Configure DDOS Protection

Securing against DDOS Attacks
DDOS attack is a malicious attempt to disrupt normal network services of an end machine which could be a Server, service, or the network itself by flooding the infrastructure with a flood of traffic using single or multiple sources. This is a very prevalent form of compromising systems that are connected to the Internet and results in the network or resources being unavailable for its intended use and/or users. DDOS attacks typically include port scans, flooding the network with TCP, ICMP probes, host sweeping and attacks involving high volumes of small packets.
Versa Secure SD-WAN DDOS Protections provides more granular control and configuration for the prevention of such attacks using policies that can be defined based on Zones, Source, and destination IP addresses, IP headers and TCP & UDP services.
Versa Secure SD-WAN gives the user the flexibility to define both ‘Aggregate’ and ‘Classified’ DDOS Profiles.
Aggregate DDOS Profile monitors the threshold for all the traffic for various protocols that match the rules defined in the DDOS Policy – typically used to defend attacks targeting an entire subnet and the source also spread across a wide range of IP addresses.
Classified DDOS Profile instead does the same on per source and per-destination IP address basis. The rate at which packets are received is tracked per-protocol, per-source-and-destination-IP-address. You use classified DDoS profiles to defend against DDoS attacks targeted against specific endpoint hosts, based on the destination IP address or to narrow down the source of the DDoS traffic to a few source IP addresses.
Versa SD-WAN DDOS Protection is a part of the Stateful Firewall feature and an appropriate subscription has to be selected.
DDOS Protection configuration has two components. They are –
| DDOS Profile | • Define criteria for the type of Profile – Aggregate or Classified • Define the Flood Protection Thresholds specific for each Protocol, rate limit thresholds and drop period in case of a breach • Action to be taken when the active rate threshold is breached – Random Early Drops – Randomly Drop Packets – SYN Cookies – Generate an acknowledgment and ensure connection from dropping during SYN flood attack. This is the Default. |
| DDOS Policy | This is used to match a certain type of traffic based on IP headers, port numbers, services and the action to be taken – Allow, Deny or Protect and match the DOS Profile created |
High Level Topology
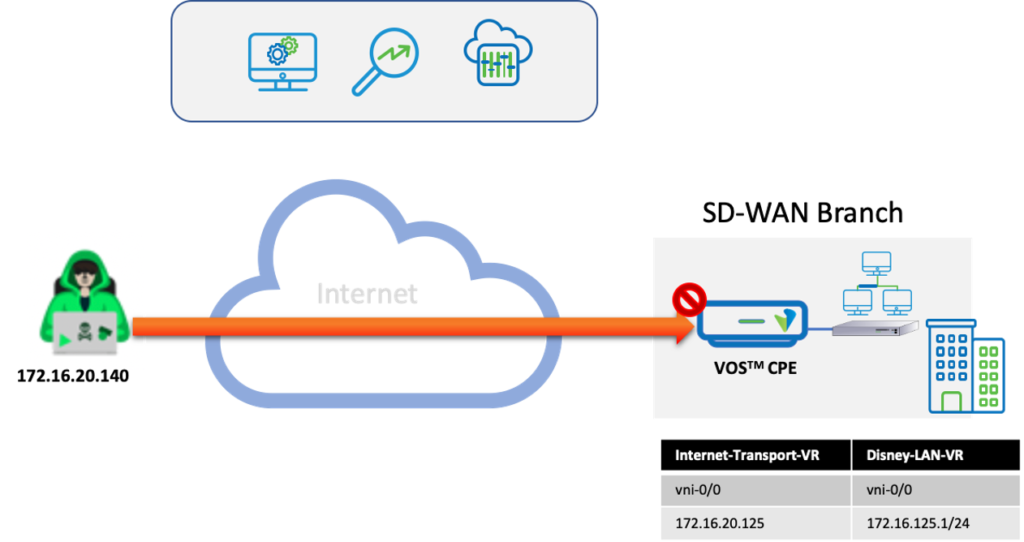
The topology has a Versa SD-WAN CPE implemented at a Branch having DIA. A remote attacker is generating malicious traffic towards the LAN from the Internet. The DDOS Security policy implemented on the Versa CPE blocks this attack.
Configuration
Objectives:
A. Configure an Aggregated DDOS Policy coming from the Internet towards a LAN subnet or endpoint
B. Generate traffic from an external source to simulate a TCP SYN flood attack. The system should identify and drop the traffic.
Step 1: DDOS Profile Configuration. Choose the type of Profile. Enable and configure the Flood Protection Policies.
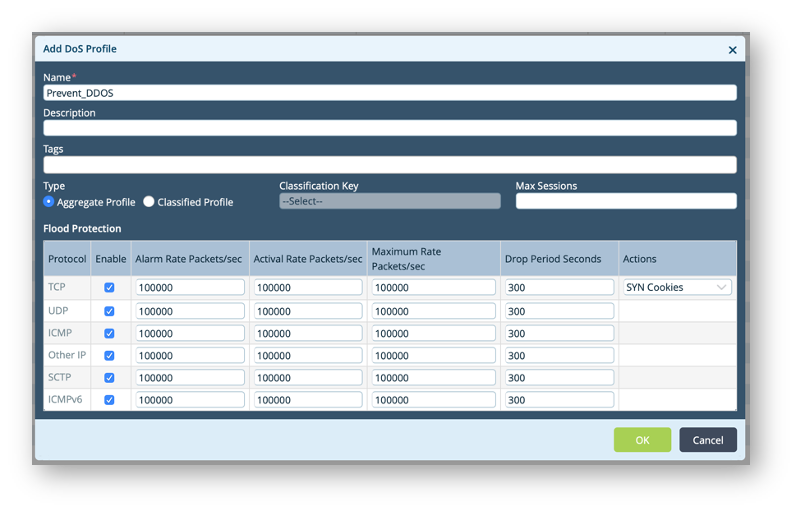
| Alarm Rate | Defines the threshold rate at which a DoS alarm has to be triggered (in packets per second) |
| Active Rate | Defines the threshold rate at which to activate a DoS response (in packets per second) |
| Maximal Rate | Defines the threshold rate of incoming packets (in packets per second) above which packets are dropped. For aggregate profile, it applies to all traffic processed by the DoS protection rule For classified profile, it applies to the classified traffic define in the DoS protection rule |
| Drop Period | Duration in Seconds, for which the packets are dropped. Traffic dropped during this period is not considered while triggering an alert. |
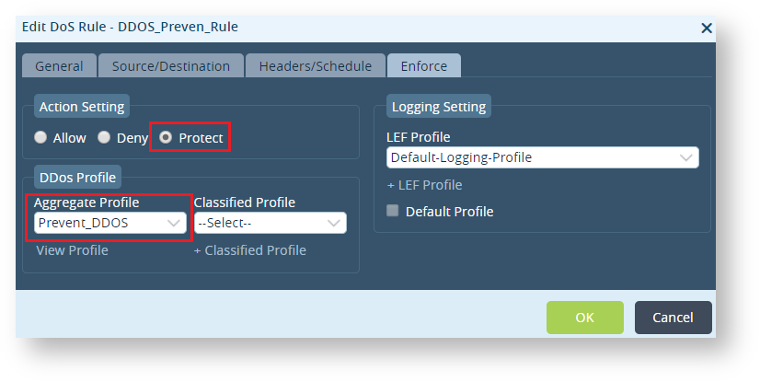
Step 2 : Configure a DOS Policy “DDOS_Policy”
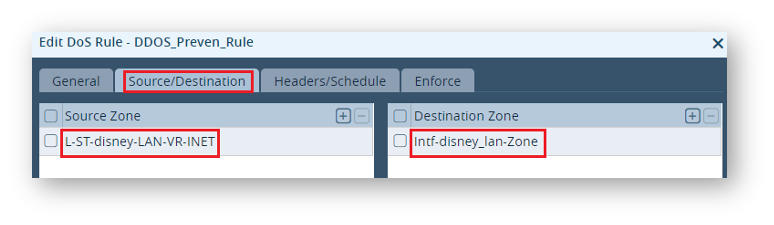
– Create a rule “DDOS_Preven_Rule”
– Define the source and destination zone – The Source zone has to be DIA, LAN side split tunnel and destination zone would be the respective LAN Zone.
– Choose to “Protect” against the DDOS attack and map the aggregate profile “Prevent_DDOS” to this Rule.
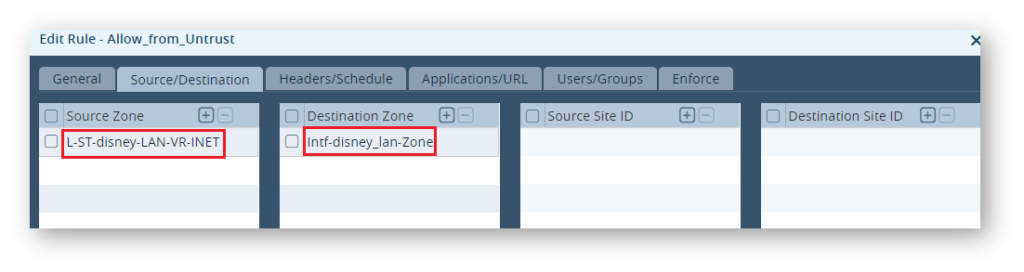
Step 3: Configure Firewall Policy “Allow_from_Untrust” to allow traffic coming from outside (Internet) towards the LAN.
Step 6: Traffic is initiated from Internet towards this LAN using packet flooding tools like hping, fping etc.
Verification
When there is a flood attack hitting the LAN from the Internet in this case, the Versa SD-WAN CPE automatically detects and drops the traffic. This can be verified using the Monitor Tab, Analytics, and the CLI.
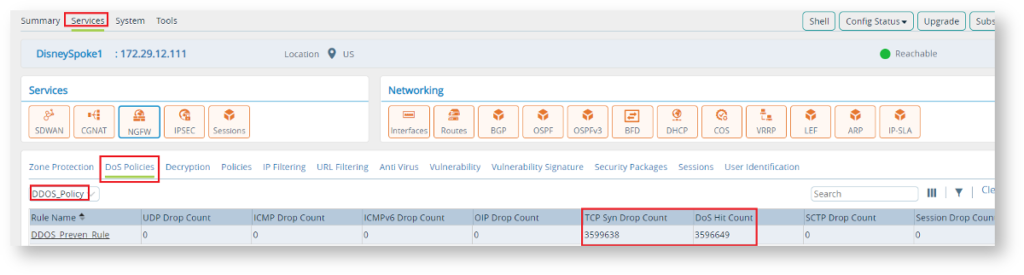
The Monitor Tab shows the near real-time traffic and hit count on the policy. The Drop count confirms the behavior of DDOS protection.
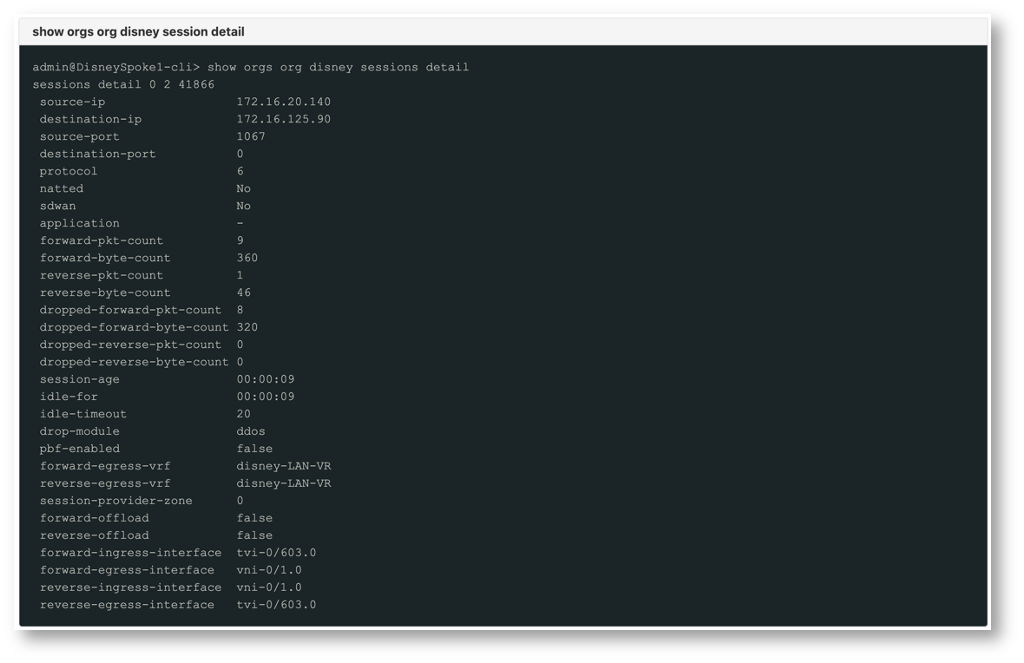
The cli output also confirms the same behaviour by identifying the “drop-module” as “ddos”
Logs on Analytics indicates the DDOS Protection in action
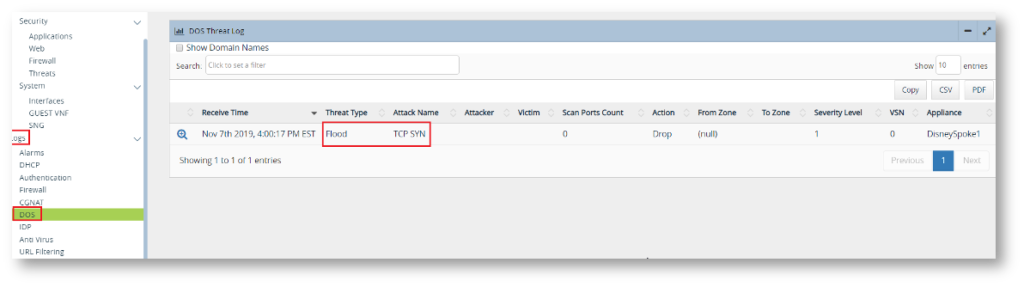
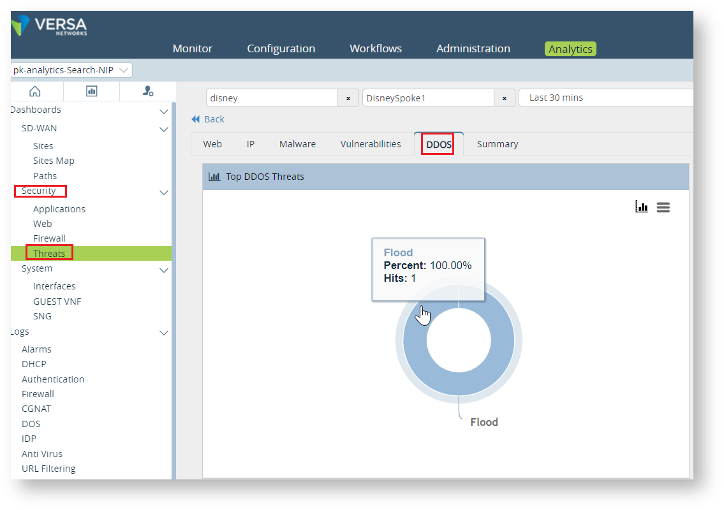
The Security > Threat tab on Analytics also show the DDOS attack
Summary
This document explained in brief about enabling DDOS Protection in an SD-WAN Branch using the aggregate Profile. While creating the Profile, the use of classified profiles gives more insights into the details of the attacker and victim. In addition, other features like schedulers, services including custom services can also be combined and mapped to a DOS profile to give the users more control over the type of Protection.

