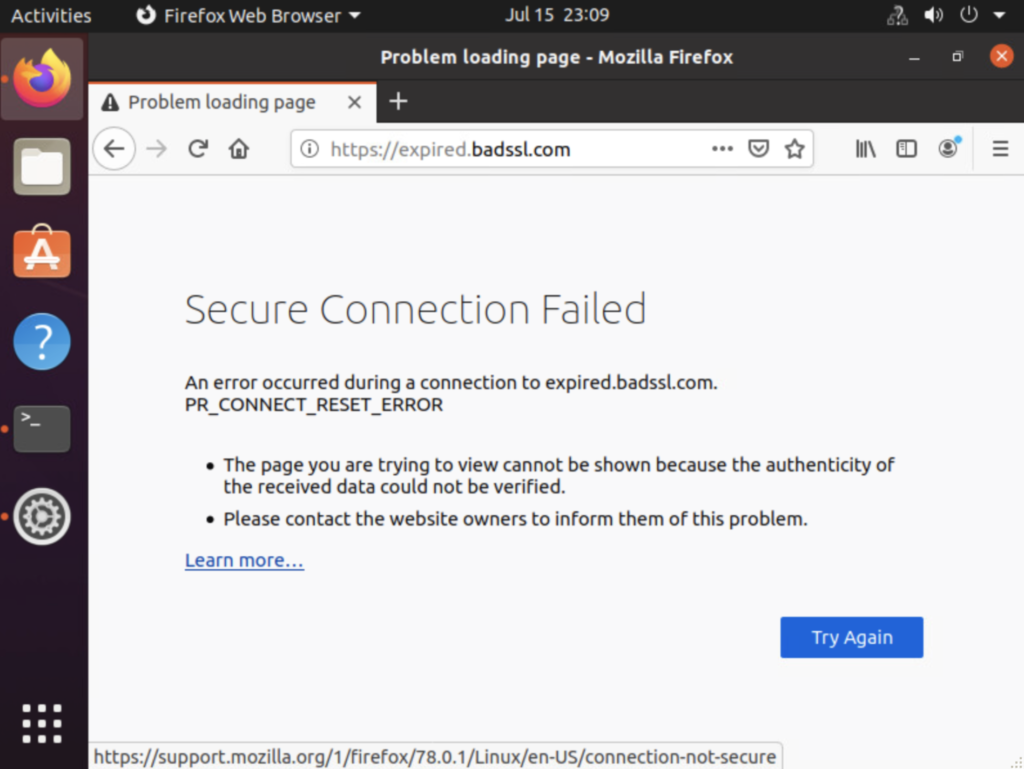
On receiving a bad SSL response from the site, the VOS automatically blocks the traffic.
Logs on CLI and Analytics
From within the CLI, we can observe the hit count on the SSL-Inspection-Rule policy.
admin@T3-Spoke-2-cli> show orgs org-services Tenant-3 security decryption-policies rules decrypt-policy-stats HIT NAME NAME COUNT -------------------------------------------- Default-Policy SSL-Inspection-Rule 182 [ok][2020-07-15 10:47:31] admin@T3-Spoke-2-cli>
On the analytics, the SSL decryption tab shows the SSL Decryption logs. The Action Taken defines if the site TCP sessions have been allowed or rejected and the reason for rejection.
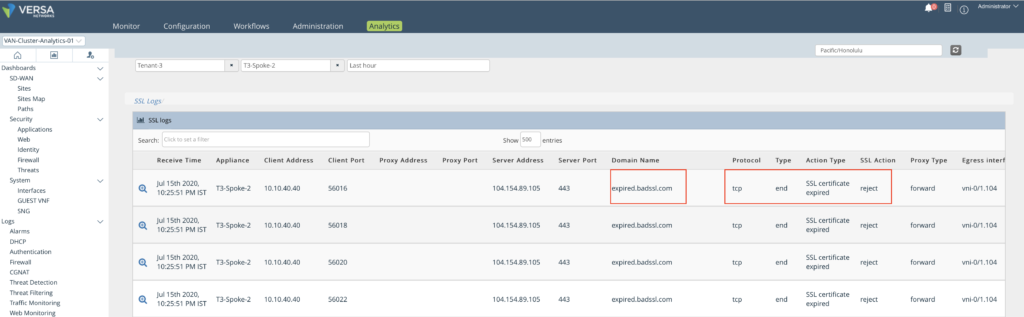
| Jul 15th 2020, 10:25:51 PM IST | 2020-07-15T16:55:51Z sslSessionLog, tenant=Tenant-3, txPkts=13, flowDuration=461, sslProtoVersion=TLS 1.2, toCountry=United States, fromZone=Intf-Spoke-LAN-Zone, policyAction=nodecrypt, sslAction=reject, eventType=end, toLatLon=38.0,-97.0, sessLenBkt=0, clientPort=56016, domainName=expired.badssl.com, serverAddr=104.154.89.105, destAddr=104.154.89.105, rcvTimeSec=51, rxPkts=12, srcAddr=10.10.40.40, applianceName=T3-Spoke-2, proxyType=forward, protocolId=6, flowKey=0x5f0f350201000200009d, certIsSelfSigned=0, toGeoHash=9yg00t, txBytes=1129, rxBytes=5320, cipher=TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256, fromUser=Unknown, decryptProfileName=SSL-Inspection-Profile, serverPort=443, clientAddr=10.10.40.40, at=Wed Jul 22 10:00:00 PDT 2020, egrIf=vni-0/1.104, policyRuleName=SSL-Inspection-Rule, ingIf=vni-0/2.0, actionType=SSL certificate expired, publicKeyLen=2048, toZone=Intf-Internet-Zone |
| Jul 15th 2020, 10:32:41 PM IST | 2020-07-15T17:02:41Z sslSessionLog, tenant=Tenant-3, txPkts=7, flowDuration=467, sslProtoVersion=TLS 1.2, toCountry=United States, fromZone=Intf-Spoke-LAN-Zone, policyAction=nodecrypt, sslAction=reject, eventType=end, toLatLon=38.0,-97.0, sessLenBkt=0, clientPort=56172, domainName=self-signed.badssl.com, serverAddr=104.154.89.105, destAddr=104.154.89.105, rcvTimeSec=41, rxPkts=6, srcAddr=10.10.40.40, applianceName=T3-Spoke-2, proxyType=forward, protocolId=6, flowKey=0x5f0f36a001000200012d, certIsSelfSigned=1, toGeoHash=9yg00t, txBytes=853, rxBytes=1624, cipher=TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256, fromUser=Unknown, decryptProfileName=SSL-Inspection-Profile, serverPort=443, clientAddr=10.10.40.40, at=Wed Jul 22 11:00:00 PDT 2020, egrIf=vni-0/1.104, policyRuleName=SSL-Inspection-Rule, ingIf=vni-0/2.0, actionType=SSL untrusted issuer, publicKeyLen=2048, toZone=Intf-Internet-Zone |
Summary
This article explained the configuration behind SSL-Inspection and how it can be used to secure the Hosts behind a Versa Secure SD-WAN.

